Category: HelpnetSecurity
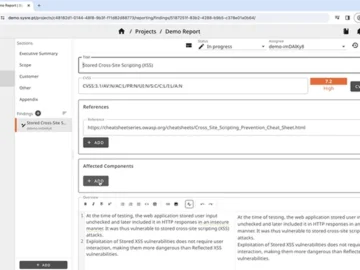
SysReptor is a customizable open-source penetration testing reporting platform built for pentesters, red teamers, and cybersecurity professionals. You can optimize…
While 4 out of 5 CEOs recognize AI’s potential, many worry gaps in their understanding will impact strategic decisions, risking…
February 2025 Patch Tuesday is here, and Microsoft has delivered fixes for 56 vulnerabilities, including two zero-days – CVE-2025-21418 and…
The Thai police has arrested four individuals suspected of being the leaders of the 8Base ransomware group and of stealing…
Users of iPhones and iPads that run iOS/iPadOS 18 and iPadOS 17 are urged to implement the latest updates to…
In this Help Net Security interview, Mike Calvi, CISO at Arvest Bank, discusses building a strong cybersecurity culture within the…
Inside Cyber Warfare, 3rd Edition by Jeffrey Caruso explores how nation-states, corporations, and hackers engage in digital warfare. It offers…
Apple’s AirTags are a convenient way to track personal items like keys and bags, but they also raise concerns about…
Application Offensive Security Consultant Sharp Decisions | USA | On-site – View job details As an Application Offensive Security Consultant,…
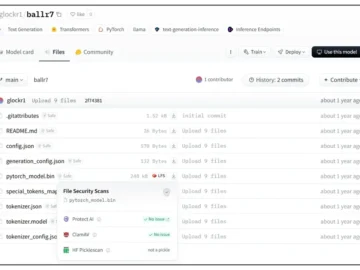
Researchers have spotted two machine learning (ML) models containing malicious code on Hugging Face Hub, the popular online repository for…
In this Help Net Security interview, Mateusz Łabuz, researcher at the IFSH, discusses the balance between using AI for personalized…
The new year has started with a whirlwind of activity, and one of the hottest topics in the news is…