Category: HackRead
The Internet Archive (Archive.org) suffered a second security breach in October 2024, exposing support tickets through unrotated Zendesk API tokens….
A hacker known as “TAINTU” is advertising a “Top Secret U.S. Space Force Military Technology Archive” for sale, allegedly containing…
Researchers at Microsoft discovered a new macOS vulnerability, “HM Surf” (CVE-2024-44133), which bypasses TCC protections, allowing unauthorized access to sensitive…
A new Gorilla Botnet has launched massive DDoS attacks, targeting over 100 countries, according to cybersecurity firm NSFOCUS. This botnet,…
Hackers impersonate ESET in phishing attacks targeting Israeli organizations. Malicious emails, claiming to be from ESET, deliver wiper malware. Security…
Iranian hackers are targeting critical infrastructure organizations with brute force tactics. This article explores their techniques, including MFA push bombing…
North Korean hackers are infiltrating Western companies using fraudulent IT workers to steal sensitive data and extort ransom. Learn how…
The app market is saturated with over 7 million apps across major stores. Analytics mobile apps have become essential for…
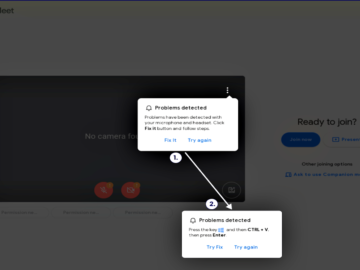
Protect yourself from the ClickFix attack! Learn how cybercriminals are using fake Google Meet pages to trick users into downloading…
Brazilian police have arrested the hacker known as USDoD, responsible for high-profile breaches including the FBI’s InfraGard and National Public…
The US DoJ indicts two Sudanese nationals allegedly behind Anonymous Sudan for over 35,000 DDoS attacks targeting critical infrastructure, hospitals,…
North Korean hackers target Linux-based payment switches with new FASTCash malware, enabling ATM cashouts. Secure your financial infrastructure and protect…