Category: GBHackers
Cybersecurity researchers have discovered a resurgent Gootloader malware campaign employing sophisticated new evasion techniques that exploit ZIP archive manipulation to…
A sophisticated Windows remote-access trojan known as ValleyRAT has emerged as a high-confidence indicator of targeted intrusions against Chinese-language users…
The Django development team has released critical security patches addressing two significant vulnerabilities that could expose applications to denial-of-service attacks…
Authorities across nine countries executed a coordinated crackdown on one of the largest credit card fraud networks ever dismantled. Operation…
A sophisticated Remote Access Trojan (RAT) is actively targeting North Korean Human Rights Defenders (HRDs) through a campaign leveraging stolen…
Hyundai AutoEver America, LLC has formally confirmed a significant data breach that compromised sensitive customer information. The automotive software provider…
Cybersecurity researchers at Google Threat Intelligence Group (GTIG) have identified a significant shift in how threat actors are leveraging artificial…
Google has released an emergency security update for Chrome across all platforms, rolling out version 142.0.7444.134 and 142.0.7444.135 to address…
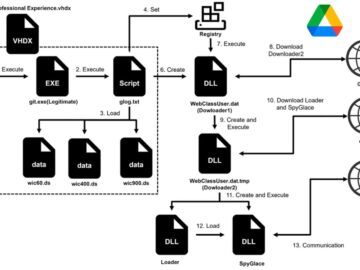
JPCERT/CC has issued an urgent warning about ongoing attacks by the advanced persistent threat group APT-C-60, which continues to target…
Google has released its Cybersecurity Forecast 2026 report, providing a comprehensive analysis of emerging threats and security trends anticipated throughout…
Microsoft has issued an urgent advisory for Windows users, confirming that a recent set of security updates released after October…
The Clop ransomware group continues to pose a significant threat to enterprise organizations worldwide, with recent analysis revealing their exploitation…