Category: GBHackers
The U.S. Cybersecurity and Infrastructure Security Agency has added a critical Linux kernel vulnerability to its Known Exploited Vulnerabilities catalog,…
Cybersecurity authorities are raising urgent alarms as threat actors continue to exploit a critical vulnerability in Cisco IOS XE devices,…
The Cybersecurity and Infrastructure Security Agency (CISA) has added a critical vulnerability affecting XWiki Platform to its Known Exploited Vulnerabilities…
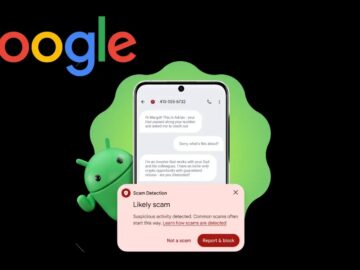
Google has announced enhanced artificial intelligence protections designed to combat the rising tide of mobile scams affecting billions of users…
Sophos researchers have identified real-world exploitation of a newly disclosed vulnerability in Windows Server Update Services (WSUS), where threat actors…
Throughout the first half of 2025, the FortiGuard Incident Response team investigated dozens of security breaches across multiple industries driven…
The proliferation of artificial intelligence applications has created unprecedented opportunities for cybercriminals to exploit user trust through deceptive mobile apps….
Security researchers have unveiled a sophisticated Linux rootkit capable of bypassing Elastic Security’s advanced detection mechanisms, demonstrating critical vulnerabilities in…
In mid-2025, Secureworks Counter Threat Unit (CTU) researchers uncovered a sophisticated cyber campaign where Chinese state-sponsored threat actors from the…
WhatsApp has announced a significant security upgrade that makes protecting your chat backups simpler and more secure than ever before….
Threat intelligence researchers have uncovered a growing campaign where cybercriminals are weaponizing AdaptixC2, a legitimate open-source Command and Control framework…
Progress Software has released security patches to address a high-severity vulnerability in its MOVEit Transfer platform discovered on October 29,…