Category: HelpnetSecurity
In this Help Net Security interview, Gonçalo Magalhães, Head of Security at Immunefi, discusses the legal and ethical implications of…
Vulnhuntr is an open-source tool that finds remotely exploitable vulnerabilities. It uses LLMs and static code analysis to trace how…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Microsoft pins on-prem SharePoint attacks…
It’s been six months since the EU’s Digital Operational Resilience Act (DORA) came into effect, but a new Censuswide survey…
In this Help Net Security interview, Benjamin Schilz, CEO of Wire, discusses Europe’s push for digital sovereignty through initiatives like…
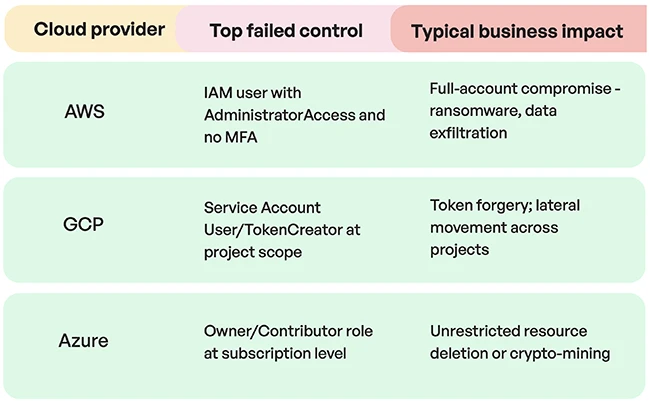
Most organizations still miss basic identity security controls in the cloud, leaving them exposed to breaches, audit failures, and compliance…
Here’s a look at the most interesting products from the past week, featuring releases from Akeyless, Bitdefender, Malwarebytes, ManageEngine, PlexTrac,…
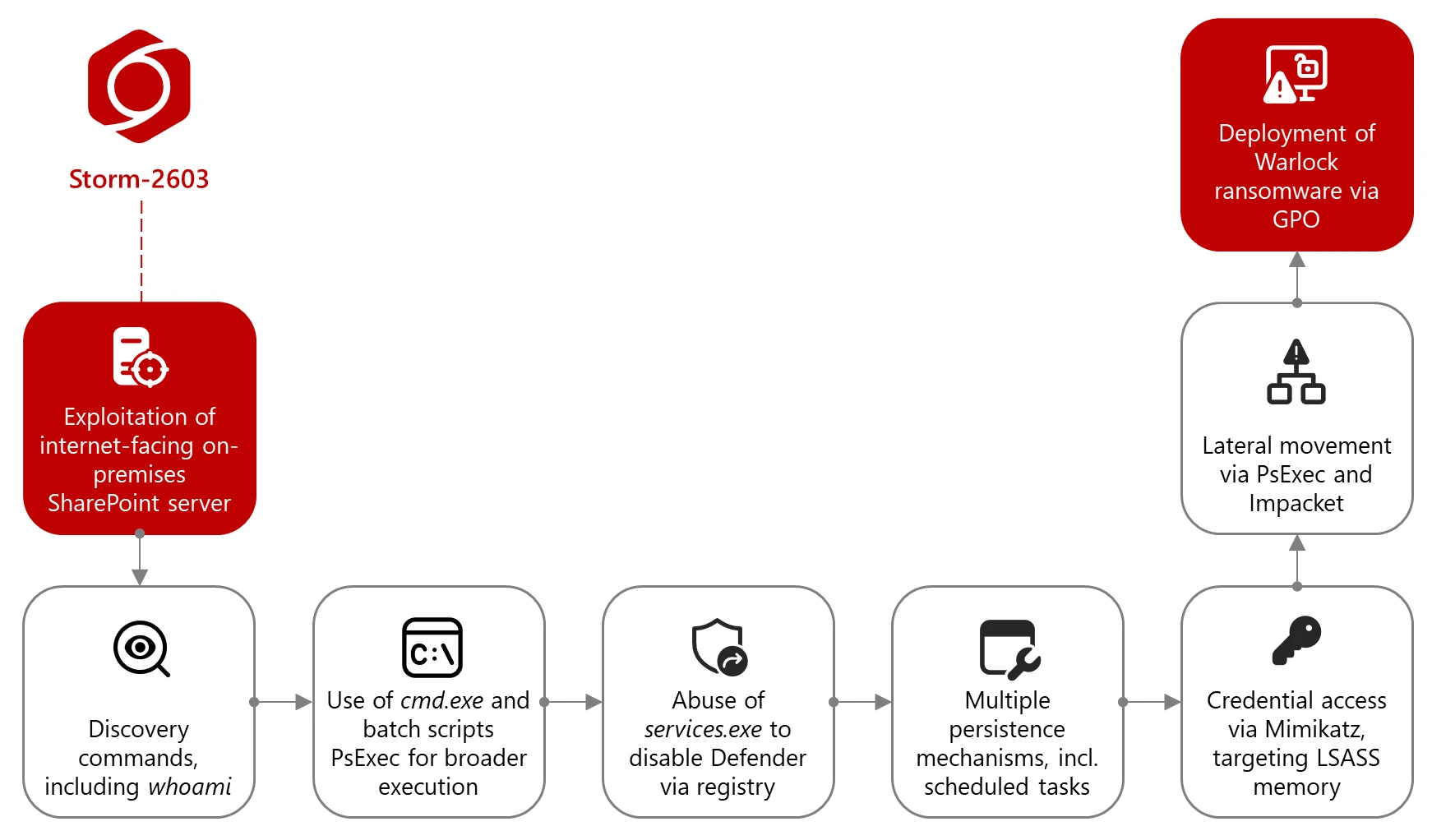
One of the groups that, in the past few weeks, has been exploiting vulnerabilities in on-prem SharePoint installation has been…
The annual CISO New York summit will be held on September 9, 2025, uniting over 150 senior cybersecurity executives for…
Sonicwall is asking customers running specific Secure Mobile Access (SMA) 100 Series devices to patch a newly uncovered vulnerability (CVE-2025-40599)…
In this Help Net Security interview, Aleksandar Stančin, Board Member Adriatics, Exclusive Networks, discusses the state of cybersecurity in the…
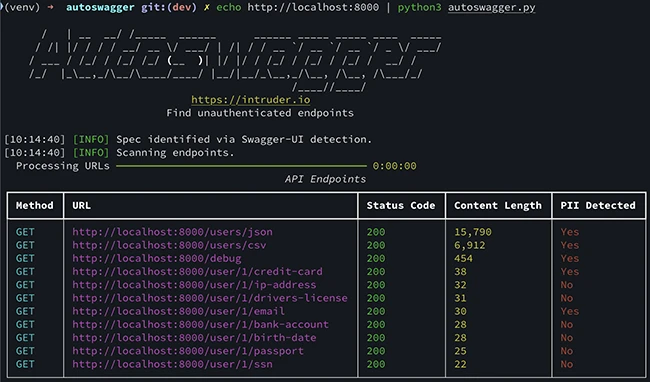
Autoswagger is a free, open-source tool that scans OpenAPI-documented APIs for broken authorization vulnerabilities. These flaws are still common, even…