Category: HelpnetSecurity
StackHawk announced Sensitive Data Identification to give security teams visibility into high-risk APIs across thousands of code repositories within an…
Here’s a look at the most interesting products from the past week, featuring releases from Contrast Security, Cymulate, Lemony, SpecterOps,…
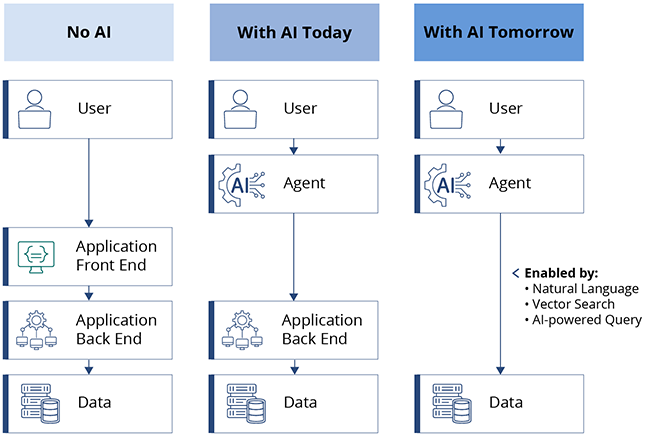
GenAI has been the star of the show lately. Tools like ChatGPT impressed everyone with how well they can summarize,…
In this Help Net Security interview, Amichai Shulman, CTO at Nokod Security, discusses how the abstraction layer in no-code environments…
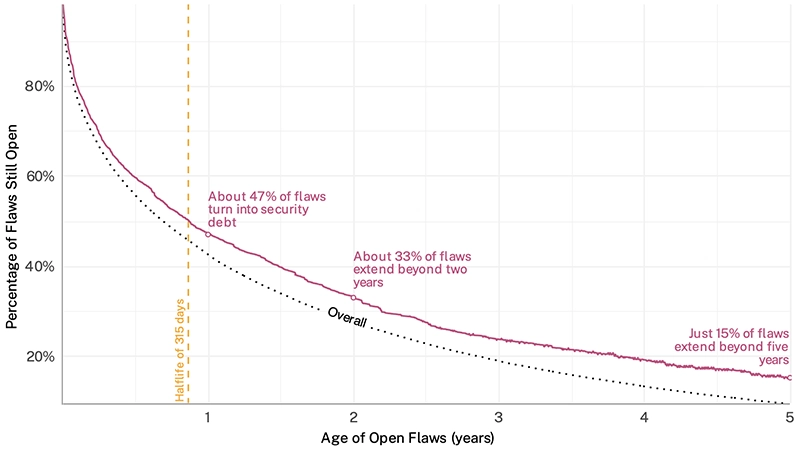
78% of public sector organizations are operating with significant security debt, flaws left unaddressed for more than a year, according…
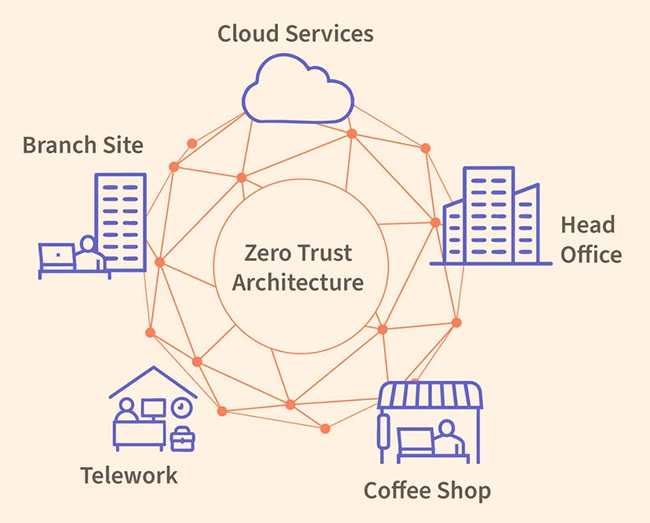
The National Institute of Standards and Technology (NIST) has released a new guide that offers practical help for building zero…
Attackers are using the TeamFiltration pentesting framework to brute-force their way into Microsoft Entra ID (formerly Azure AD) accounts, Proofpoint…
The LockBit ransomware-as-a-service (RaaS) operation has netted around $2.3 million USD within 5 months, the data leak stemming from the…
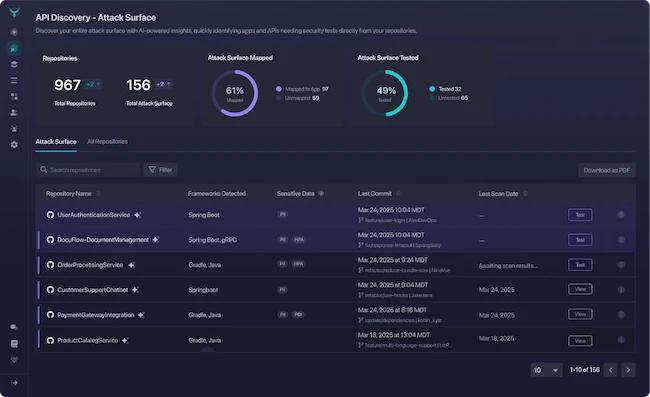
In this Help Net Security interview, Joni Klippert, CEO of StackHawk, discusses why API visibility is a major blind spot…
Lemony announced its on-premise artificial intelligence solution that is redefining how organizations deploy generative AI. Lemony’s secure, hardware-based node offers…
A cybersecurity hobbyist has built a compact, foldable mobile hacking rig that runs Kali NetHunter on a Google Pixel 3…
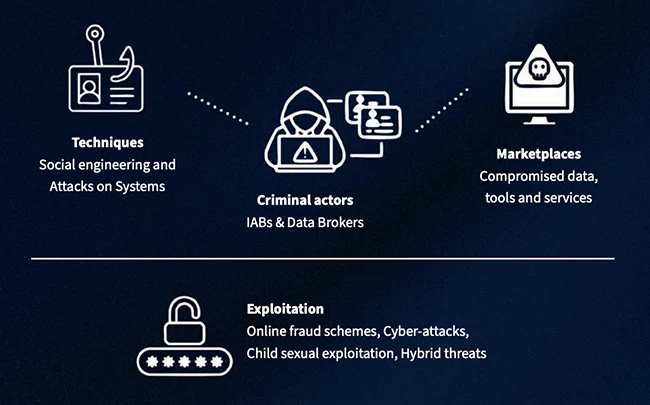
Cybercriminals are stealing data and running full-scale businesses around it. Europol’s latest Internet Organised Crime Threat Assessment (IOCTA) report reveals…