Category: HelpnetSecurity
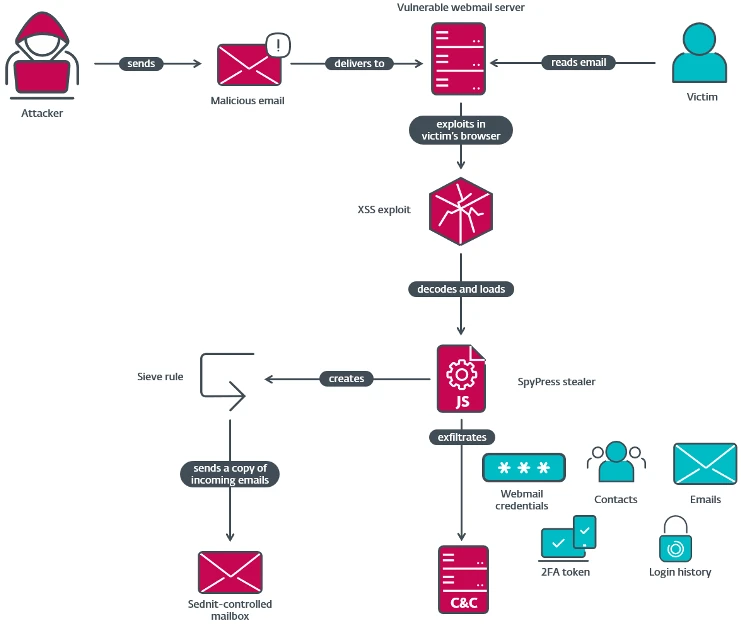
ESET researchers have uncovered RoundPress, a Russia-aligned espionage operation targeting webmail servers via XSS vulnerabilities. Behind it is most likely…
Cloud storage company Backblaze has released its Q1 2025 hard drive reliability report, which provides insights into the performance and…
In this Help Net Security interview, Anne Sofie Roed Rasmussen, CISO at Novonesis, discusses how a science-driven organization approaches cybersecurity,…
The Blockchain Security Standards Council (BSSC) launched its first four security standards, marking a significant milestone in the journey towards…
In this Help Net Security interview, Kim Crawley, cybersecurity expert and Professor at the Open Institute of Technology, discusses her…
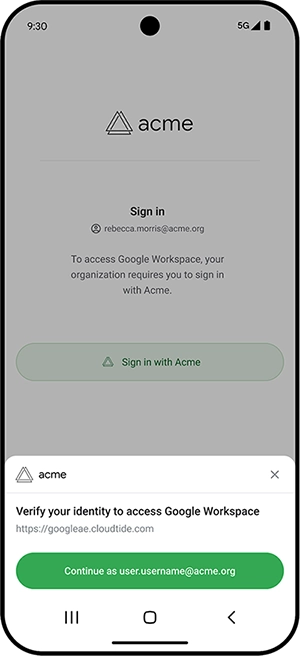
Google has introduced Device Trust from Android Enterprise, a new solution for making sure that private Android devices used for…
SecuX launched hardware-based cybersecurity solution tailored for small and medium-sized businesses (SMBs). At the core is Cyber Athena, an enterprise-grade…
The Nobara Project has released a new version of its Linux distribution, bringing updated packages, performance improvements, and a few…
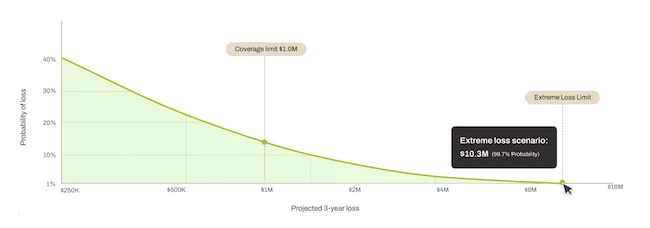
Resilience launched Cyber Risk Calculator to provide organizations with a financial snapshot of their cyber risk. The AI-powered tool provides security…
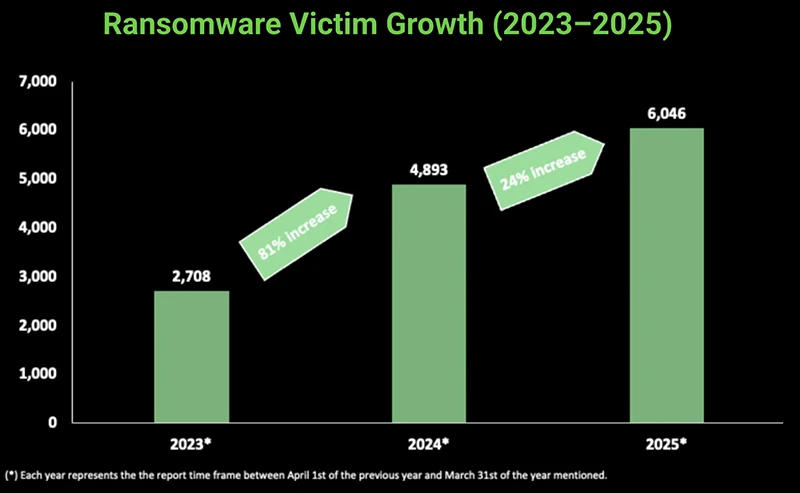
The fall of two of the most dominant ransomware syndicates, LockBit and AlphV, triggered a power vacuum across the cybercriminal…
Insider risk is not just about bad actors. Most of the time, it’s about mistakes. Someone sends a sensitive file…
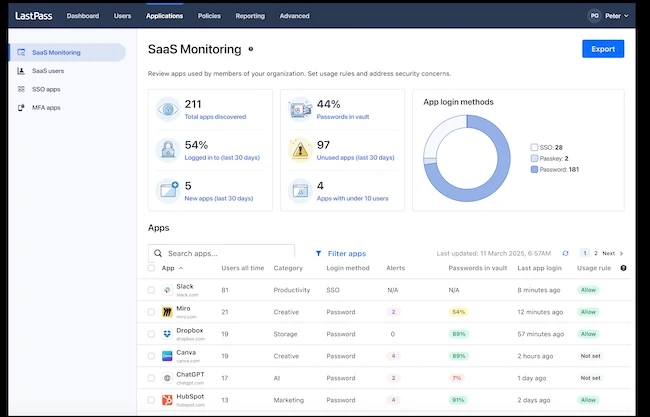
LastPass has announced the general availability of SaaS Monitoring. This new capability empowers organizations of all sizes to gain visibility…