Category: HelpnetSecurity
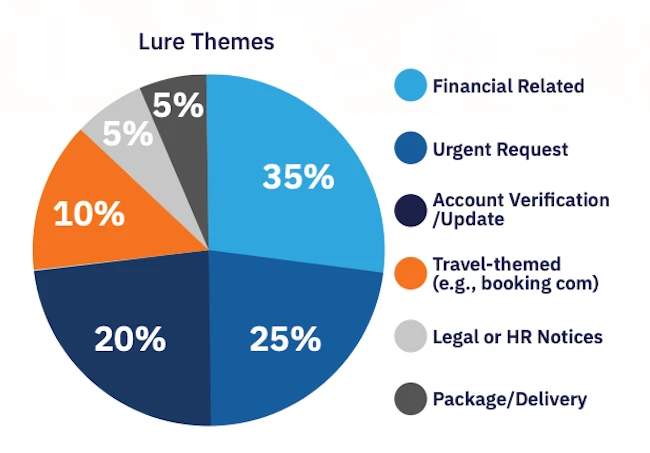
Cybercriminals are deploying unidentifiable phishing kits (58% of phishing sites) to propagate malicious campaigns at scale, indicating a trend towards…
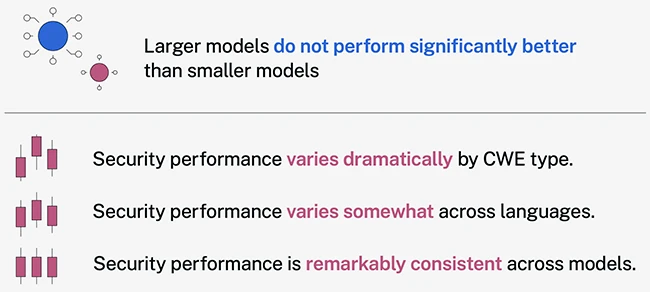
While GenAI excels at producing functional code, it introduces security vulnerabilities in 45 percent of cases, according to Veracode’s 2025…
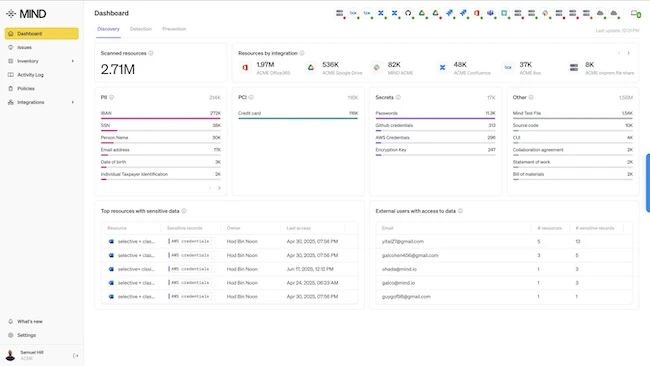
MIND announced the general availability of the first autonomous DLP platform, enabling security teams to safely use GenAI, go beyond…
Adobe has released an emergency security update for Adobe Experience Manager Forms on Java Enterprise Edition (JEE), which fix two…
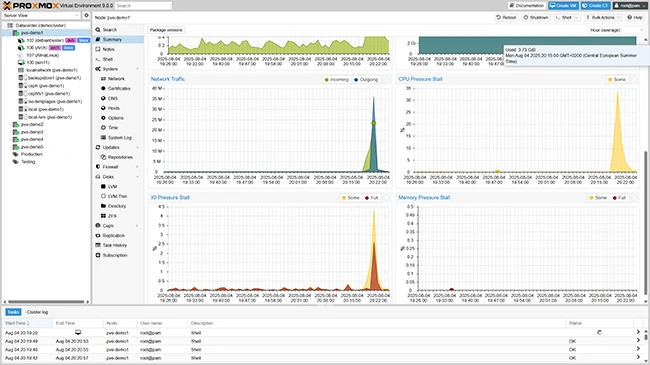
Proxmox Virtual Environment (VE) 9.0 introduces advancements in both storage and networking capabilities, addressing critical enterprise demands. A highlight is…
SpyCloud has introduced enhancements to its SaaS Investigations solution, integrating advanced AI-powered insights that mirror the tradecraft of SpyCloud’s seasoned…
Unauthenticated command injection vulnerabilities (CVE-2025-54948, CVE-2025-54987) affecting the on-premise version of Trend Micro’s Apex One endpoint security platform are being…
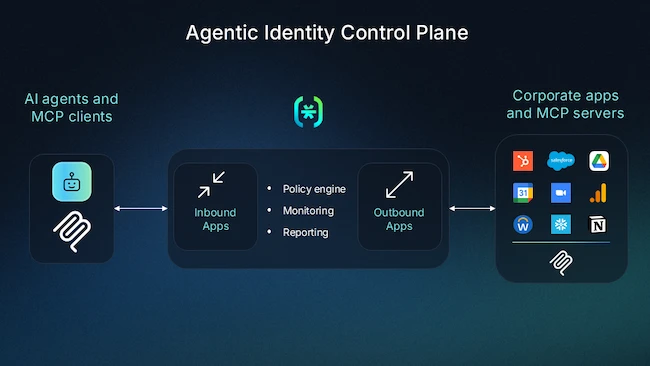
Descope launched Agentic Identity Control Plane, a solution that enables security teams to institute policy-based governance, auditing, and identity management…
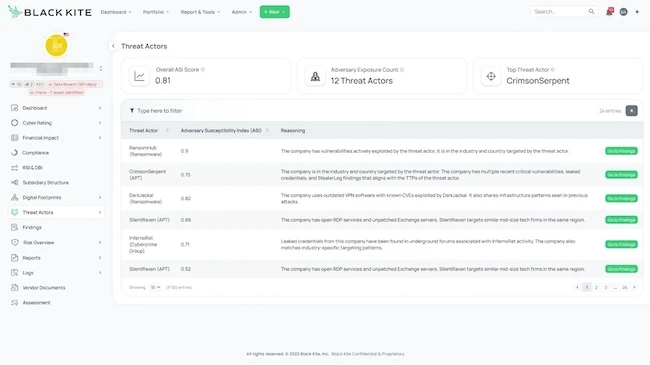
Black Kite has unveiled the Adversary Susceptibility Index (ASI), a tool designed for TPRM teams to proactively identify which vendors…
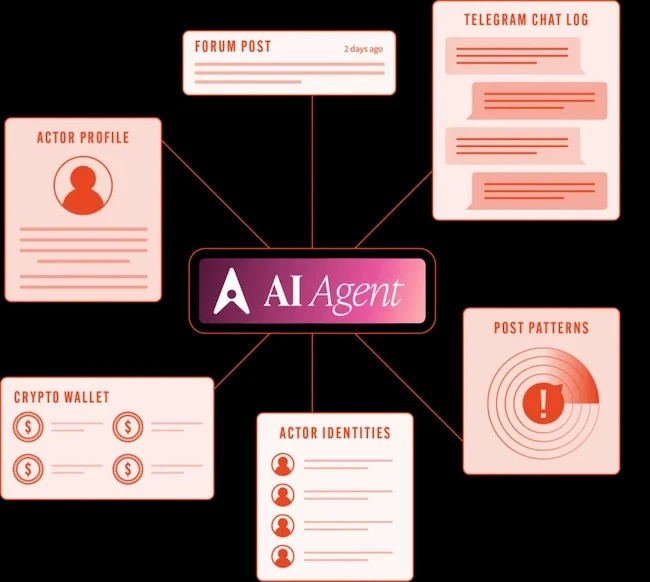
Searchlight Cyber has released a new AI capability that summarizes the activity of a threat actor in its dark web…
Cyber attackers are finding new ways in through the overlooked and unconventional network corners. Forescout’s 2025H1 Threat Review reveals a…
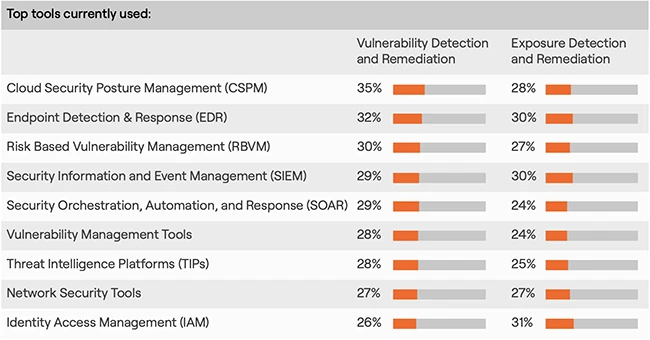
Most security teams believe they can act quickly when a threat emerges. But many don’t trust the very data they…