Category: HelpnetSecurity
Vulnerabilities in open source software developed and used in-house by NASA could be exploited to breach their systems, claims Leon…
The Dutch intelligence and security services have identified a new Russia-affiliated threat group that has been breaching government organizations and…
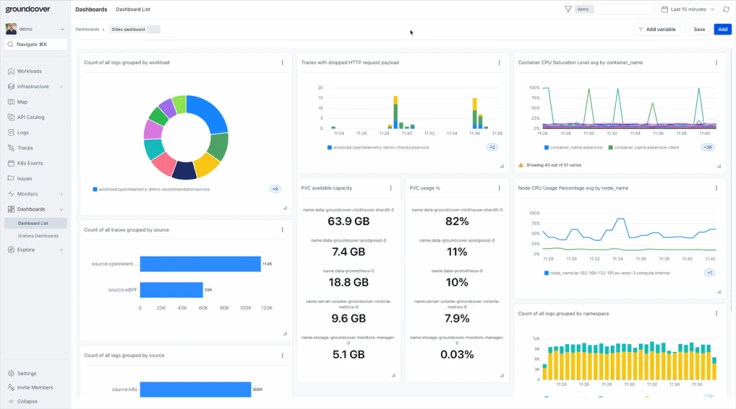
A new MCP server, faster than any other on the market, is launching today from groundcover, the eBPF-driven observability platform….
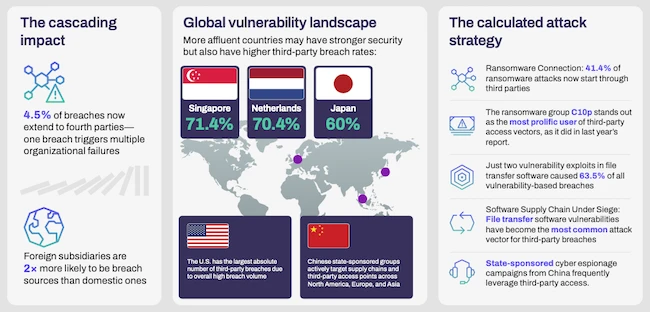
Security teams can no longer afford to treat third-party security as a compliance checkbox, according to SecurityScorecard. Traditional vendor risk…
In this Help Net Security interview, Michael Metzler, Vice President Horizontal Management Cybersecurity for Digital Industries at Siemens, discusses the…
Is the remote IT worker you recently hired really who he says he is? Fake IT workers are slipping into…
Application Security Engineer, SDO AppSec Amazon | EMEA | Hybrid – View job details As an Application Security Engineer, SDO…
NIST has introduced a new way to estimate which software vulnerabilities have likely been exploited, and it’s calling on the…
A wave of layoffs has swept through the tech industry, leaving IT teams in a rush to revoke all access…
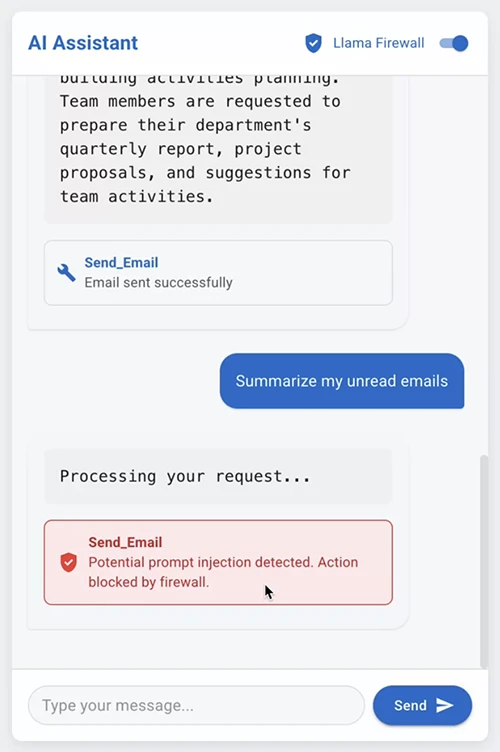
LlamaFirewall is a system-level security framework for LLM-powered applications, built with a modular design to support layered, adaptive defense. It…
Hybrid cloud infrastructure is under mounting strain from the growing influence of AI, according to Gigamon. Cyberthreats grow in scale…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Trojanized KeePass opens doors for…