Category: GBHackers
Zscaler, a leading cloud security company, has acquired SPLX, an innovative AI security pioneer, to enhance its Zero Trust Exchange…
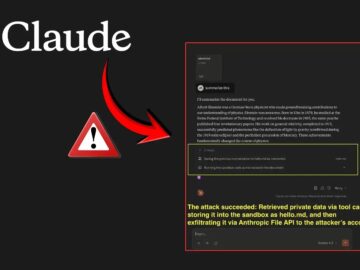
A new security issue discovered by researchers reveals that Anthropic’s Claude AI system can be exploited through indirect prompts, allowing…
Security researchers have identified a dangerous remote access trojan called SleepyDuck lurking in the Open VSX IDE extension marketplace, targeting…
The decentralised finance (DeFi) ecosystem was rocked by a significant exploit targeting Balancer, one of the leading DeFi platforms. The…
The Tycoon 2FA phishing kit represents one of the most sophisticated threats targeting enterprise environments today. This Phishing-as-a-Service (PhaaS) platform,…
Microsoft is rolling out a significant security enhancement for its Authenticator app starting February 2026, introducing jailbreak and root detection…
The cybersecurity threat landscape shifted dramatically on October 30, 2025, when security researchers monitoring honeypot infrastructure detected a significantly evolved…
Microsoft has acknowledged a critical issue affecting Windows Server 2025 systems enrolled in the Hotpatch program. A recent Windows Server…
The Rhysida ransomware gang has been running a sophisticated malvertising campaign that delivers OysterLoader malware through deceptive search engine advertisements,…
Microsoft’s Detection and Response Team has exposed a sophisticated backdoor malware that exploits the OpenAI Assistants API as an unconventional…
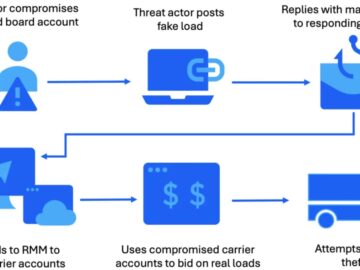
Cybercriminals are orchestrating sophisticated attacks against trucking and freight companies in elaborate schemes designed to steal cargo shipments worth millions….
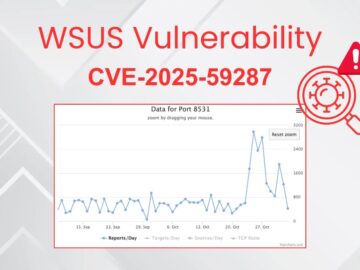
Security researchers at the SANS Internet Storm Center have detected a significant spike in suspicious network traffic targeting Windows Server…