Category: HelpnetSecurity
The tech industry is experiencing significant layoffs, leaving thousands of IT and cybersecurity professionals in search of new employment opportunities….
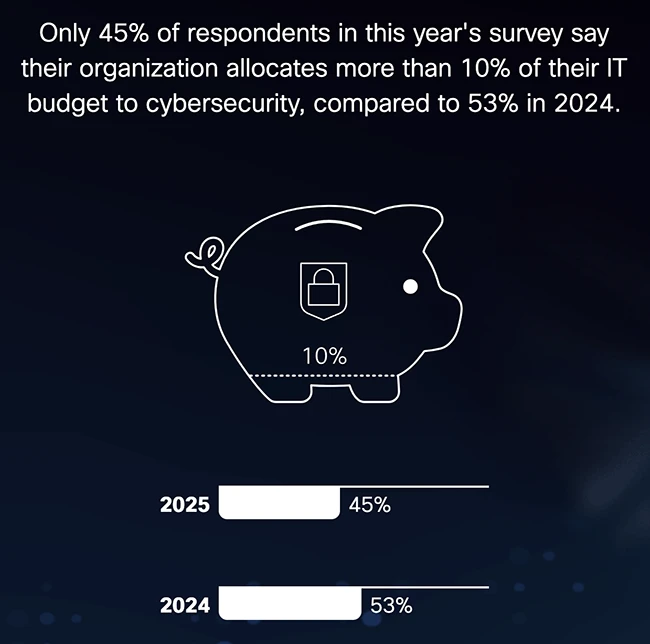
Only 4% of organizations worldwide have achieved the ‘mature’ level of readiness required to withstand cybersecurity threats, according to Cisco’s…
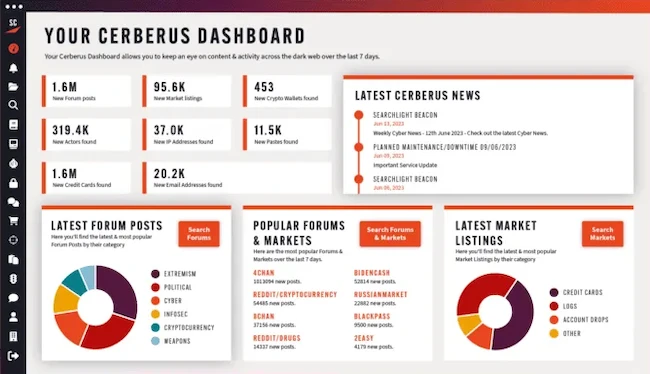
Searchlight Cyber has launched new AI capabilities within its dark web investigations platform, Cerberus. The new Cerberus AI Insights feature…
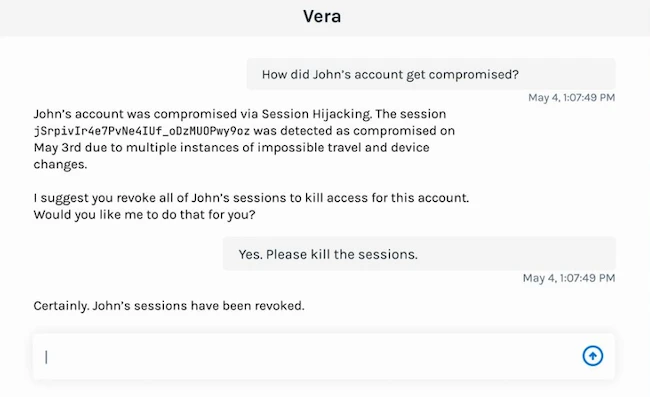
Verosint launched Vera, an agentic AI security analyst to transform how organizations detect, investigate, and respond to identity-based threats. Built…
WatchTowr researchers have released a proof-of-concept (PoC) exploit that chains two vulnerabilities in SysAid On-Prem – the self-hosted version of…
Google has released fixes for a bucketload of Android security vulnerabilities, including a FreeType flaw (CVE-2025-27363) that “may be under…
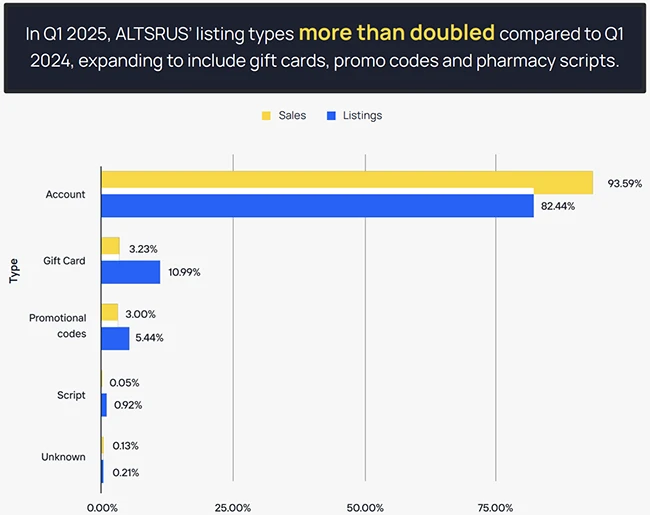
A new report from bot defense firm Kasada has exposed the growing threat of ALTSRUS, a fraud syndicate targeting some…
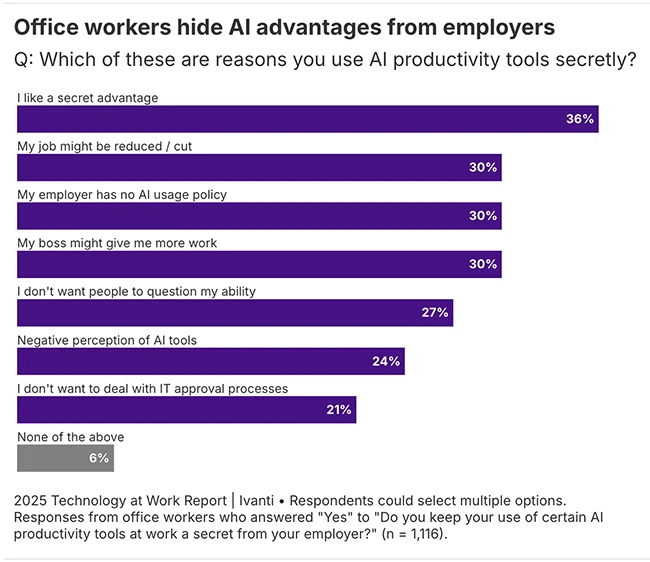
Employees are feeling heightened concerns around the use of technology to enhance productivity, as well as job dissatisfaction and a…
Application security is changing fast. In this Help Net Security interview, Loris Gutic, Global CISO at Bright, talks about what…
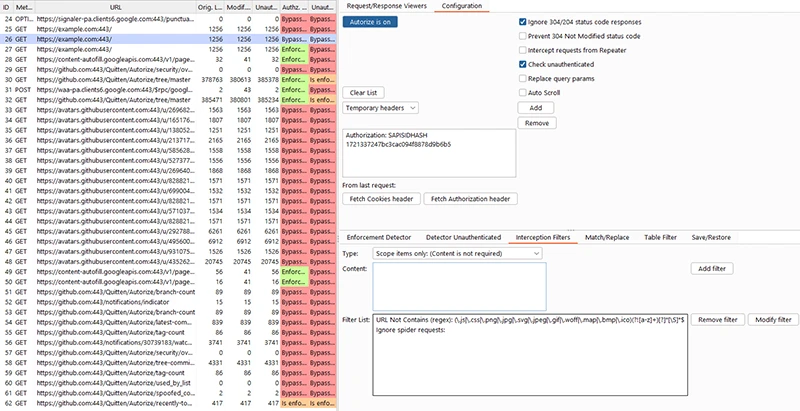
Autorize is an open-source Burp Suite extension that checks if users can access things they shouldn’t. It runs automatic tests…
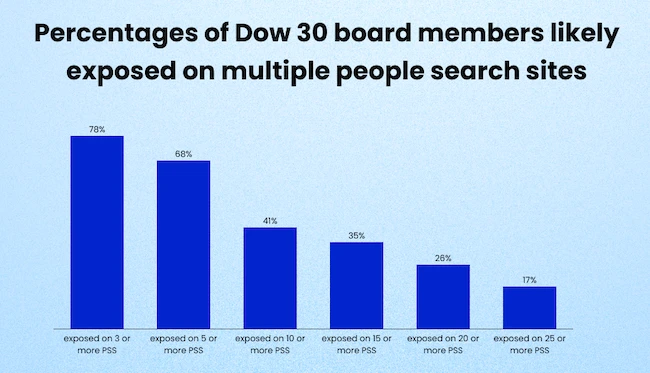
The personal information of 75% of corporate directors can be found on people search sites, according to Incogni. People search…
Whether your organization is already in the cloud or just starting to plan your migration, security is a top priority….