Category: HelpnetSecurity
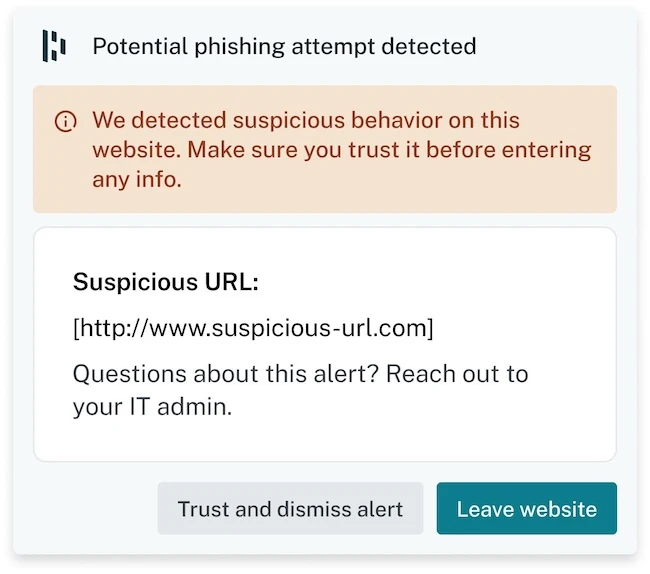
Dashlane introduced AI phishing alerts, an advancement to the Dashlane Omnix platform that protects enterprises and users against threats targeting…
As applications become more distributed, traditional monitoring and security tools are failing to keep pace. This article explores how eBPF,…
This article showcases free, open-source security tools that support your organization’s teams in red teaming, threat hunting, incident response, vulnerability…
Despite widespread anticipation about AI’s positive impact on workforce productivity, most employees feel they were overpromised on its potential, according…
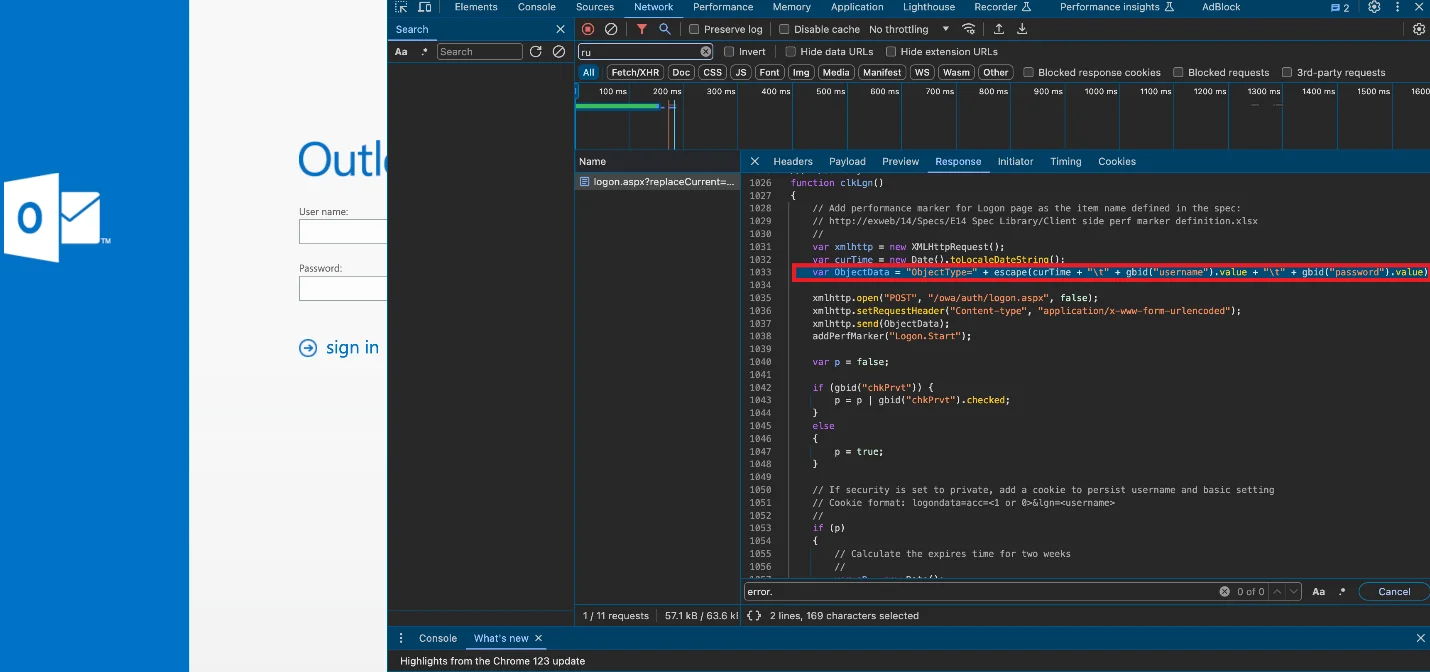
Unknown threat actors have compromised internet-accessible Microsoft Exchange Servers of government organizations and companies around the world, and have injected…
Developers are turning to AI coding assistants to save time and speed up their work. But these tools can also…
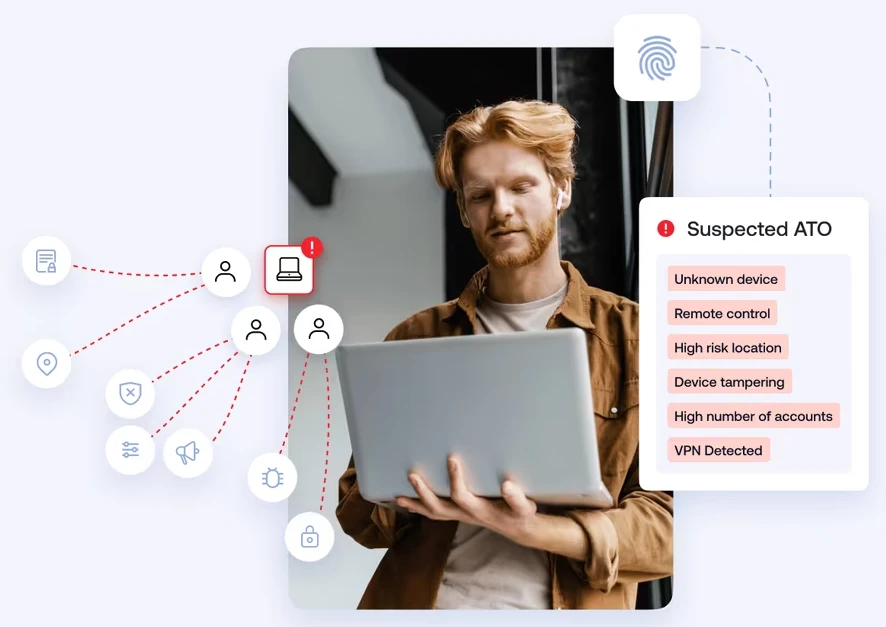
Sumsub is expanding its Fraud Prevention solution with advanced Device Intelligence, enhanced by the Fingerprint platform. Designed to identify threats before…
NIST and the University of Colorado Boulder have created a public service that delivers random numbers using quantum mechanics. Called…
When CISOs think about risk, they usually think about cloud platforms, laptops, and data centers. But live events like conferences,…
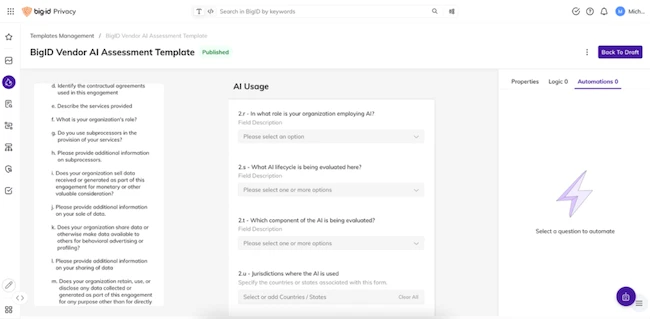
BigID launched Vendor AI Assessment, a solution designed to help organizations identify, evaluate, and manage the risks introduced by third-party…
In this Help Net Security interview, Paolo del Mundo, Director of Application and Cloud Security at The Motley Fool, discusses…
Cybersecurity threats are growing more complex, and domain-based attacks are at the center of this shift. CSC’s CISO Outlook 2025…