Category: HelpnetSecurity
In this Help Net Security interview, Cindy Segond von Banchet CC, Cybersecurity Lead at Yokogawa Europe, shares her insights on…
In this Help Net Security video, Andy Ulrich, CISO at Vonage, explains how silent authentication offers a smarter, seamless solution…
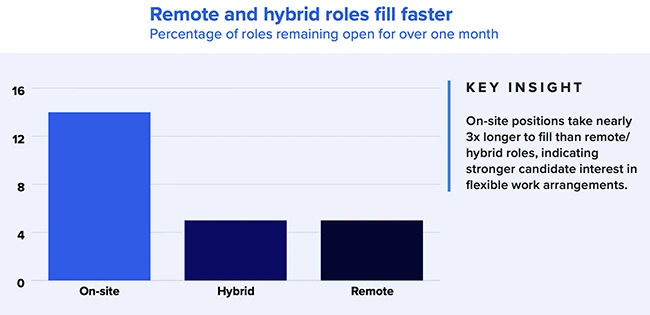
Many companies say they can’t find enough cybersecurity professionals. But a new report suggests the real problem isn’t a lack…
Unknown intruders are targeting fully patched end-of-life SonicWall Secure Mobile Access (SMA) 100 series appliances and deploying a novel, persistent…
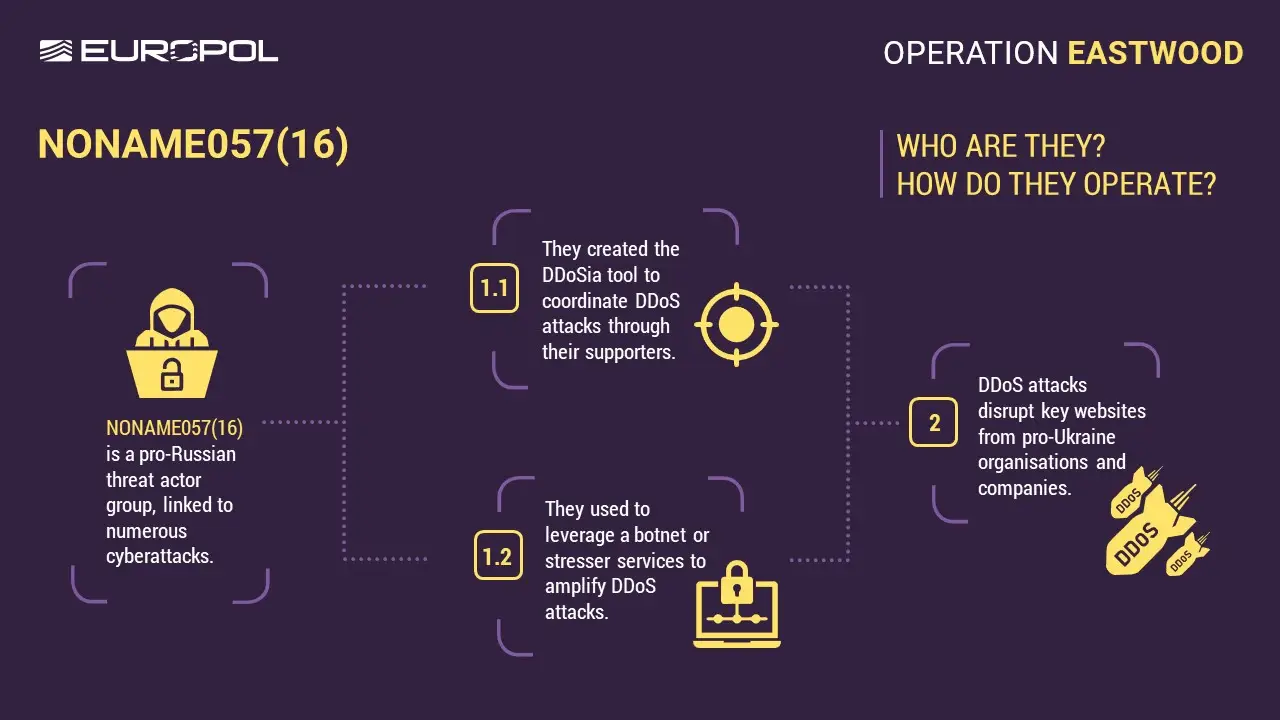
In a major blow to pro-Russian cybercrime, authorities across Europe and the United States launched a sweeping international crackdown on…
For the fifth time this year, Google has patched a Chrome zero-day vulnerability (CVE-2025-6558) exploited by attackers in the wild….
Immersive announced its Immersive One AI-powered Lab Builder feature to give customers and partners new ways to improve cyber skills…
2025 has been a busy year for cybersecurity. From unexpected attacks to new tactics by threat groups, a lot has…
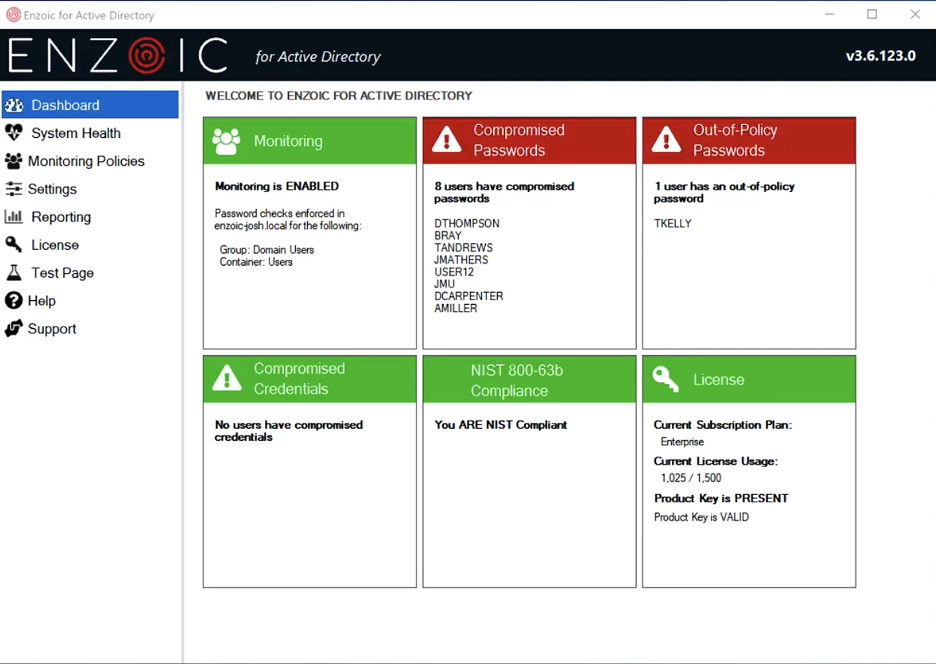
Enzoic for Active Directory is an easy-to-install plugin that integrates with Microsoft Active Directory (AD) to set, monitor, and remediate…
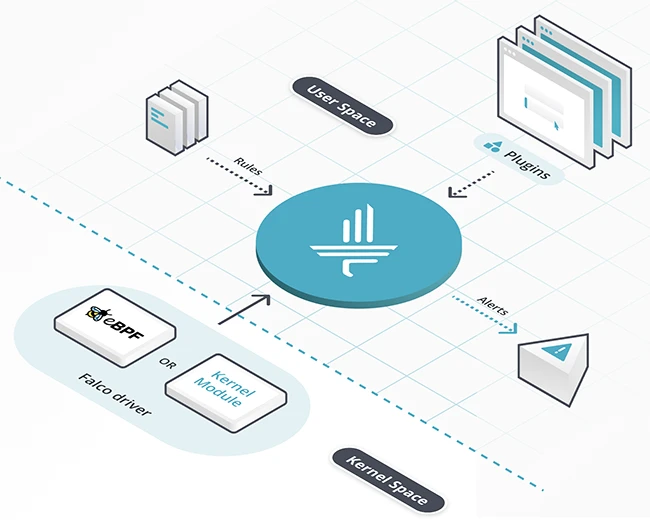
Falco is an open-source runtime security tool for Linux systems, built for cloud-native environments. It monitors the system in real…
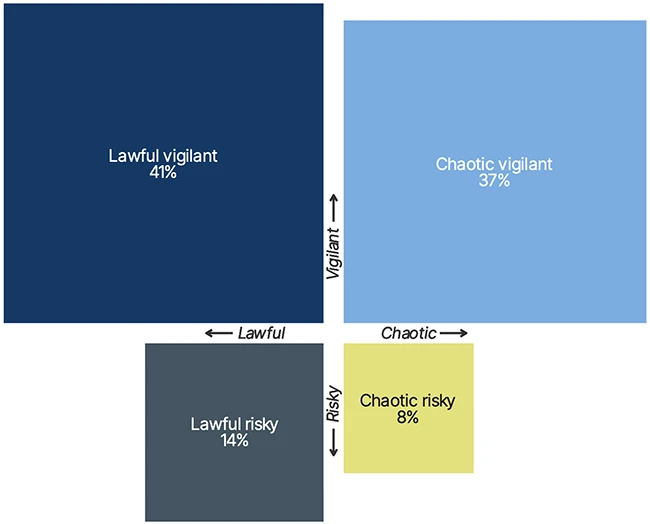
A new report from Living Security and the Cyentia Institute sheds light on the real human element behind cybersecurity threats,…
UEFI firmware running on 100+ Gigabyte motherboard models is affected by memory corruption vulnerabilities that may allow attackers to install…