Category: HackRead
A new report from Cofense Intelligence reveals a troubling trend in cyberattacks: criminals are increasingly hijacking legitimate Remote Access Tools…
In a major international operation coordinated by Europol and Eurojust, law enforcement agencies and private sector partners have successfully dismantled…
A newly disclosed vulnerability in Google Chrome and Chromium-based browsers is putting users at risk of data leaks. Tracked as…
Coca-Cola and its bottling partner, Coca-Cola Europacific Partners (CCEP), are facing separate cyberattack claims from two distinct threat groups. The…
In one of the largest global law enforcement actions against dark web crime to date, authorities from ten countries have…
Cybersecurity researcher Jeremiah Fowler discovered a misconfigured cloud server containing a massive 184 million login credentials, likely collected using infostealer…
Ever tried resizing an image only to end up with a blurry, pixelated mess? Whether you’re adjusting a photo for…
A 19-year-old college student faces charges after pleading guilty to cyber extortion targeting PowerSchool, exposing data of 60 million+ students…
Cary, North Carolina, May 22nd, 2025, CyberNewsWire INE Security, a global leader in Cybersecurity training and certifications, has announced a…
As the crypto market continues to mature, investors are looking for sophisticated financial instruments that allow them to capitalize on…
Microsoft, in a global takedown with support from international law enforcement agencies, has disrupted a major malware distribution network responsible…
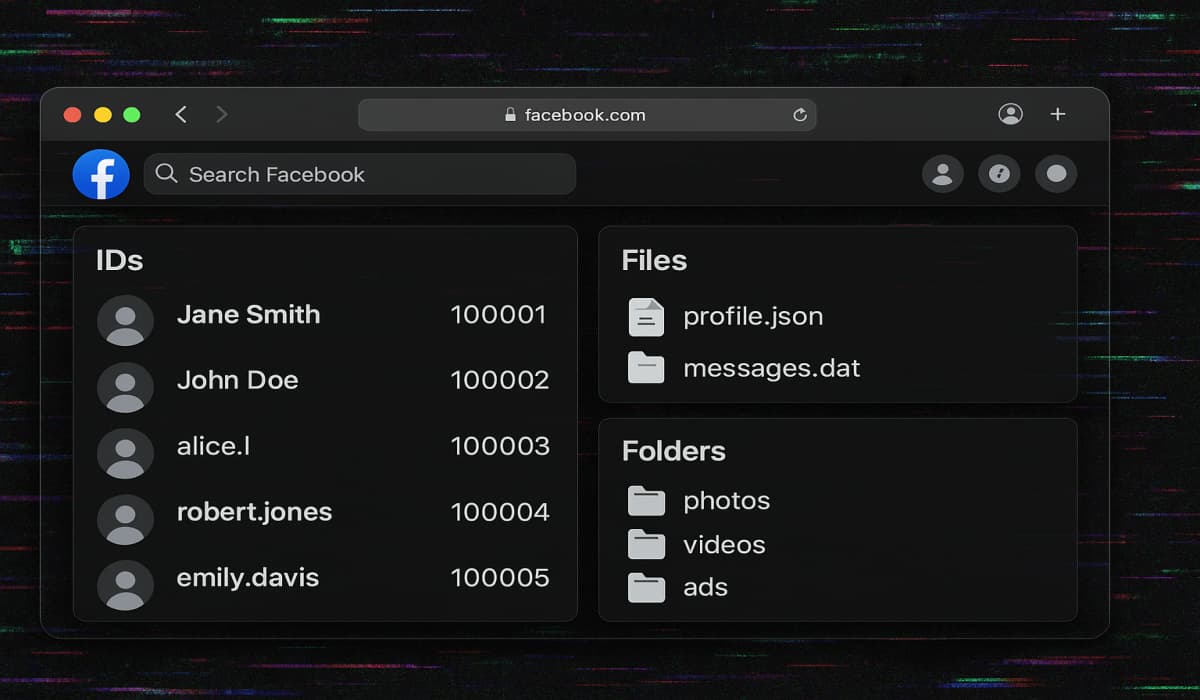
A threat actor using the alias “ByteBreaker” is claiming to have abused the Facebook API and scraped 1.2 billion account…