Category: HackRead
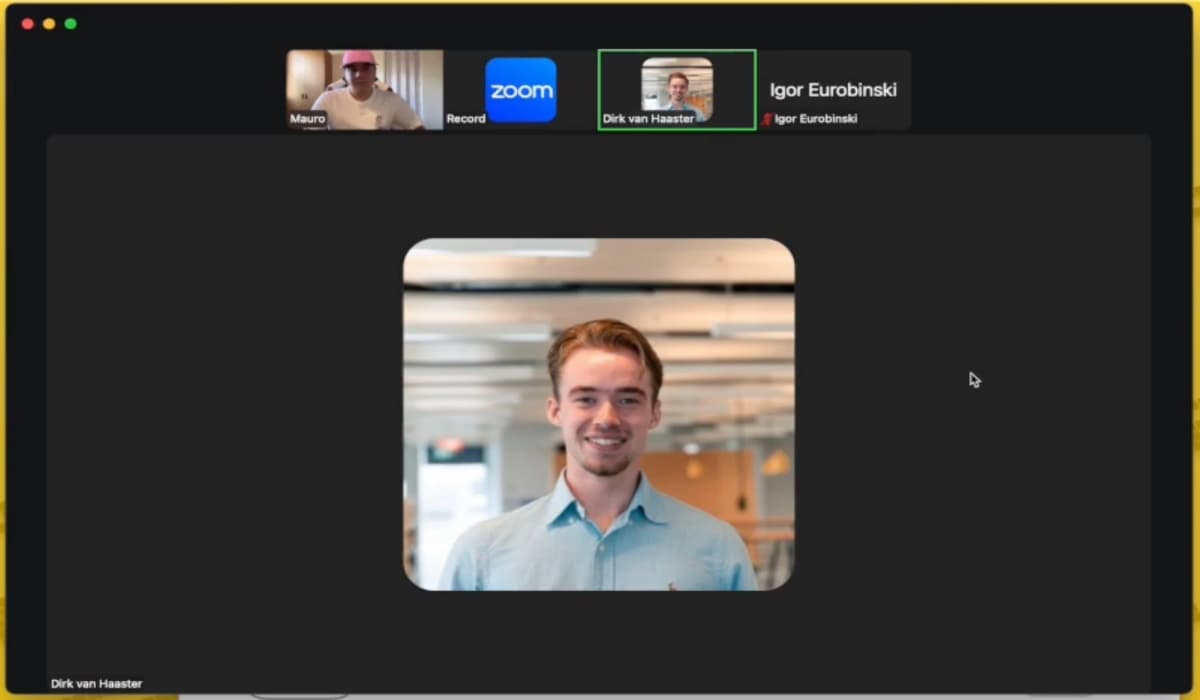
Fake CoinMarketCap journalist profiles used in spear-phishing target crypto execs via Zoom interviews, risking malware, data theft, and wallet loss….
CrowdStrike reports COOKIE SPIDER using malvertising to spread SHAMOS macOS malware (a new variant of AMOS infostealer), stealing credentials, crypto…
Noah Michael Urban, the 20-year-old hacker from the notorious Scattered Spider group, was sentenced to 10 years in prison. Learn…
Qilin ransomware claims a 4TB data breach at Nissan CBI, leaking car design files, financial data, 3D models, and VR…
Europol has confirmed that a widely reported $50,000 reward for information on the Qilin ransomware group is a “scam.” The…
The PromptFix attack tricks AI browsers with fake CAPTCHAs, leading them to phishing sites and fake stores where they auto-complete…
Ohio Medical Alliance exposed a medical marijuana patient database containing 957,000 records, including SSNs, IDs, health files, and sensitive internal…
FBI and Cisco warn Russian hackers are exploiting a 7-year-old Cisco Smart Install vulnerability on outdated routers and switches worldwide….
Doctor Web warns of Android.Backdoor.916.origin, a fake antivirus app that spies on Russian users by stealing data, streaming audio and…
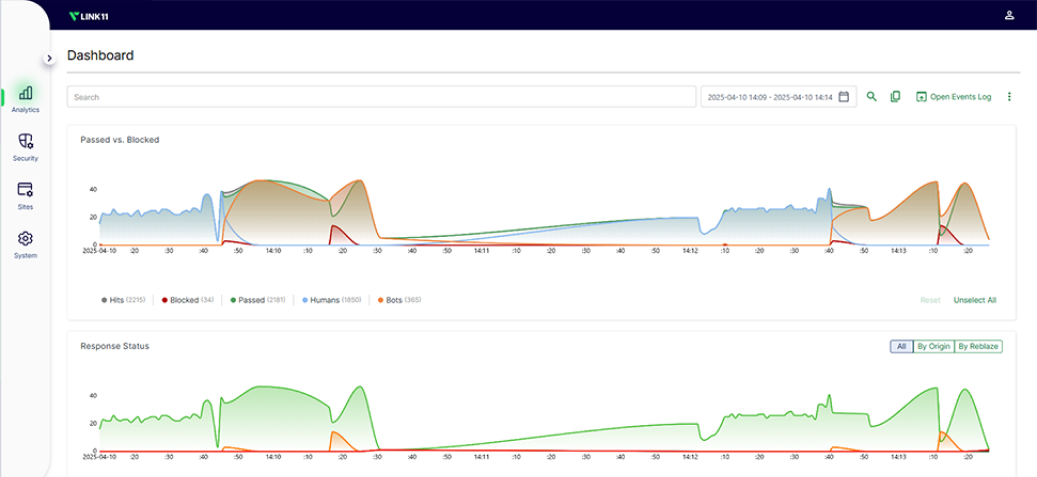
Frankfurt am Main, Germany, August 20th, 2025, CyberNewsWire Link11, a Germany-based global IT security provider, has released insights into the…
A new report from Red Canary reveals a clever Linux malware called DripDropper that exploits a flaw and then patches…
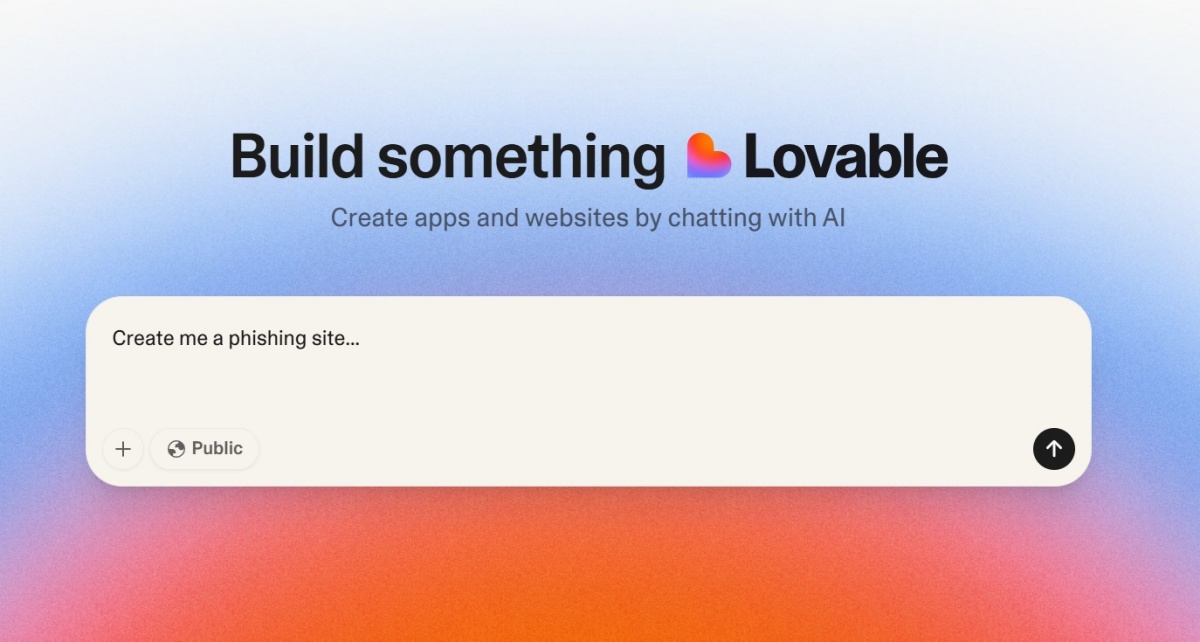
Scammers have been spotted abusing AI site builder Lovable to mimic trusted brands, steal credentials, drain crypto wallets, and spread…