Category: GBHackers
Google has released Chrome version 142 to the stable channel, addressing multiple critical security vulnerabilities that could allow attackers to…
A sophisticated cybercrime campaign leveraging Near Field Communication technology has exploded across multiple continents, with researchers at zLabs identifying over…
A critical security vulnerability in Redis’s Lua scripting engine has left thousands of database instances vulnerable to remote code execution…
Microsoft has addressed a critical privilege escalation vulnerability affecting Windows environments worldwide. Attackers can exploit misconfigured Service Principal Names (SPNs)…
Microsoft addressed a critical race condition vulnerability affecting its Windows Cloud Files Minifilter driver in October 2025. The flaw, assigned…
A sophisticated malware campaign is actively targeting WordPress e-commerce websites using the WooCommerce plugin, according to recent findings from the…
The VSCode extension marketplace has become a critical vulnerability in the software supply chain. Security researchers at HelixGuard Team recently…
A critical security flaw has been discovered in the Anti-Malware Security and Brute-Force Firewall WordPress plugin, putting more than 100,000…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning about active exploitation of a critical vulnerability affecting…
The global developer community has been rocked by the emergence of PhantomRaven, a far-reaching campaign involving 126 malicious npm packages…
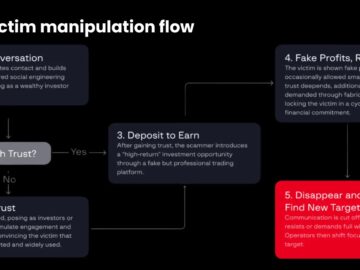
Fraudulent investment platforms impersonating legitimate cryptocurrency and forex exchanges have emerged as the primary financial threat across Asia, with organized…
Microsoft experienced a widespread service outage on Wednesday, October 29, 2025, affecting its Azure cloud platform and Microsoft 365 suite,…