Category: HelpnetSecurity
Here’s a look at the most interesting products from the past week, featuring releases from ProcessUnity, Searchlight Cyber, ServiceNow, and…
April was an event-filled month for cybersecurity. Patch Tuesday came to us quickly on April 8 – the earliest first…
If you’re trying to make sense of how to actually build AI agents, not just talk about them, AI Agents…
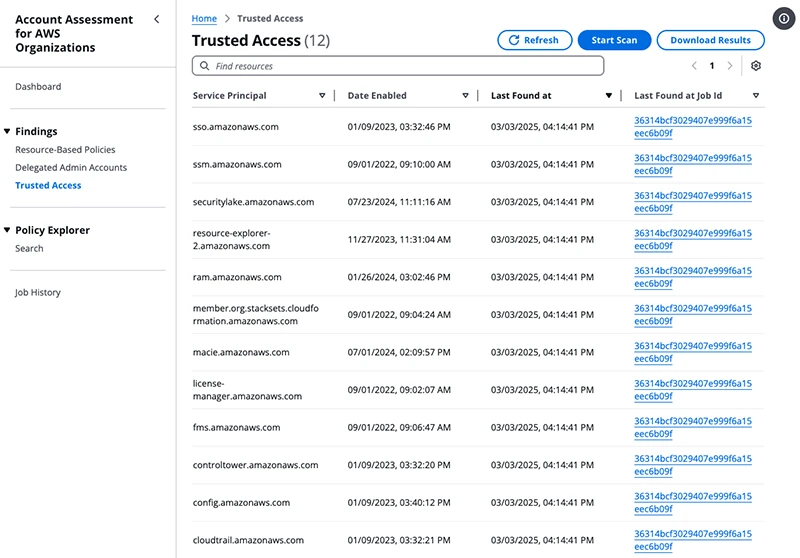
Managing multiple AWS accounts in an organization can get complicated, especially when trying to understand how services and permissions are…
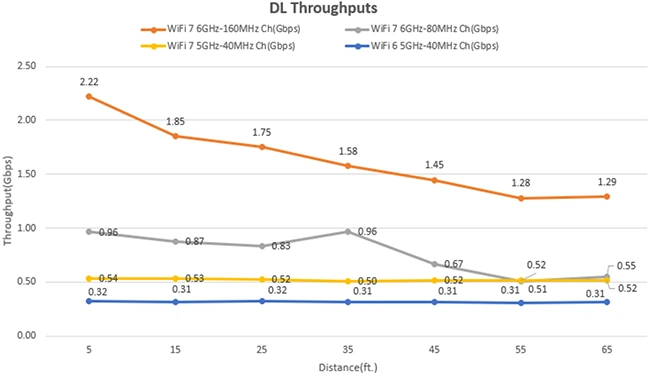
The next generation of wireless technology is getting a real-world test, and the results are promising. Recent trials led by…
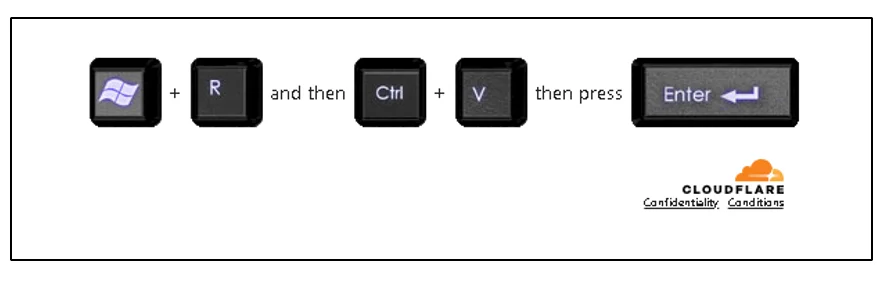
As new malware delivery campaigns using the ClickFix social engineering tactic are spotted nearly every month, it’s interesting to see…
SonicWall has fixed multiple vulnerabilities affecting its SMA100 Series devices, one of which (CVE-2025-32819) appears to be a patch bypass…
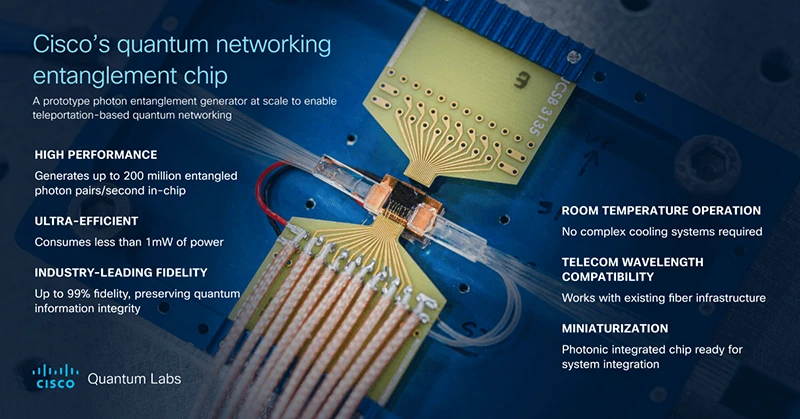
Cisco is making significant strides in quantum computing by focusing on quantum networking, aiming to bring practical applications closer to…
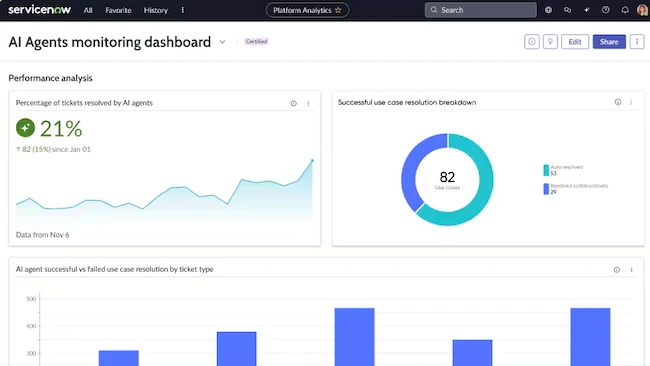
ServiceNow launched a new, agentic chapter in enterprise security and risk, introducing AI agents to power the rise of self-defending…
ProcessUnity introduced Evidence Evaluator, an generative AI that reduces the manual lift of assessing and validating third-party security controls. A…
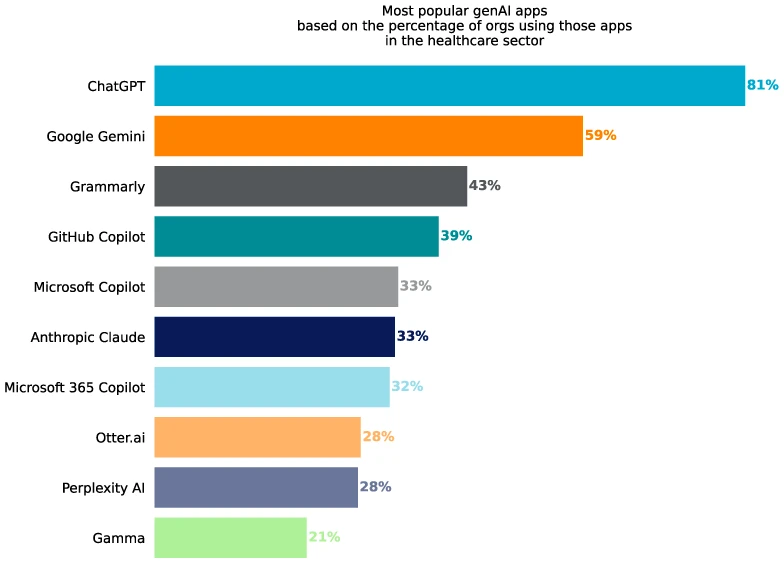
Healthcare organizations are facing a growing data security challenge from within, according to a new report from Netskope Threat Labs….
In this Help Net Security interview, Michael Pound, Associate Professor at the University of Nottingham shares his insights on the…