Category: HelpnetSecurity
To meet today’s complex security requirements, organizations need solutions that are not only secure, but also practical and scalable. The…
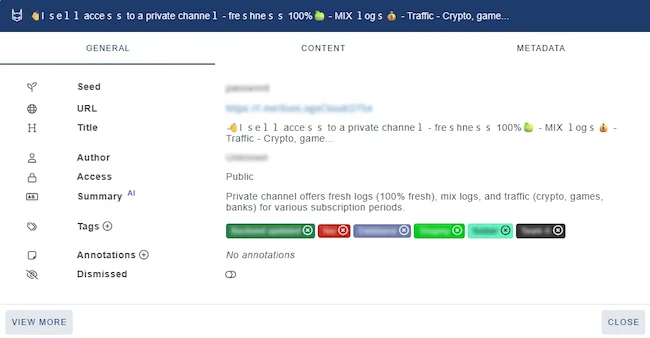
Outpost24 announced the addition of AI-enhanced summaries to the Digital Risk Protection (DRP) modules within its External Attack Surface Management…
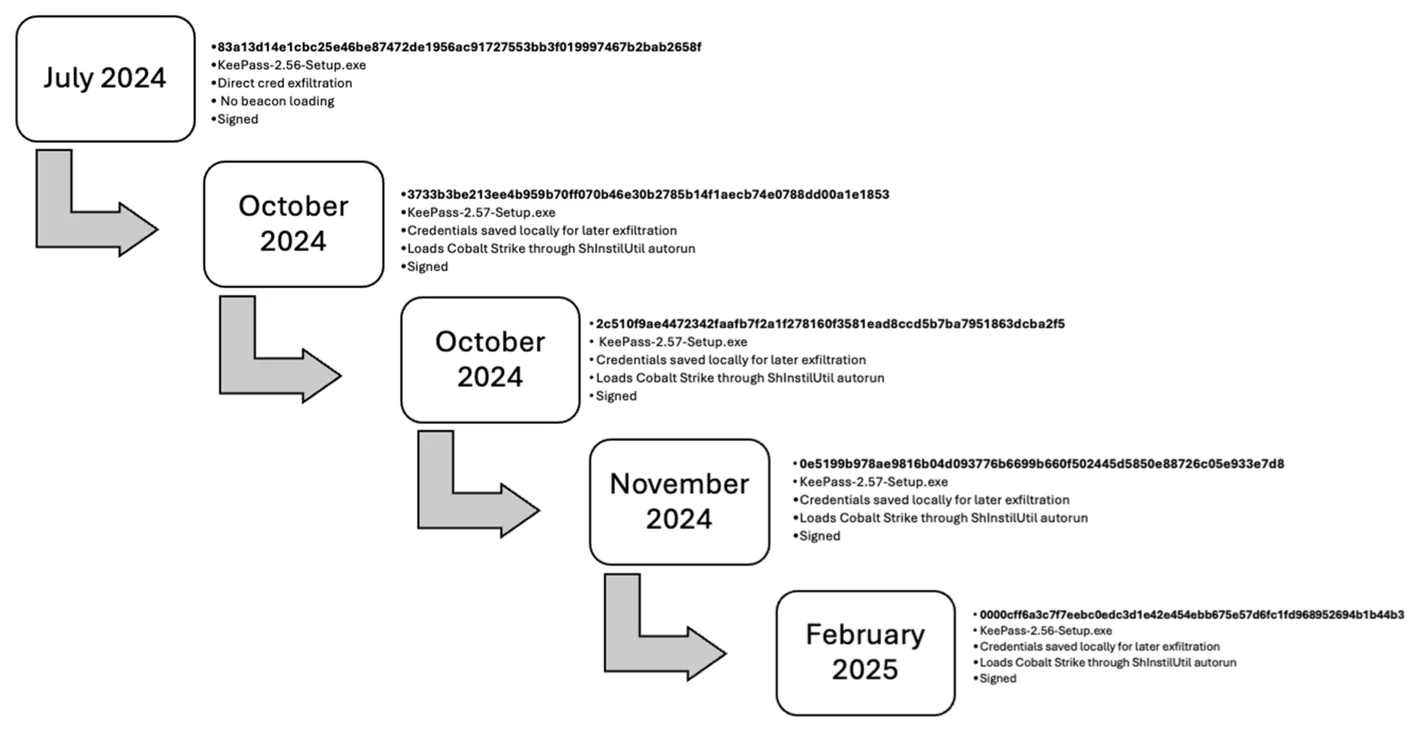
A suspected initial access broker has been leveraging trojanized versions of the open-source KeePass password manager to set the stage…
Microsoft has officially open-sourced the Windows Subsystem for Linux (WSL), closing the very first issue ever filed on the Microsoft/WSL…
CISO Vault Cloud | Australia | Hybrid – View job details As a CISO, you will lead company’s cloud security…
In this Help Net Security interview, Kunal Modasiya, SVP, Product Management, GTM, and Growth at Qualys, discusses recent Qualys research…
In this Help Net Security interview, Brooke Johnson, Chief Legal Counsel and SVP of HR and Security, Ivanti, explores the…
How sure are you that you can recognize an AI-cloned voice? If you think you’re completely certain, you might be…
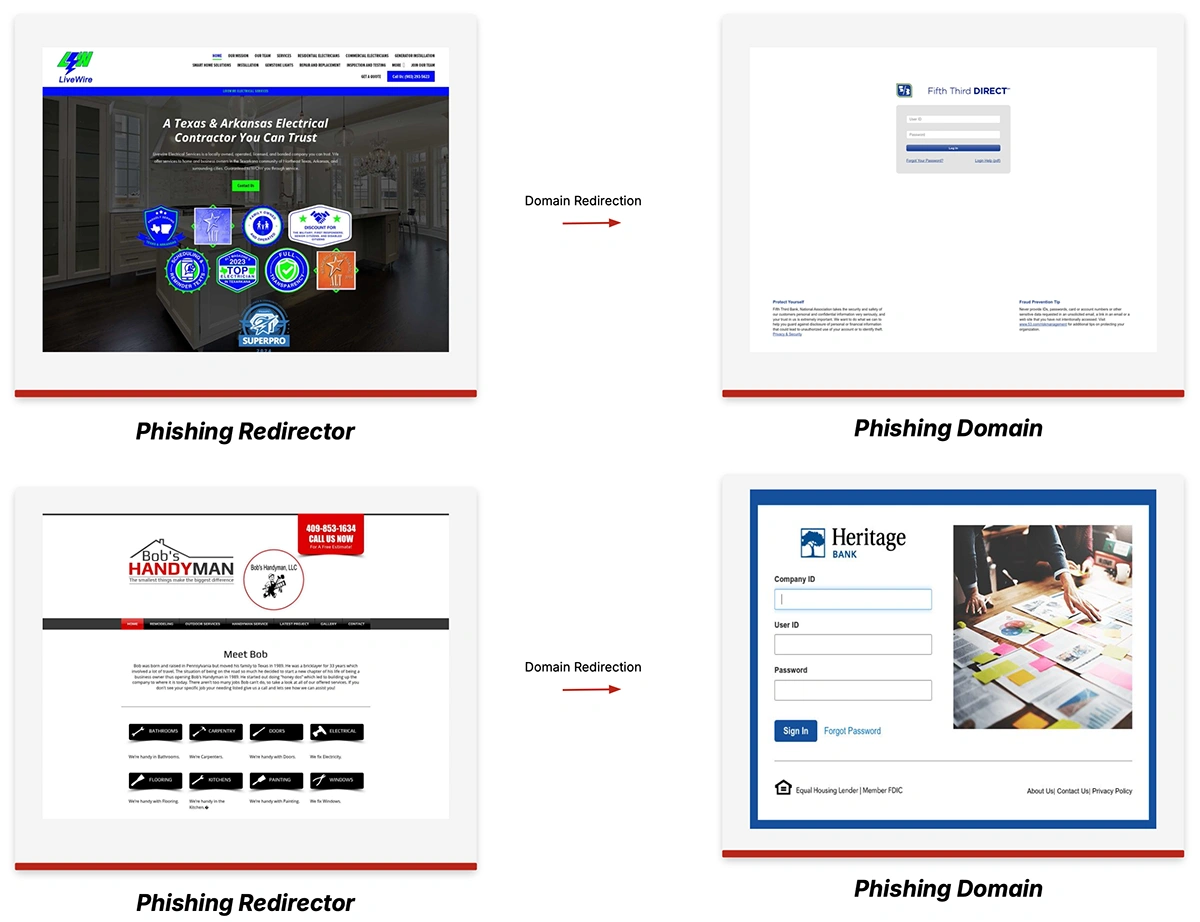
A phishing operation that targets corporate banking accounts across the globe has been analyzed in a new report by CTM360….
ThreatMark launched ScamFlag, a Generative AI-powered solution designed to protect digital banks and their customers from the scams and social…
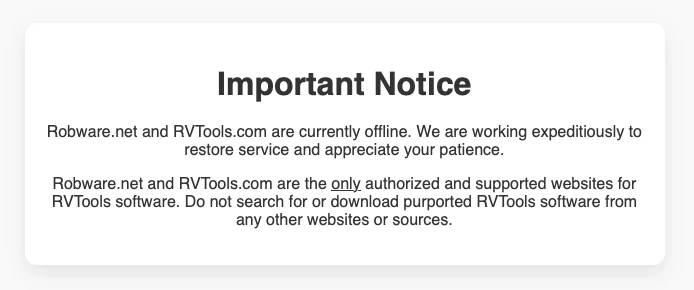
The official site for RVTools has apparently been hacked to serve a compromised installer for the popular utility, a security…
In this Help Net Security interview, Full Professor at University of Leuven, unpacks the European Commission’s encryption agenda, urging a…