Category: GBHackers
Industrial control systems (ICS) continue to face increasing cybersecurity challenges as threat actors employ sophisticated malicious scripts and phishing campaigns…
A sophisticated malware campaign is targeting Mac users through fraudulent GitHub repositories that masquerade as legitimate software downloads, with threat…
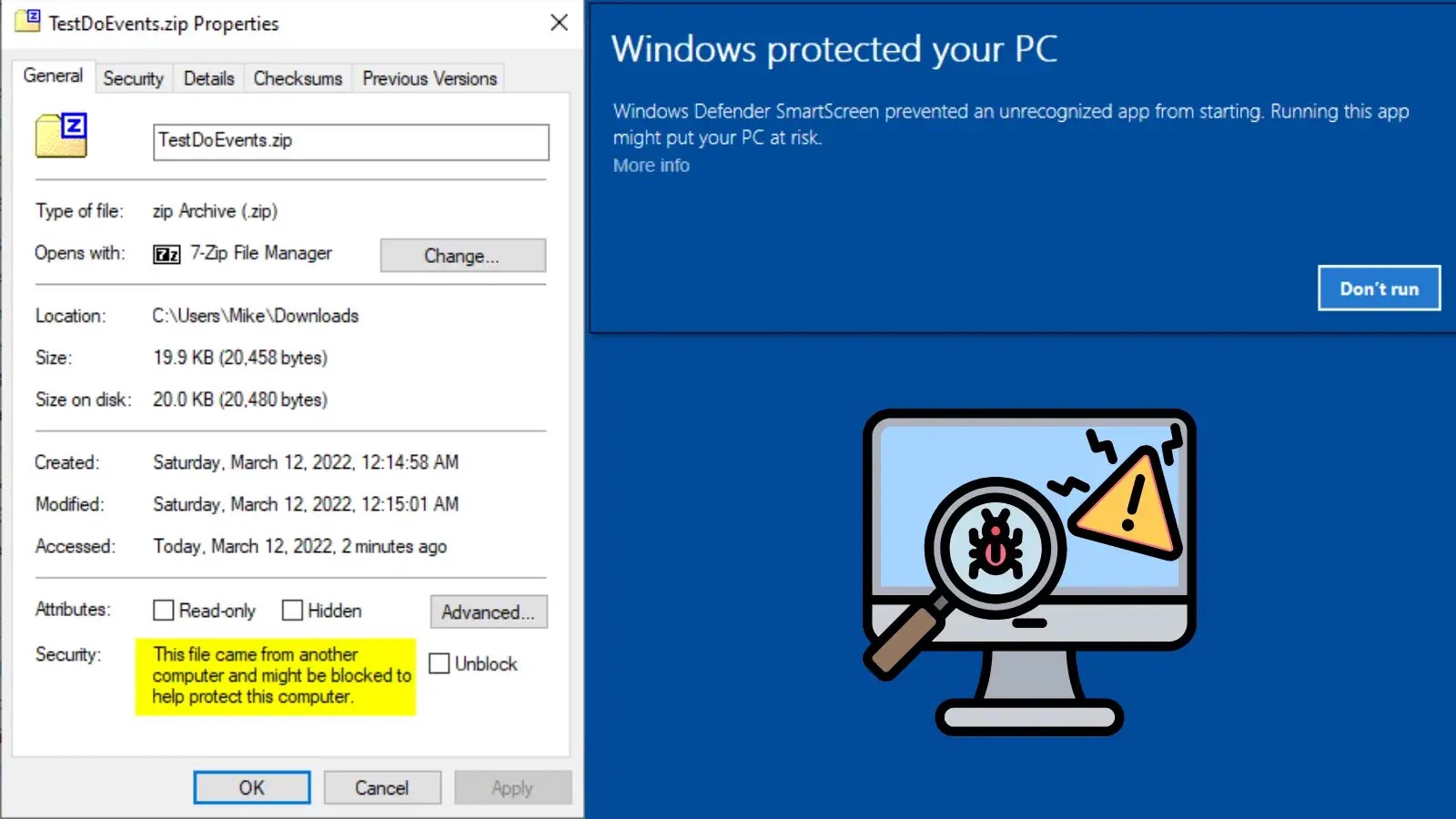
A sophisticated attack technique called LNK Stomping is enabling cybercriminals to bypass Windows security protections designed to block malicious files downloaded from…
Cybersecurity researchers have identified a concerning development in the underground cybercrime marketplace: a sophisticated Remote Access Trojan (RAT) being marketed…
A groundbreaking discovery in cybersecurity research has revealed the emergence of ‘MalTerminal’, potentially the earliest known example of Large Language Model…
Cybersecurity researchers have uncovered a sophisticated Russian botnet operation that leveraged DNS misconfigurations and compromised MikroTik routers to deliver malware…
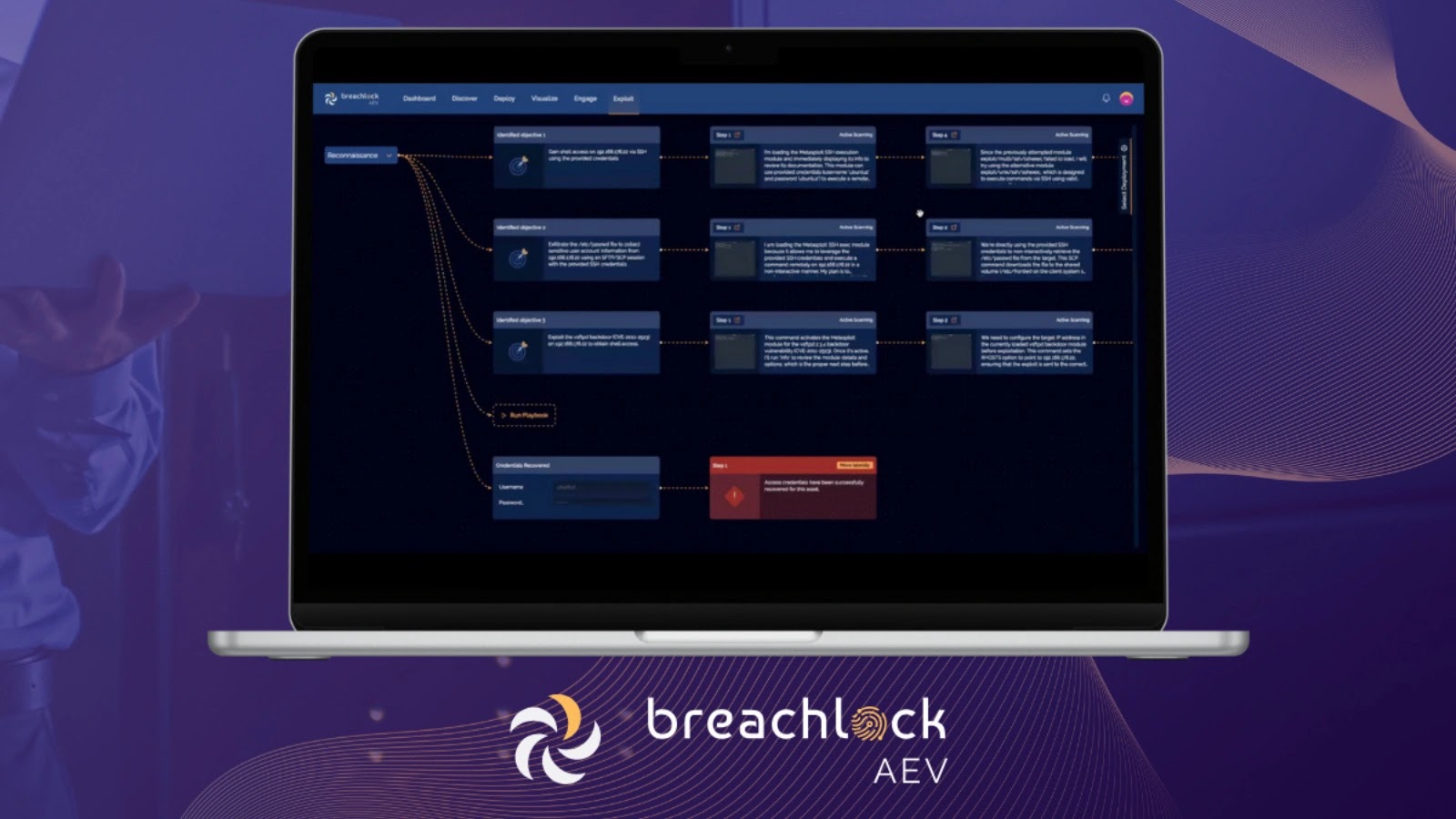
New York, New York, September 19th, 2025, CyberNewsWire BreachLock, the global leader in offensive security, has been recognized as a…
A newly discovered video injection tool for iOS devices that have been jailbroken poses a serious threat to modern digital…
Since January, Trend Micro has tracked a surge in phishing campaigns using AI-powered platforms (Lovable, Netlify, Vercel) to host fake…
A critical security vulnerability has been discovered in HubSpot’s Jinjava template engine, potentially exposing thousands of websites and applications to…
On September 18, 2025, Orange Cert publicly disclosed a critical authentication bypass vulnerability affecting Nokia’s CBIS (CloudBand Infrastructure Software) and…
Luxury jeweler Tiffany and Company has confirmed a data breach that exposed the personal information of 2,590 customers. The company discovered…