Category: HelpnetSecurity
Attackers have been using two previously known vulnerabilities (CVE-2024-38475, CVE-2023-44221) to compromise SonicWall secure mobile access devices, the vendor has…
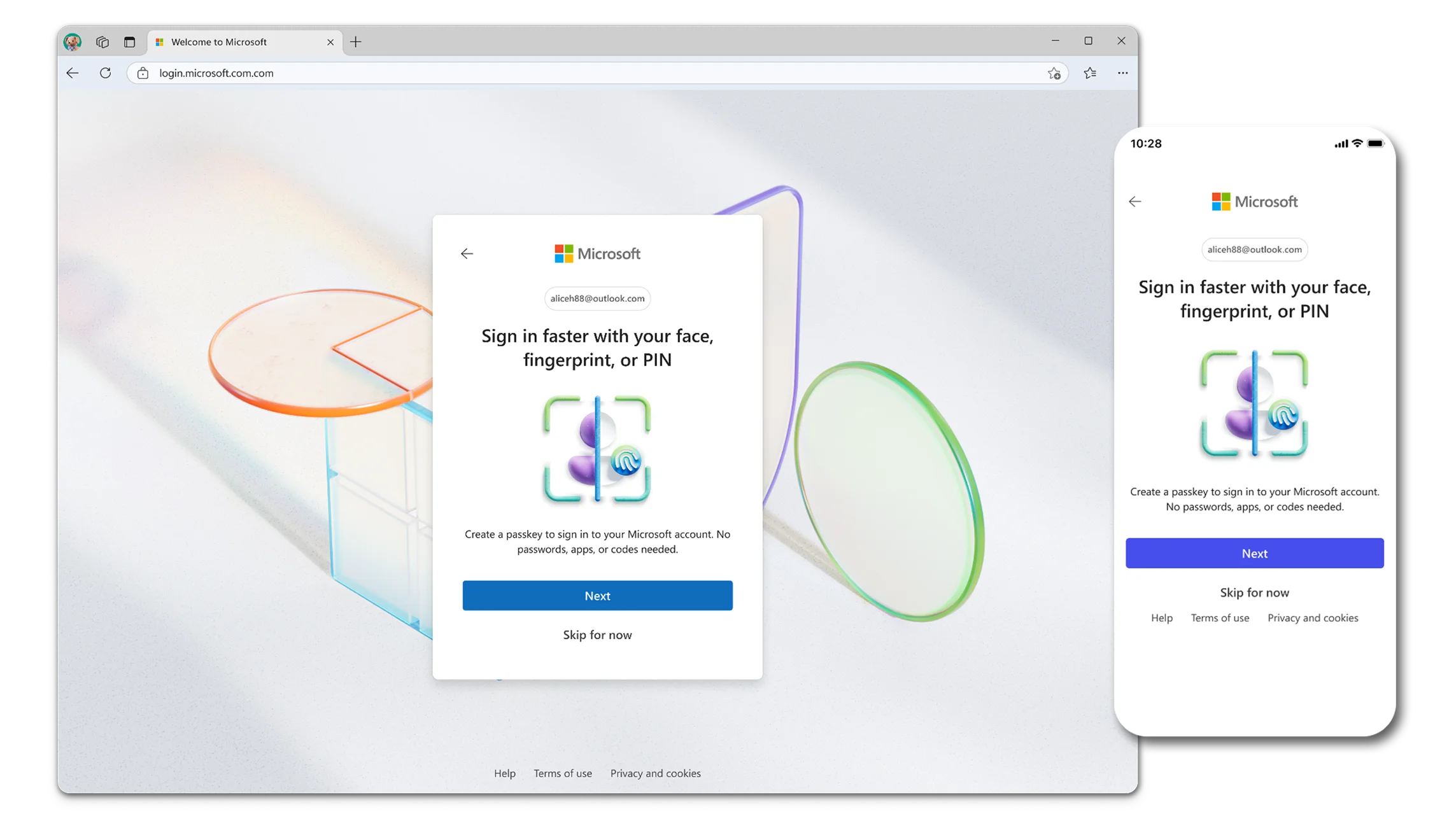
Microsoft is making new Microsoft accounts passwordless by default, the company has announced on Thursday, which marked this year’s World…
35% of Gen Z said they never or rarely update passwords after a data breach affecting one of their accounts,…
Threat actors are increasingly harnessing automation, commoditized tools, and AI to systematically erode the traditional advantages held by defenders, according…
Phone theft is a rising issue worldwide, and it’s more than just a property crime. It’s a serious cybersecurity threat….
Third-party risk management (TPRM) is compromised in many organizations because those holding the relationship with the third-party (relationship owners) don’t…
Here’s a look at the most interesting products from the past month, featuring releases from: 1touch.io, Abnormal AI, AppViewX, Arctic…
RSAC 2025 Conference is taking place at the Moscone Center in San Francisco. Help Net Security is on-site, and this…
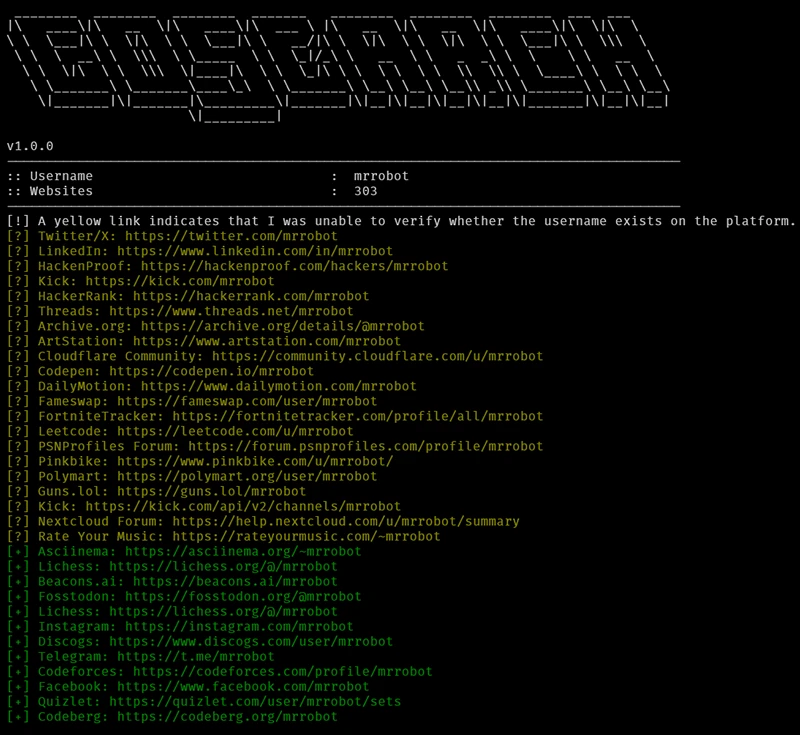
This month’s roundup features exceptional open-source cybersecurity tools that are gaining attention for strengthening security across various environments. GoSearch: Open-source…
In this Help Net Security interview, Steven Furnell, Professor of Cyber Security at the University of Nottingham, illustrates how small…
Machine identities are multiplying fast, and many organizations are struggling to keep up. In this Help Net Security interview, Wendy…
RSAC 2025 showcased a wave of innovation, with vendors unveiling technologies poised to redefine cybersecurity. From AI-powered defense to breakthroughs…