Category: HelpnetSecurity
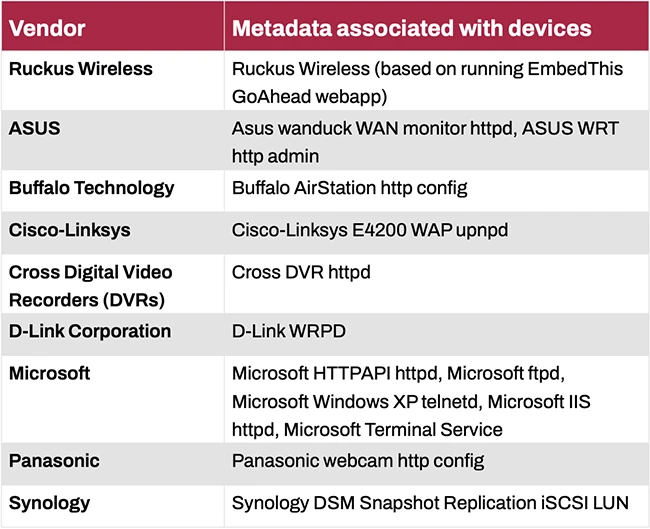
SecurityScorecard’s STRIKE team has uncovered a network of compromised small office and home office (SOHO) devices they’re calling LapDogs. The…
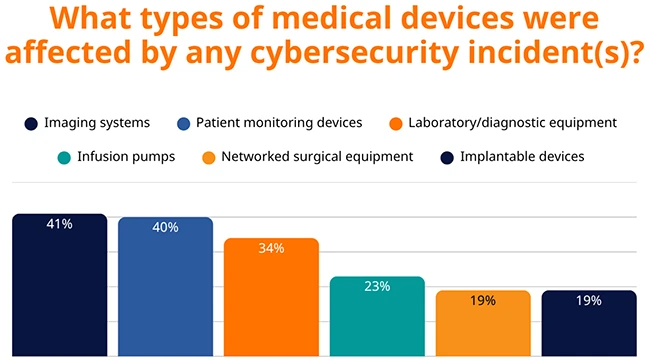
22% of healthcare organizations have experienced cyberattacks that directly impacted medical devices, according to RunSafe Security. Three-quarters of these incidents…
Redefining Hacking takes a look at how red teaming and bug bounty hunting are changing, especially now that AI is…
In this Help Net Security interview, John Verry, Managing Director at CBIZ, discusses how insurers and financial risk professionals evaluate…
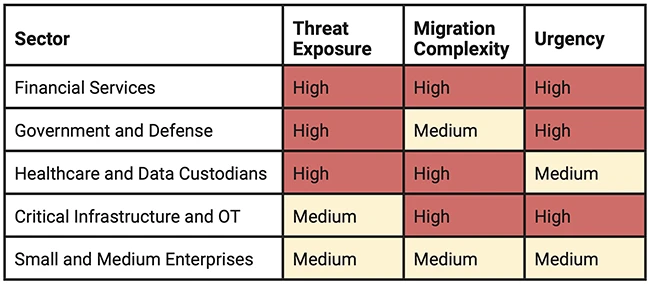
A new report from the Cyber Threat Alliance warns that the era of quantum risk is already underway, and security…
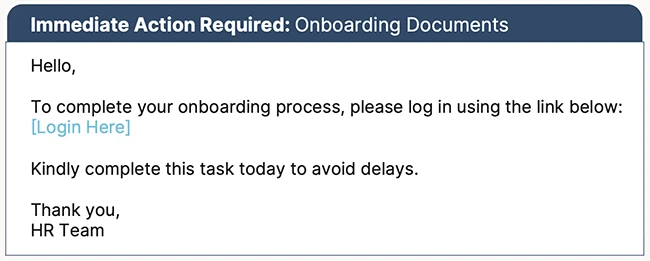
New hires are more likely to fall for phishing attacks and social engineering than longer-term employees, especially in their first…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Researchers unearth keyloggers on Outlook…
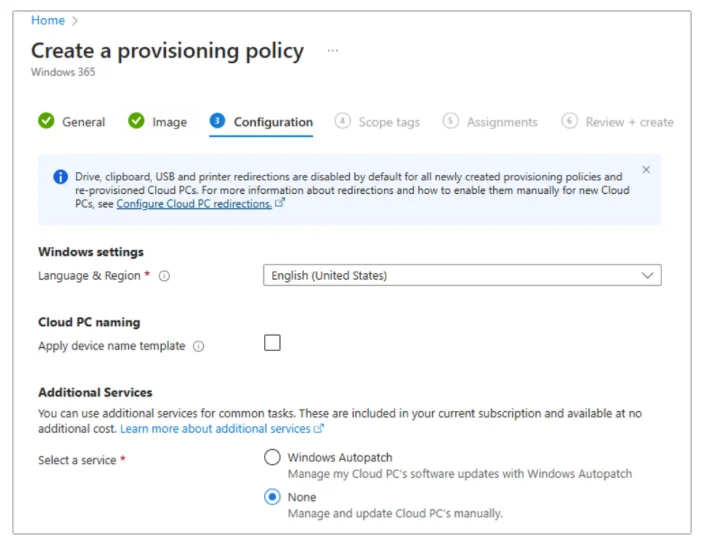
Windows 365 Cloud PCs now come with new default settings aimed at preventing / minimizing data exfiltration and malicious exploits,…
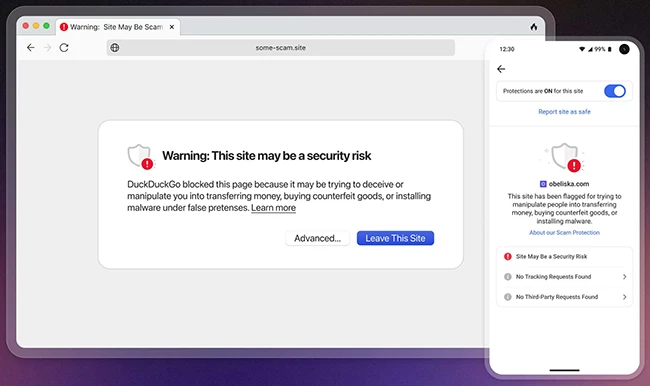
Online scams are getting worse and more varied. DuckDuckGo knows that, so they’ve made changes. Their built-in Scam Blocker now…
Amazon Linux 2023 (AL2023) has earned FIPS 140-3 Level 1 validation for several of its cryptographic modules. This means it’s…
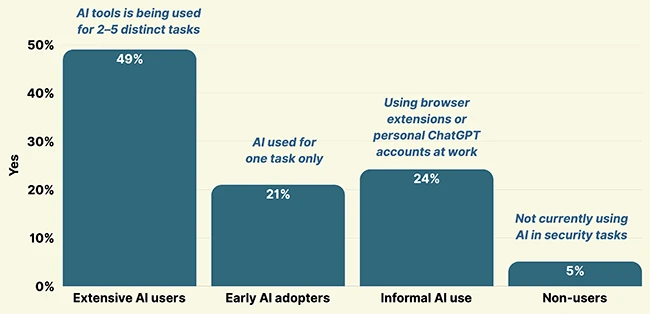
Even security teams, the ones responsible for protecting the business, are adding to AI-related risk. A new survey by AI…
In this Help Net Security interview, Rob ter Linden, CISO at Signify, discusses priorities for CISOs working on IoT security,…