Category: HackRead
Python has emerged as a powerful ally in combating rising cybersecurity threats and tracking cybercrime through tools leveraging threat intelligence….
SUMMARY Scammers Use Fake Ads: Cybercriminals are creating fake betting app ads to lure users and steal money and personal…
When looking to create a business, one of the most important things to consider is how you will get it…
Summary Massive Data Leak: Propertyrec exposed over 644,000 records, totaling 713 GB of sensitive data. Sensitive Information: Leaked data includes…
According to recent reports, Ethereum’s Layer 2 solutions could reach an impressive $1 trillion market capitalization by 2030. This positive…
SUMMARY RomCom Exploits Double Zero-Day: RomCom, a Russia-linked group used previously unknown vulnerabilities in Firefox and Windows in a sophisticated attack…
Researchers reveal major vulnerabilities in popular corporate VPN clients, allowing remote attacks. Discover the NachoVPN tool and expert advisories to…
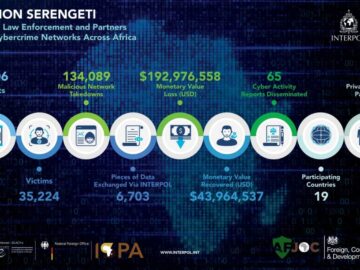
Group-IB collaborated with INTERPOL and AFRIPO in a major crackdown on cybercrime in Africa for “Operation Serengeti.” This article provides…
Cebu, Philippines, November 27th, 2024, CyberNewsWire Cebu-based entrepreneur Brian Christopher Aguilar has emerged as a notable figure in the cryptocurrency…
Protecting sensitive data nowadays should be a top priority for businesses of all sizes. Data breaches and cyber threats are…
Cryptocurrencies are a relatively new asset class, and over the years, they have continued to be the subject of scrutiny…
Aqua Nautilus researchers have discovered a campaign powering a series of large-scale DDoS attacks launched by Matrix, which could be…