Category: HelpnetSecurity
Phishing is one of the oldest and most effective scams used by cybercriminals. No one is immune to them, not…
Fraud is growing faster than revenue in eCommerce. That’s one of the first things PwC and Forter point out in…
As Microsoft continues to update its customer guidance for protecting on-prem SharePoint servers against the latest in-the-wild attacks, more security…
Data breaches seem to pop up in the news every other week, so it’s no surprise that keeping sensitive information…
Printer platform security is often overlooked in enterprise security strategies, creating security gaps, according to HP Wolf Security. By addressing…
A new survey from ISC2 shows that nearly a third of cybersecurity professionals are already using AI security tools, and…
CISO Kbrw | France | Hybrid – View job details As a CISO, you will develop risk management processes aligned…
Unknown attackers have exploited a vulnerability (CVE-2025‑54309) in the CrushFTP enterprise file-transfer server solution to gain administrative access to vulnerable…
Nearly one in 12 employees are using Chinese-developed generative AI tools at work, and they’re exposing sensitive data in the…
In this Help Net Security interview, Flavio Aggio, CISO at the World Health Organization (WHO), explains how the organization prepares…
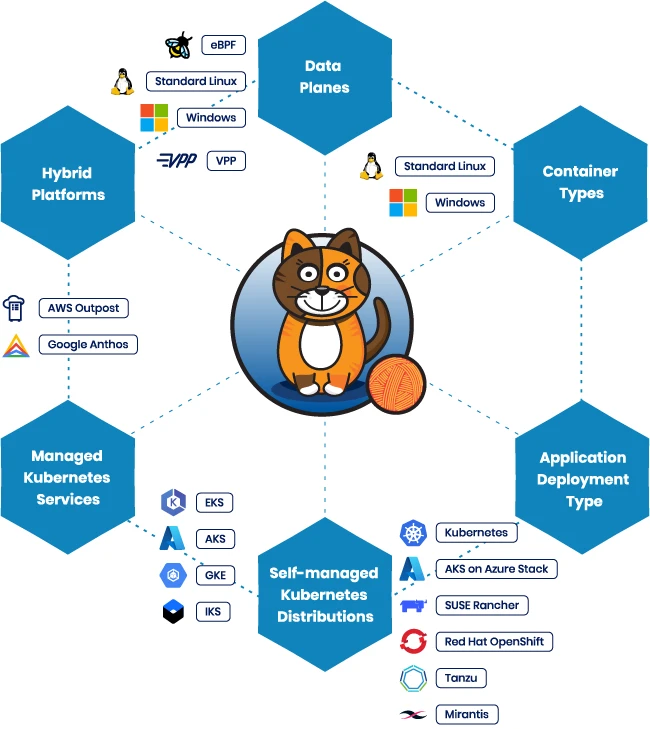
Calico is an open-source unified platform that brings together networking, security, and observability for Kubernetes, whether you’re running in the…
Aircraft systems are getting more connected and ground operations increasingly integrated, and attackers are taking notice. They’re shifting from minor…