Category: HackRead
The Shadowserver Foundation reports over 2,000 Palo Alto Networks firewalls have been hacked via two zero-day vulnerabilities: CVE-2024-0012 & CVE-2024-9474,…
Learn how to prevent payment fraud with effective fraud detection, online prevention solutions, and secure payment orchestration strategies. The Basics…
73% of globally exposed ICS systems are in the US and Europe, with the US leading at 38%. Vulnerabilities in…
Malware bypasses Microsoft Defender and 2FA, stealing $24K in cryptocurrency via a fake NFT game app. Learn how it compromised…
The DOJ proposes tough proposals in its antitrust lawsuit against Google, including selling the Chrome browser, limiting search deals, and…
The US Department of Justice has taken down PopeyeTools, a major online marketplace used by cybercriminals to sell stolen credit…
Five alleged members of the notorious Scattered Spider hacking group have been charged with executing a sophisticated phishing scheme that…
Five alleged members of the notorious Scattered Spider hacking group have been charged with executing a sophisticated phishing scheme that…
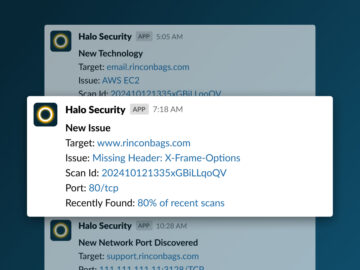
MIAMI, Florida, November 21st, 2024, CyberNewsWire Halo Security, a leader in external attack surface management and penetration testing, has announced…
Choosing the best on-ramp and off-ramp solutions is a key part of navigating the cryptocurrency landscape – to avoid getting…
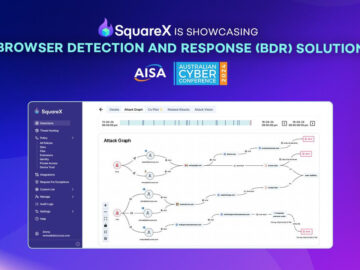
Palo Alto, California, November 20th, 2024, CyberNewsWire SquareX, the leading browser security company, will make its Australian debut at Melbourne…
Forces Penpals, a social network for US and UK military personnel, exposed the sensitive data of 1.1M users, including SSNs,…