Category: HelpnetSecurity
IBM unveiled Power11 today, a new generation of Power servers built to improve performance across processing, hardware, and virtualization. It’s…
ParrotOS, known for its emphasis on security, privacy, and development, is widely used by cybersecurity professionals and enthusiasts alike. Version…
In this Help Net Security interview, Dan DeCloss, Founder and CTO at PlexTrac, discusses the role of exposure management in…
Sports fans and cybercriminals both look forward to major sporting events, but for very different reasons. Fake ticket sites, stolen…
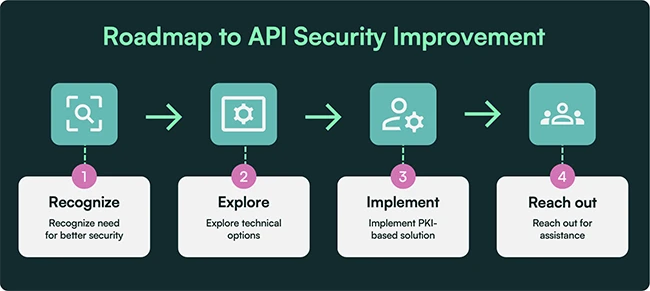
Most organizations are exposing sensitive data through APIs without security controls in place, and they may not even realize it,…
Analyst III-Threat Intel Verizon Data Services | India | Hybrid – View job details As an Analyst III-Threat Intel, you…
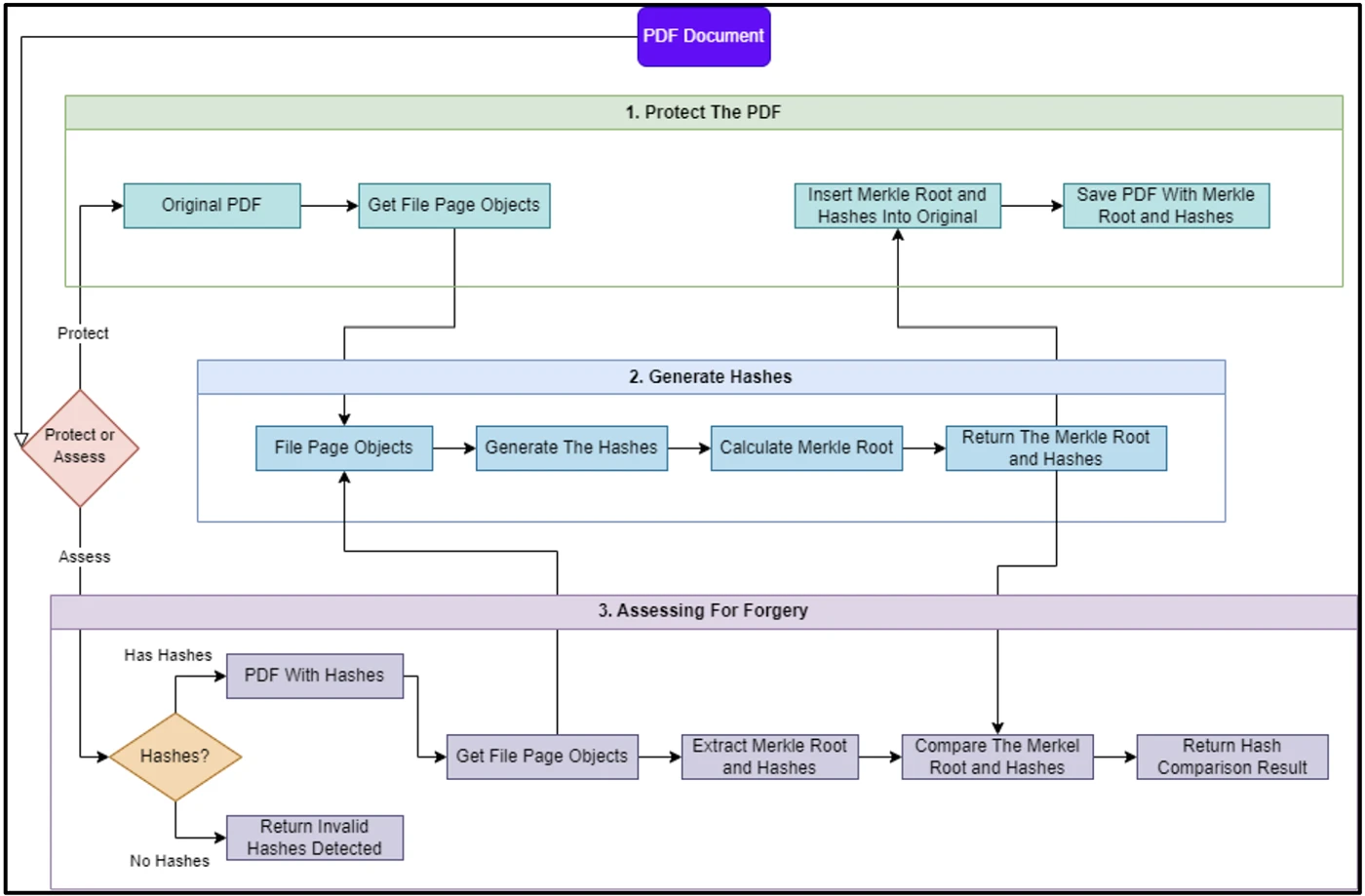
Researchers from the University of Pretoria presented a new technique for detecting tampering in PDF documents by analyzing the file’s…
There was a barrage of updates released the week of June 2025 Patch Tuesday. This included security updates from Adobe,…
In this Help Net Security interview, John Morello, CTO at Minimus, discusses the security risks in AI-driven development, where many…
Aegis Authenticator is an open-source 2FA app for Android that helps you manage login codes for your online accounts. The…
Attack Surface Management (ASM) has become one of those buzzwords that gets used a lot but rarely explained in detail….
While most enterprises have integrated cloud resources into their operations, many need to improve their ability to secure these environments…