Category: HackRead
Security questionnaires serve as essential tools for building connections and trust in the digital realm. They help in identifying potential…
Cybersecurity researchers at third-party risk management firm UpGuard have identified a vulnerability surrounding exposed Ollama APIs, which provide access to…
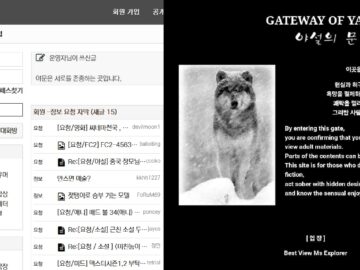
A hacker using the alias “Valerie” is claiming to have hacked Ya-moon, a notorious South Korean private pornography website and…
A recent security analysis of DeepSeek AI‘s distilled DeepSeek-R1 LLaMA 8B variant by cloud-based cybersecurity, compliance, and vulnerability management solutions…
UAC-0006, a financially motivated threat actor, targets PrivatBank customers with advanced phishing attacks. CloudSEK’s research reveals malicious emails containing password-protected…
The gaming industry has grown into a massive global market, with millions of players engaging in online multiplayer games, digital…
Mobile devices have become a prime target for financial fraud, as the availability of digital payments and interception of OTPs…
A 22-year-old Canadian man, Andean Medjedovic, is facing federal charges in the U.S. for allegedly exploiting smart contract vulnerabilities in…
Silver Spring, Maryland, February 5th, 2025, CyberNewsWire Aembit, the non-human identity and access management (IAM) company, today announced that Michael…
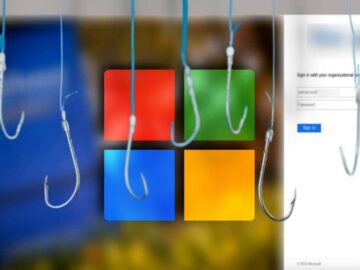
A global phishing campaign is underway, exploiting a legacy Microsoft authentication system to steal user credentials and bypass multi-factor authentication…
Morphisec uncovers a new ValleyRAT malware variant with advanced evasion tactics, multi-stage infection chains, and novel delivery methods targeting systems….
Austin, TX, USA, February 4th, 2025, CyberNewsWire SpyCloud’s Identity Threat Protection solutions spearhead a holistic identity approach to security, illuminating…