Category: HelpnetSecurity
Google has released a security update for Chrome to address a zero‑day vulnerability (CVE-2025-6554) that its Threat Analysis Group (TAG)…
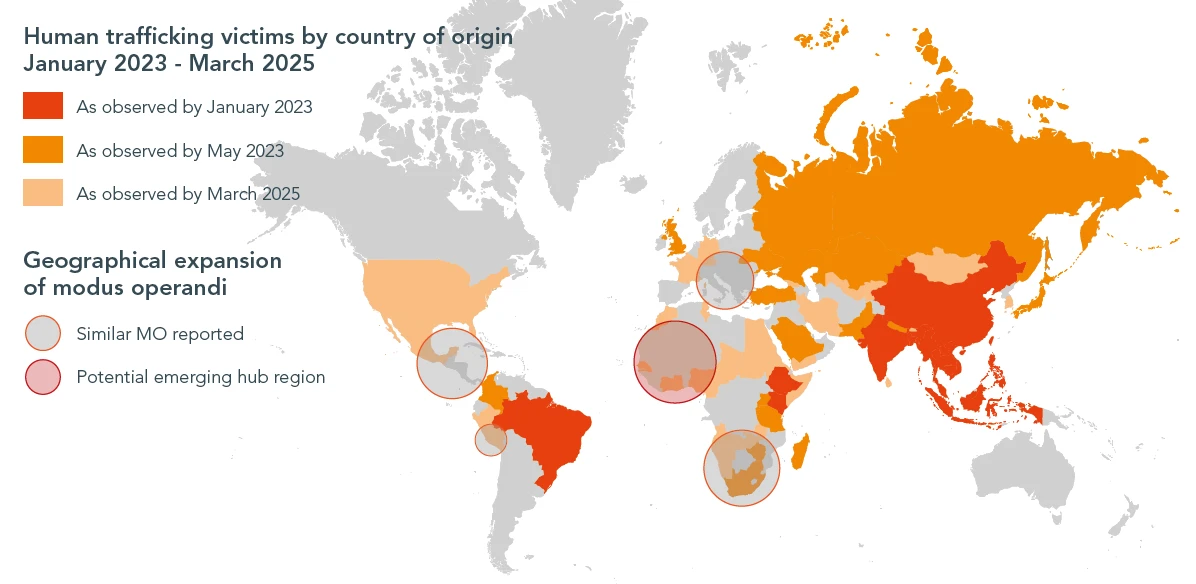
Human trafficking tied to online scam centers is spreading across the globe, according to a new crime trend update from…
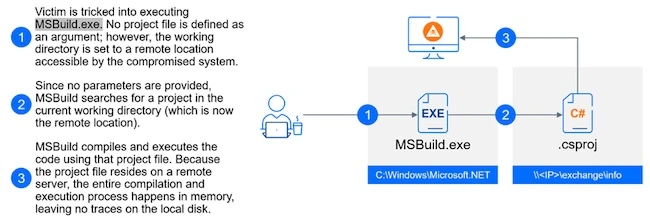
This article shares initial findings from internal Bitdefender Labs research into Living off the Land (LOTL) techniques. Our team at…
In this Help Net Security interview, Tammy Hornsby-Fink, CISO at Federal Reserve System, shares how the Fed approaches cyber risk…
In a recent case tracked by Flashpoint, a finance worker at a global firm joined a video call that seemed…
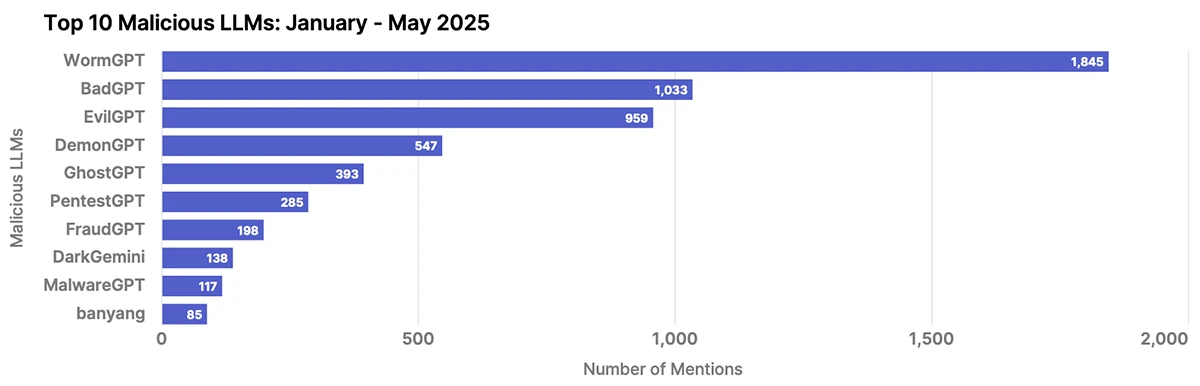
Nearly three out of four European IT and cybersecurity professionals say staff are already using generative AI at work, up…
Application Security Engineer Fireblocks | Israel | Hybrid – View job details As an Application Security Engineer, you will improve…
Spanish authorities arrested five members of a criminal network responsible for laundering €460 million stolen through global cryptocurrency investment fraud…
While Citrix has observed some instances where CVE-2025-6543 has been exploited on vulnerable NetScaler networking appliances, the company still says…
Cato Networks has raised $359 million in a late-stage funding round, bringing its total valuation to $4.8 billion. The company,…
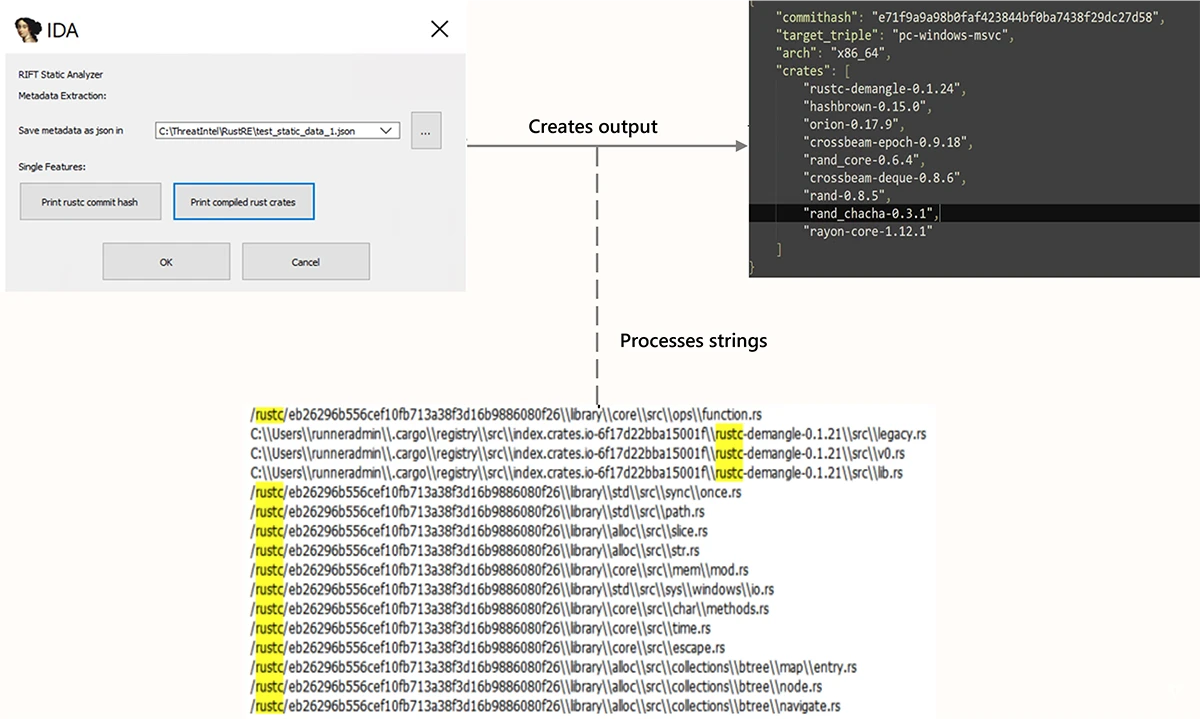
Microsoft’s Threat Intelligence Center has released a new tool called RIFT to help malware analysts identify malicious code hidden in…
In this Help Net Security interview, Chris McGranahan, Director of Security Architecture & Engineering at Backblaze, discusses how AI is…