Category: HelpnetSecurity
CISO Nightfall AI | USA | On-site – View job details As a CISO, you will own and continuously evolve…
Vulnerabilities affecting the SinoTrack GPS tracking platform may allow attackers to keep tabs on vehicles’ location and even perform actions…
The UK government has appointed Blaise Florence Metreweli as the next Chief of the Secret Intelligence Service (SIS), also known…
Law enforcement authorities across Europe have dismantled Archetyp Market, the most enduring dark web drug market, following a large-scale operation…
Getting a call saying a family member has been kidnapped is terrifying. Fear and panic take over, making it hard…
In this Help Net Security interview, Rich Friedberg, CISO at Live Oak Bank, discusses how banks can better align cybersecurity…
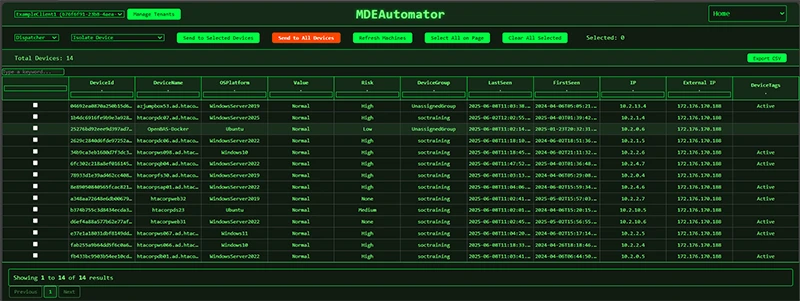
Managing endpoints and responding to security incidents in Microsoft Defender for Endpoint (MDE) can be time-consuming and complex. MDEAutomator is…
Kali Linux has long been the go-to operating system for penetration testers and security professionals, and Learning Kali Linux, 2nd…
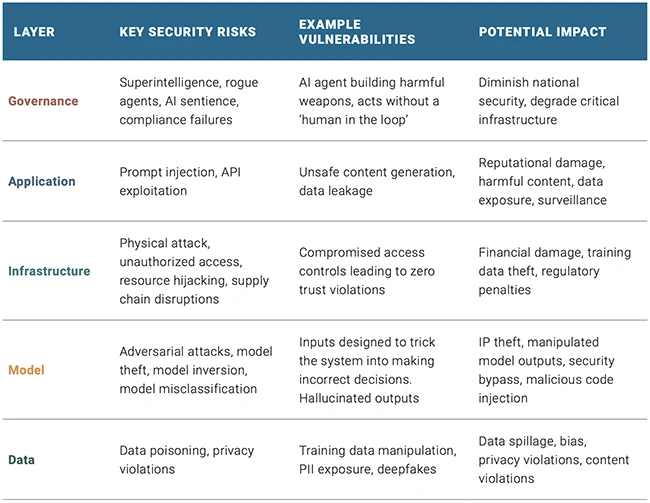
As AI spreads, so do the risks. Security leaders are being asked to protect systems they don’t fully understand yet,…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Microsoft fixes zero-day exploited for…
OffSec has released Kali Linux 2025.2, the most up-to-date version of the widely used penetration testing and digital forensics platform….
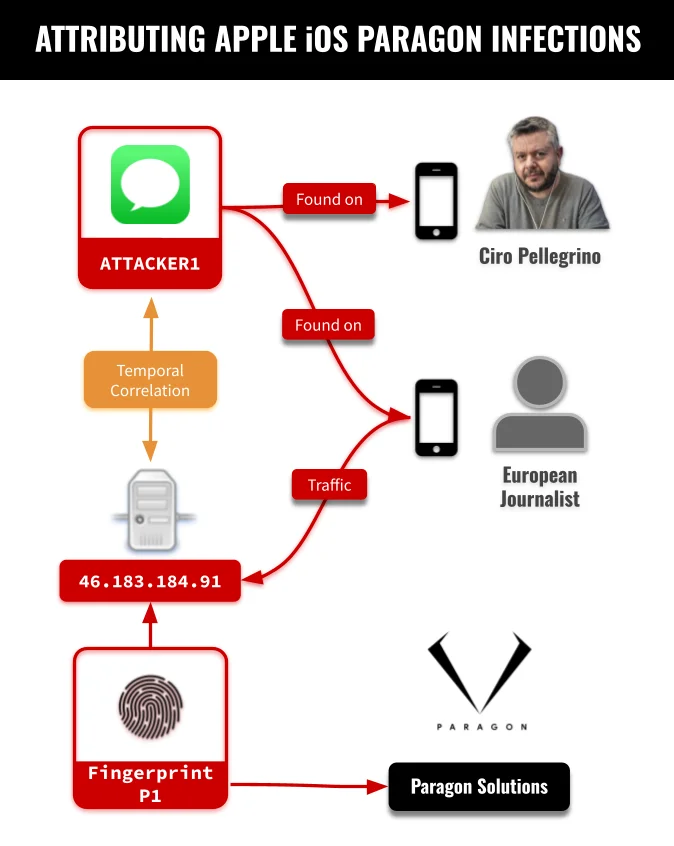
A zero-click attack leveraging a freshly disclosed Messages vulnerability (CVE-2025-43200) has infected the iPhones of two European journalists with Paragon’s…