Category: HelpnetSecurity
Patient data is often stored or processed outside the country where it was collected. When that happens, the data falls…
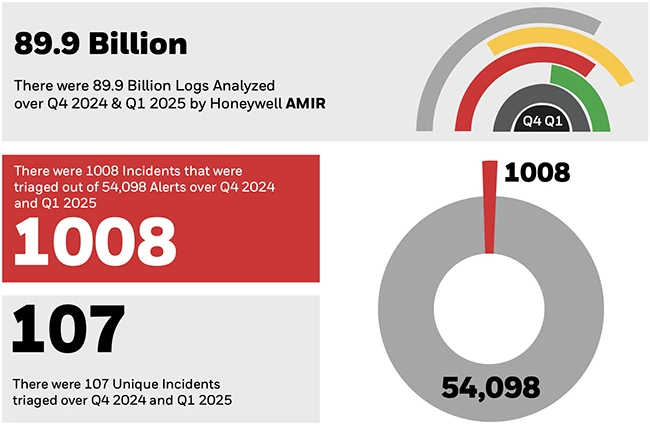
Ransomware, trojans, and malware delivered through USB devices are putting growing pressure on industrial systems, according to the Honeywell 2025…
Here’s a look at the most interesting products from the past week, featuring releases from Akamai, AttackIQ, Barracuda Networks, Bitdefender,…
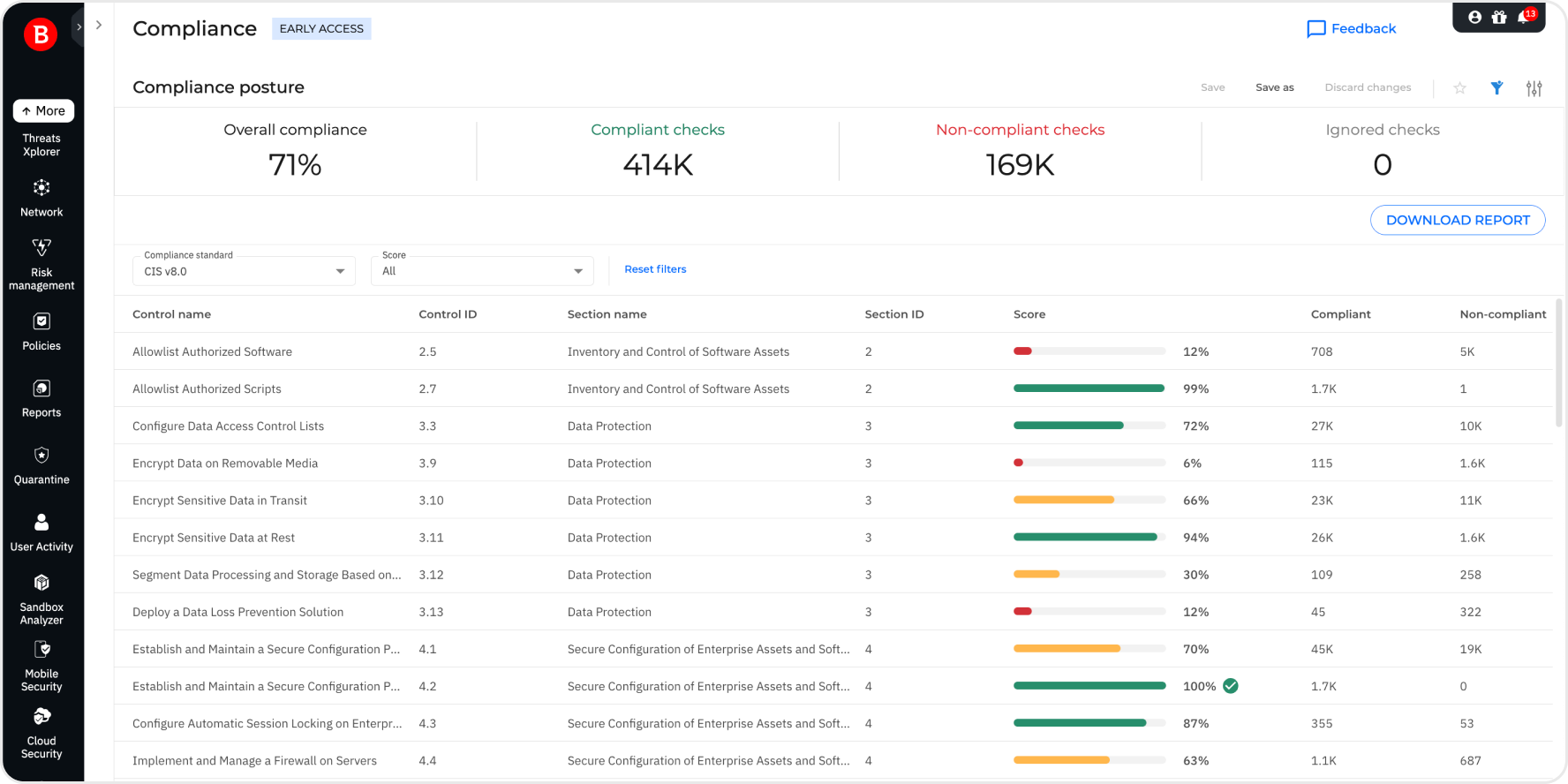
Bitdefender announced GravityZone Compliance Manager, a new addition to its GravityZone platform that helps organizations reduce the burden of compliance…
If it seems like scams are popping up everywhere lately, you’re not wrong. A new survey from Google shows most…
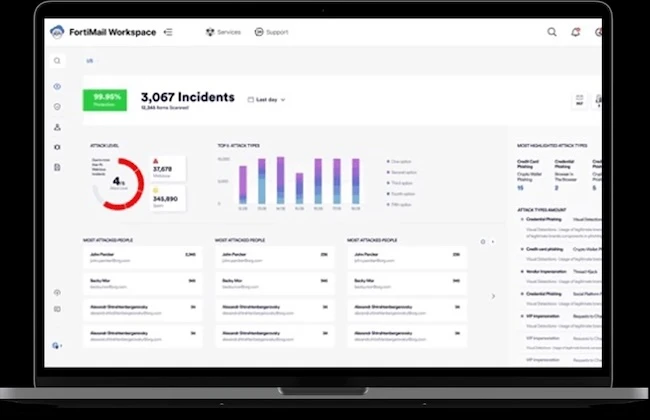
Fortinet has enhanced its data and productivity security portfolio, expanding FortiMail with the launch of the FortiMail Workspace Security suite. These…
Meta has released an open source AI tool called Automated Sensitive Document Classification. It was originally built for internal use…
Security teams are overwhelmed by a flood of alerts, most of which lack the context needed to accurately assess and…
32% of healthcare executives say their organization suffered a breach in the past 12 months, and 46% say they are…
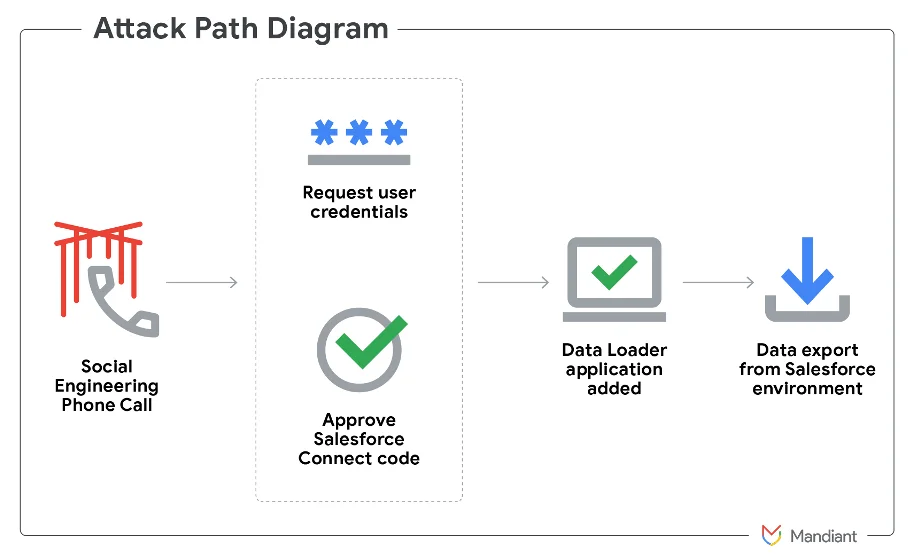
Over the past several months, a threat group has been actively breaching organizations’ Salesforce instances and exfiltrating customer and business…
Google has fixed two Chrome vulnerabilities, including a zero-day flaw (CVE-2025-5419) with an in-the-wild exploit. About CVE-2025-5419 CVE-2025-5419 is a…
Infosecurity Europe 2025 is a cybersecurity event taking place from June 3 to 5 in London. Help Net Security is…