Category: HelpnetSecurity
From a psychological standpoint, we all crave attention, and likes and comments fuel that need, encouraging us to share even…
Packed with real-world scenarios, hands-on techniques, and insights into widely used tools, the third edition of the bestselling Ultimate Kali…
WhatsApp users are urged to update the Windows client app to plug a serious security vulnerability (CVE-2025-30401) that may allow…
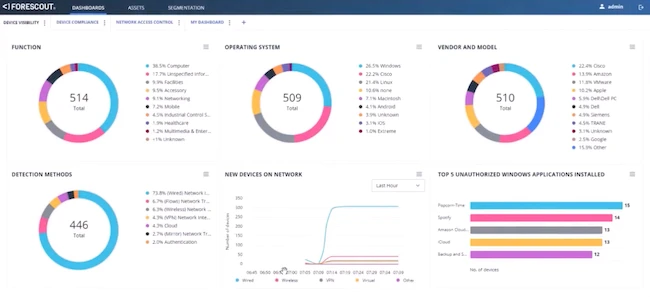
Forescout announced new Forescout eyeScope cloud visibility and monitoring solution, expanding the Forescout 4D Platform to the cloud. Forescout also…
Enzoic for AD Lite Password Auditor is an innovative tool designed to integrate with an organization’s Active Directory environment seamlessly….
A critical RCE vulnerability (CVE-2025-30406) affecting the Gladinet CentreStack file-sharing/remote access platform has been added to CISA’s Known Exploited Vulnerabilities…
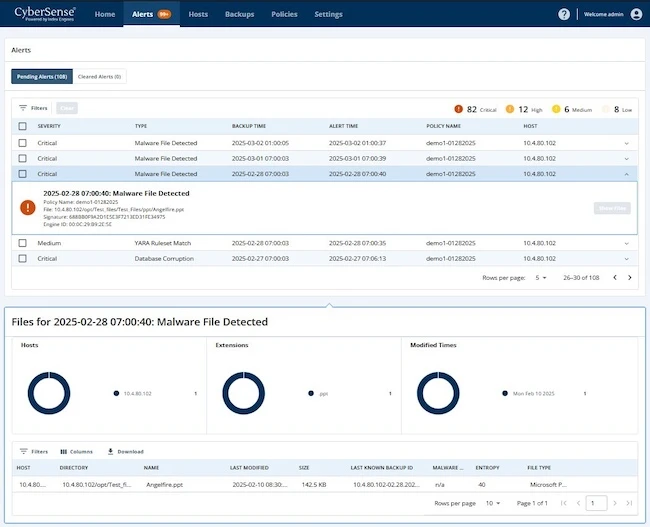
Index Engines announced CyberSense 8.10, fully integrated with Dell PowerProtect Cyber Recovery, which provides new capabilities to enhance cyber resilience…
The OpenSSL Project has released version 3.5.0 of its widely used open-source cryptographic library, introducing new features and notable changes…
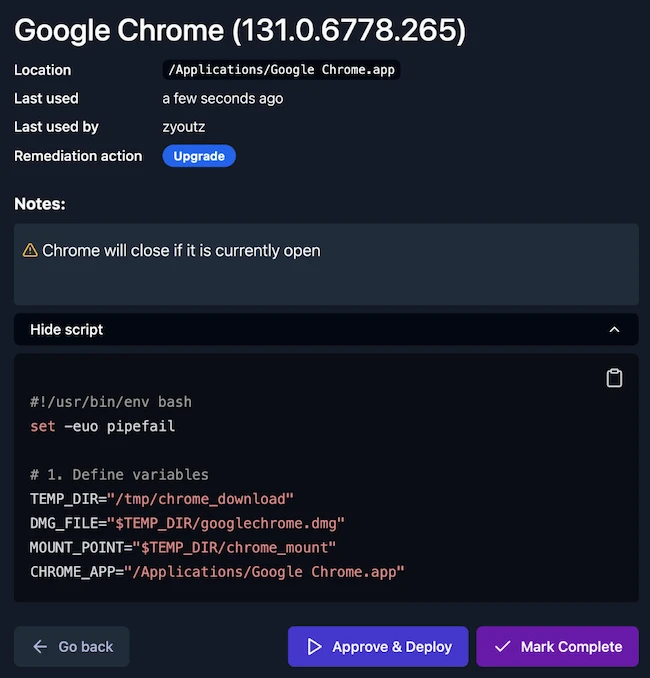
Furl launched AI-powered remediation platform, designed to revolutionize how security teams tackle the ever-growing backlog of endpoint and server vulnerabilities….
In this Help Net Security interview, Kevin Serafin, CISO at Ecolab, discusses aligning security strategy with long-term business goals, building…
Cyber threats aren’t going away, and CISOs know prevention isn’t enough. Being ready to respond is just as important. Cyber…
APTRS is an open-source reporting tool built with Python and Django. It’s made for penetration testers and security teams who…