Category: HackRead
TM SGNL, a chat app by US-Israeli firm TeleMessage used by Trump officials, halts operations after a breach exposed messages…
ESET has discovered Spellbinder, a new tool used by the China-linked cyber espionage group TheWizards to conduct AitM attacks and…
Are you aiming to develop an innovative startup that will make a boom effect in the modern market? If you…
Cybersecurity threats aren’t just aimed at servers or customer databases. They also target a company’s most vital but often overlooked…
Cloudflare’s Q1 2025 DDoS Threat Report: DDoS attacks surged 358% YoY to 20.5M. Germany hit hardest; gaming and telecom were…
watchTowr reveals active exploitation of SonicWall SMA 100 vulnerabilities (CVE-2024-38475 & CVE-2023-44221) potentially leading to full system takeover and session…
Oligo Security uncovers “AirBorne,” a set of 23 vulnerabilities in Apple AirPlay affecting billions of devices. Learn how these flaws…
Fake Qantas emails in a sophisticated phishing scam steal credit card and personal info from Australians, bypassing major email security…
German police seized the dark web shop Pygmalion, gaining access to customer data linked to over 7,000 drug orders in…
Luxury retailer Harrods confirms a cyber attack attempt, restricting internet access but keeping its online store running. Learn about the…
Bitdefender uncovers a massive surge in sophisticated subscription scams disguised as online shops and evolving mystery boxes. Learn how to…
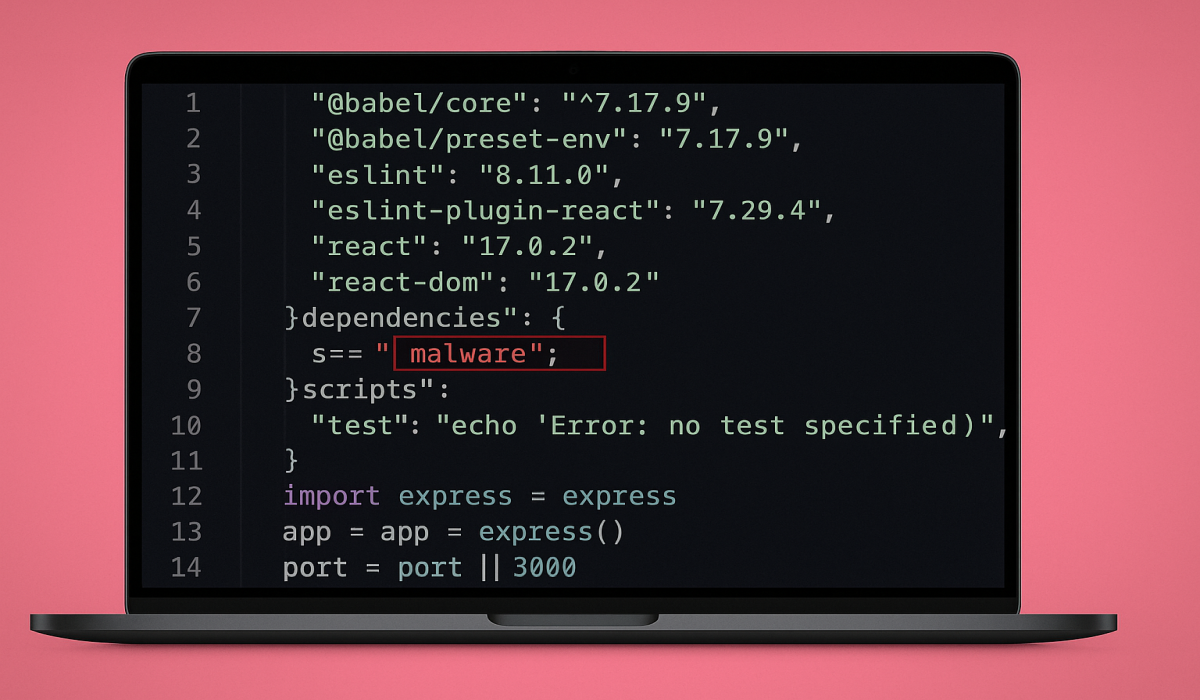
Sonatype discovered ‘crypto-encrypt-ts’, a malicious npm package impersonating the popular CryptoJS library to steal crypto and personal data. Over 1900…