Category: HelpnetSecurity
With an exploit for a critical Roundcube vulnerability (CVE-2025-49113) being offered for sale on underground forums and a PoC exploit…
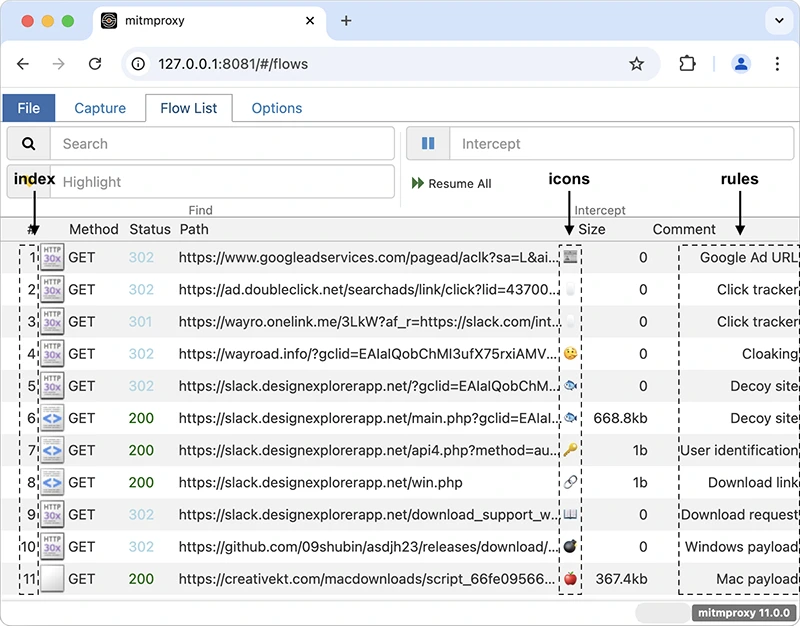
fiddleitm is an open-source tool built on top of mitmproxy that helps find malicious web traffic. It works by checking…
In this Help Net Security interview, Renana Friedlich-Barsky, EVP and CISO at LPL Financial, discusses how threat actors are targeting…
The threat landscape in the bioeconomy is different from what most CISOs are used to. It includes traditional risks like…
Using the MITRE ATT&CK framework as a baseline, organizations are generally improving year-over-year in understanding security information and event management…
In just 12 months, attackers attempted to steal more than $300 million via vendor email compromise (VEC), with 7% of…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: June 2025 Patch Tuesday forecast:…
Millions of Internet-of-Things (IoT) devices running the open-source version of the Android operating system are part of the Badbox 2.0…
Approximately 145 darknet and conventional internet domains, along with cryptocurrency funds linked to the BidenCash marketplace, have been seized by…
Ransomware breaches continue to rise even as fewer victims pay, according to a Delinea report. 69% of organizations globally have…
Microsoft has been busy releasing more out-of-band (OOB) patches than usual throughout May. The May Patch Tuesday release of updates…
In this Help Net Security interview, Benny Porat, CEO at Twine Security, discusses applying AI agents to security decisions. He…