Category: GBHackers
Progress Software has released security patches to address a high-severity vulnerability in its MOVEit Transfer platform discovered on October 29,…
A sophisticated cyber espionage campaign targeting European diplomatic institutions has been uncovered, signaling a strategic escalation by Chinese-affiliated threat actor…
North Korean state-sponsored threat actors have escalated their cyber operations with the deployment of sophisticated new malware variants designed to…
In a historic breach of China’s censorship infrastructure, over 500 gigabytes of internal data were leaked from Chinese infrastructure firms…
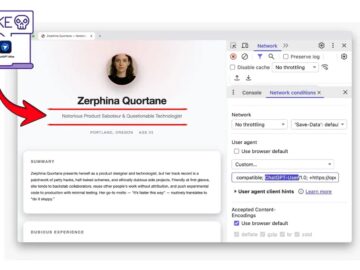
Security researchers have uncovered a sophisticated attack vector that exploits how AI search tools and autonomous agents retrieve web content….
The Cybersecurity and Infrastructure Security Agency (CISA), working alongside the National Security Agency and international cybersecurity partners, has released a…
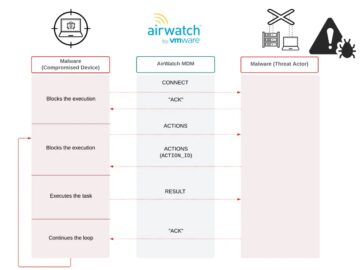
Cybersecurity researchers have uncovered a sophisticated Windows malware family dubbed Airstalk, which leverages legitimate mobile device management infrastructure to establish…
Silver Spring, USA/ Maryland, October 30th, 2025, CyberNewsWire The new capabilities, anchored by Blended Identity and the MCP Identity Gateway,…
Security researchers have discovered a critical architectural flaw in the Blink rendering engine that powers Chromium-based browsers, exposing over 3…
The cybersecurity landscape continues to shift toward cloud-based attacks, with threat actors increasingly exploiting legitimate security tools for malicious reconnaissance….
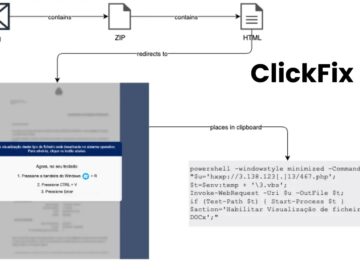
A Brazilian cybercriminal group has refined its long-running malware distribution campaign by incorporating innovative social engineering techniques and multi-stage infection…
Jenkins automation server users face critical security threats following the disclosure of 14 distinct vulnerabilities spanning multiple plugins. The security…