Category: HelpnetSecurity
Application-layer attacks have become one of the most common and consequential methods adversaries use to gain access and compromise organizations,…
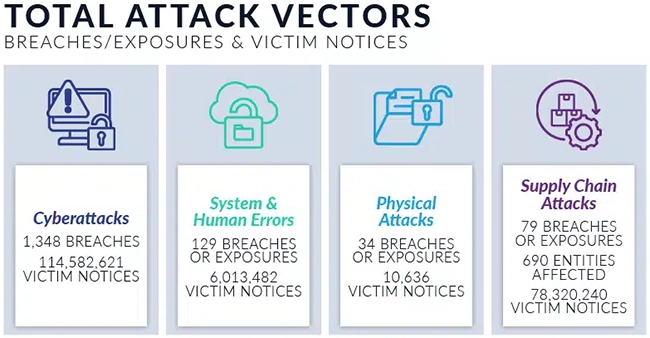
The Identity Theft Resource Center (ITRC) reports 1,732 publicly disclosed data breaches in H1 2025, marking a 5% increase over…
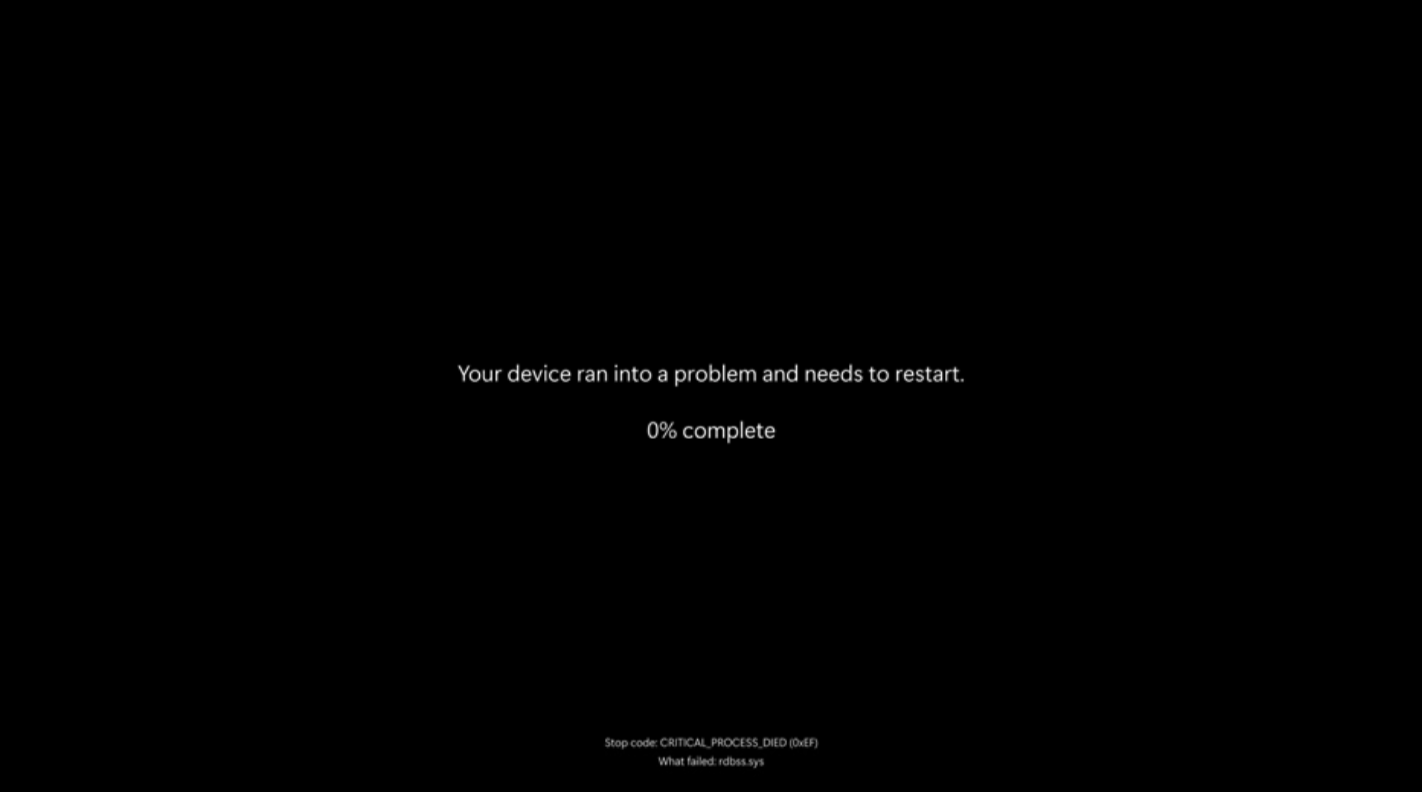
With the latest Windows 11 update, Microsoft is saying goodbye to the infamous “Blue Screen of Death” and has enabled…
The suspected administrator of xss.is, one of the world’s most influential Russian-speaking cybercrime forums, was arrested in Kyiv, Ukraine, on…
Bitdefender expanded support for Facebook and Instagram for Bitdefender Security for Creators, a dedicated cybersecurity solution for digital content creators,…
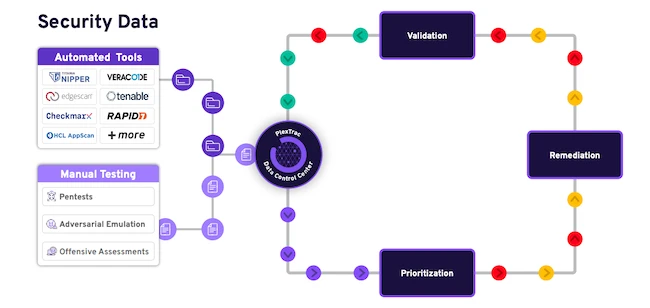
PlexTrac launched enhanced Workflow Automation Engine, a major product update designed to standardize workflows across the vulnerability lifecycle, automate pentest…
One or more vulnerabilities affecting Cisco Identity Services Engine (ISE) are being exploited in the wild, Cisco has confirmed by…
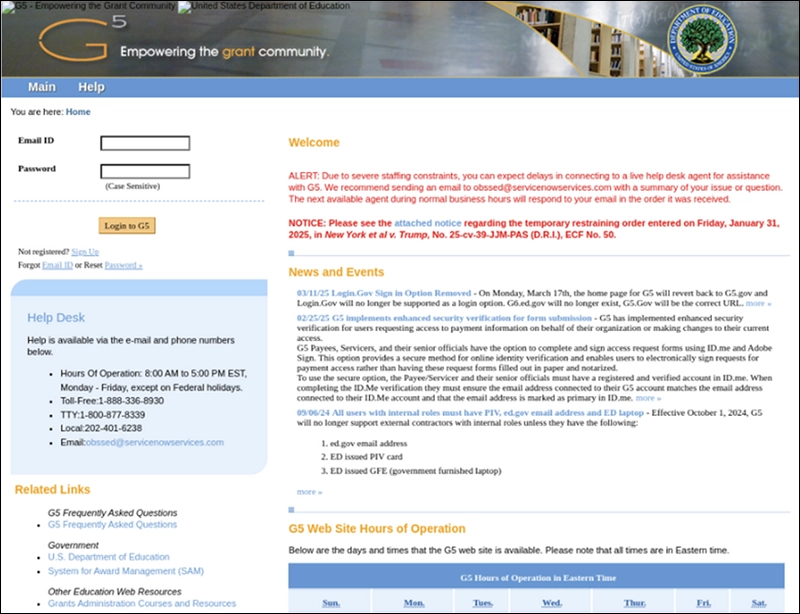
A new phishing campaign is targeting users of the U.S. Department of Education’s G5 portal, a site used by educational…
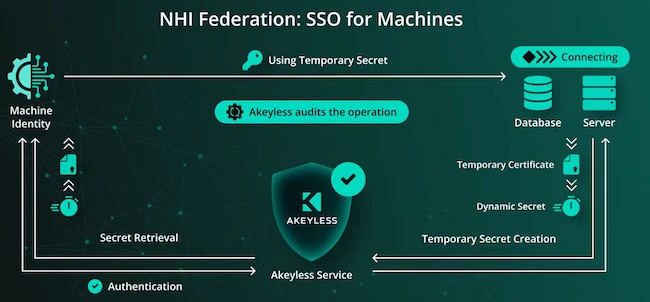
Akeyless launched NHI Federation, a solution that delivers Single Sign-On (SSO) for machines. As organizations increasingly operate workloads across on-premises…
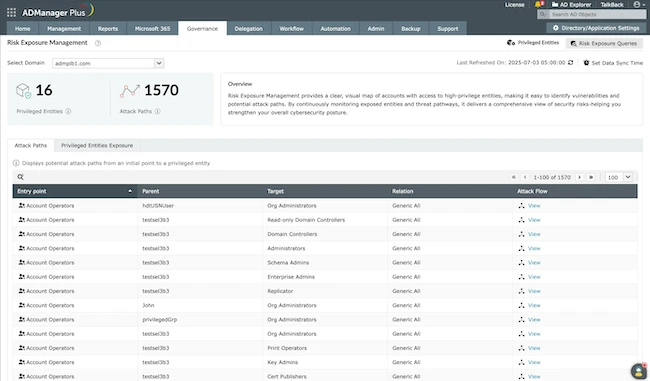
ManageEngine announced identity risk exposure management and local user MFA features in AD360, its converged identity and access management (IAM)…
A new policy brief from NATO’s Cooperative Cyber Defence Centre of Excellence (CCDCOE) warns that critical port infrastructure, responsible for…
Cervantes is an open-source collaborative platform built for pentesters and red teams. It offers a centralized workspace to manage projects,…