Category: HelpnetSecurity
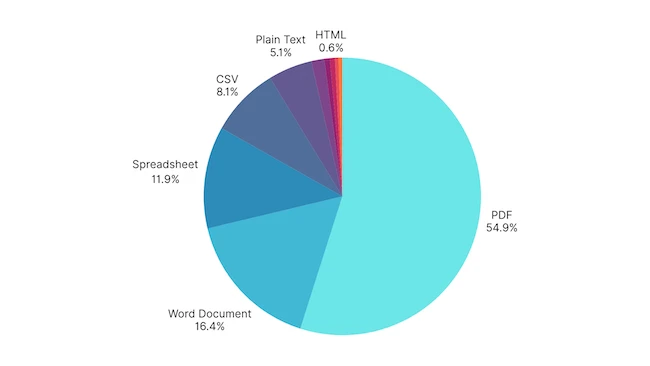
In Q2 2025, Harmonic reviewed 1 million GenAI prompts and 20,000 uploaded files across more than 300 GenAI and AI-powered…
CW – OT Security Officer SSE | United Kingdom | On-site – View job details As a CW – OT…
Attackers wielding the Akira ransomware and possibly a zero-day exploit have been spotted targeting SonicWall firewalls since July 15, 2025….
Organizations most confident in their identity security are often the least prepared, according to a new report from BeyondID. The…
In this Help Net Security interview, Marc Frankel, CEO at Manifest Cyber, discusses how overlooked AI-specific risks, like poisoned training…
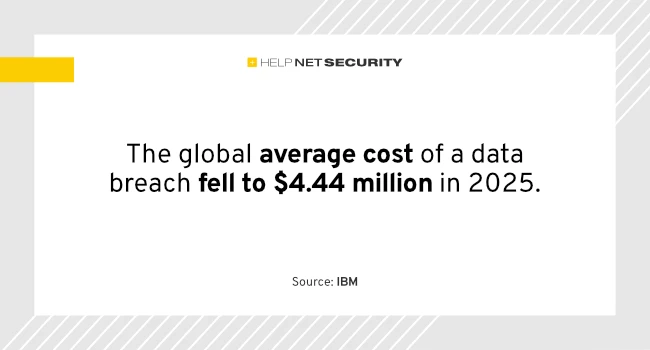
IBM released its Cost of a Data Breach Report, which revealed AI adoption is greatly outpacing AI security and governance….
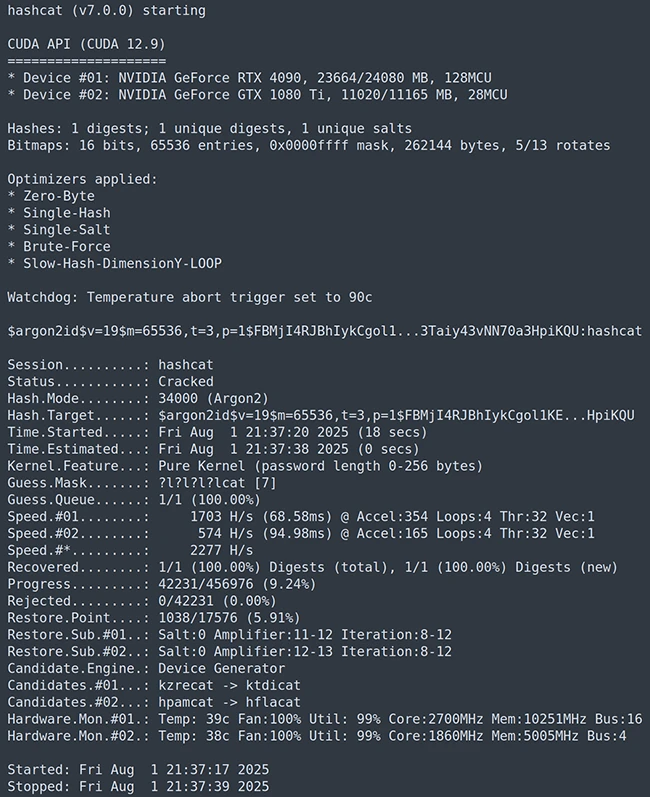
Hashcat is an open-source password recovery tool that supports five attack modes and more than 300 highly optimized hashing algorithms….
Enterprise risk leaders are most concerned about rising tariffs and trade tensions heading into the second half of 2025, according…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Review: LLM Engineer’s HandbookFor all…
In this Help Net Security interview, Rohan Sen, Principal, Cyber, Data, and Tech Risk, PwC US, discusses how organizations can…
A cyberattack on a water facility can put entire communities and businesses at risk. Even a short disruption in clean…
CISA Certified Information Systems Auditor Practice Tests offers practical, domain-by-domain prep for the CISA exam, with hundreds of questions covering…