Category: GBHackers
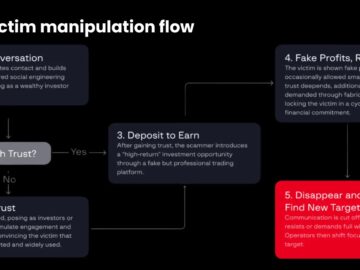
Fraudulent investment platforms impersonating legitimate cryptocurrency and forex exchanges have emerged as the primary financial threat across Asia, with organized…
Microsoft experienced a widespread service outage on Wednesday, October 29, 2025, affecting its Azure cloud platform and Microsoft 365 suite,…
A critical vulnerability discovered in Google Messages for Wear OS has exposed millions of smartwatch users to a significant security…
Tel Aviv, Israel, October 29th, 2025, CyberNewsWire Sweet Security Brings Runtime-CNAPP Power to Windows Sweet Security, a leader in Runtime…
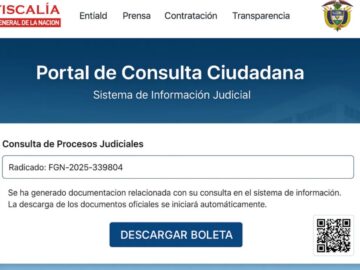
The campaign leverages judicial document themes to distribute Hijackloader malware, which subsequently deploys PureHVNC remote access trojan (RAT)—marking the first…
Google has released comprehensive guidance on protecting privileged accounts, recognizing that stolen credentials have become one of the most dangerous…
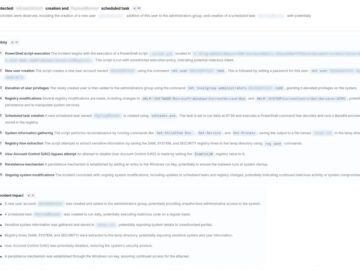
Russian-linked attackers have intensified their targeting of Ukrainian organizations through sophisticated intrusions that rely heavily on legitimate Windows tools rather…
A critical security vulnerability was discovered when a complete 4-terabyte SQL Server backup belonging to Ernst & Young (EY), one…
Threat intelligence researchers have identified a new ransomware-as-a-service (RaaS) operation called The Gentlemen’s RaaS, being actively recruited on underground hacking…
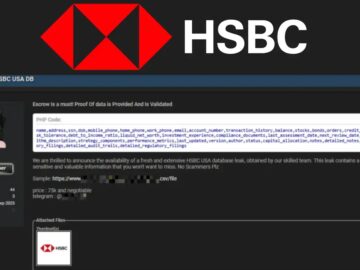
A threat actor has claimed responsibility for breaching HSBC USA, the American division of the global investment bank and financial…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical security alert regarding two severe vulnerabilities discovered in Dassault…
Tata Motors, India’s largest automaker and a major player in the global automotive industry, suffered a catastrophic data exposure that…