Category: HelpnetSecurity
A new report from Zendesk outlines a growing problem for companies rolling out AI tools: many aren’t ready to manage…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Microsoft fixes critical wormable Windows…
Threat actors are actively exploiting a recently fixed remote code execution vulnerability (CVE-2025-47812) in Wing FTP Server, security researchers have…
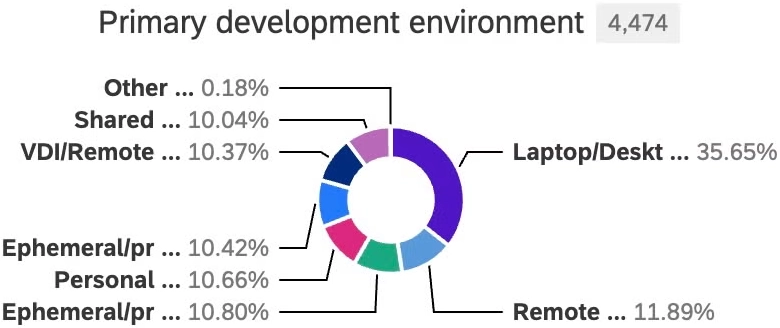
How are developers working in 2025? Docker surveyed over 4,500 people to find out, and the answers are a mix…
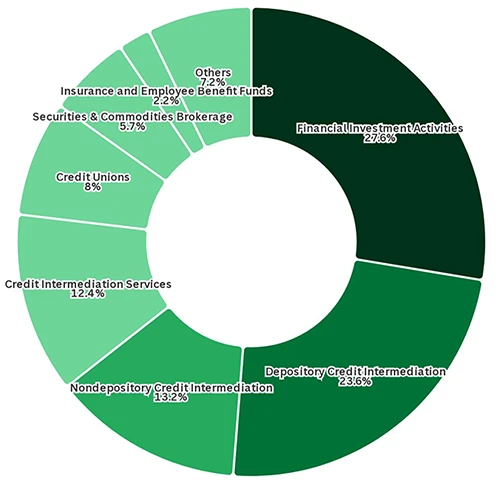
Financial institutions are building stronger defenses against direct cyberattacks, but they may be overlooking a growing problem: their vendors. According…
In this Help Net Security interview, Thijs Povel, Managing Partner at Ventures.eu, discusses how the firm evaluates emerging technologies through…
While IT departments race to implement AI governance frameworks, many employees have already opened a backdoor for AI, according to…
Here’s a look at the most interesting products from the past week, featuring releases from Barracuda Networks, Cynomi, Lepide, Tosibox,…
Four individuals suspected of having been involved in the ransomware attacks that hit UK-based retailers earlier this year have been…
Claroty researcher Noam Moshe has discovered serious vulnerabilities in two Ruckus Networks (formerly Ruckus Wireless) products that may allow attackers…
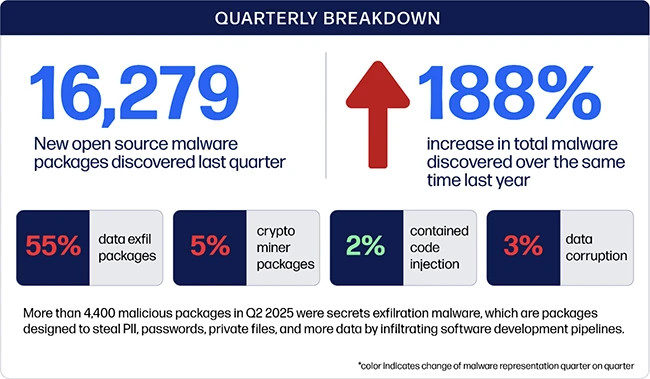
Sonatype has published its Q2 2025 Open Source Malware Index, identifying 16,279 malicious open source packages across major ecosystems such…
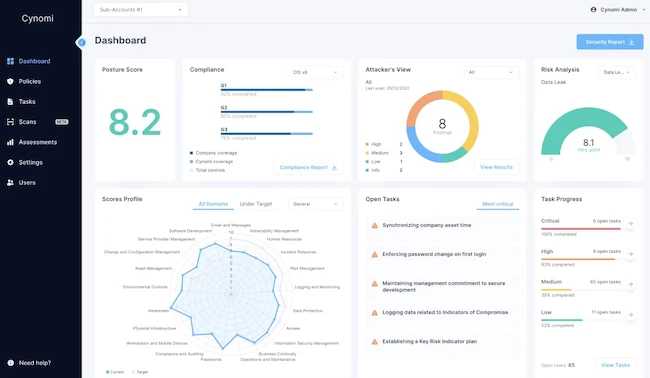
Cynomi has launched new business impact analysis (BIA) and business continuity planning (BCP) features. Designed to help cybersecurity professionals identify…