Category: HelpnetSecurity
In this Help Net Security interview, Arun Shrestha, CEO at BeyondID, discusses how AI is transforming secure access management for…
YES3 Scanner is an open-source tool that scans and analyzes 10+ different configuration items for your S3 buckets in AWS….
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Attackers are probing Palo Alto…
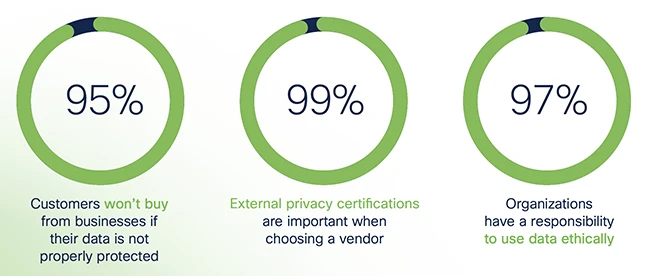
Cisco released its 2025 Data Privacy Benchmark Study. The report looks at global trends in data privacy and how they…
In this Help Net Security interview, Curtis Simpson, CISO and Chief Advocacy Officer at Armis, discusses how CISOs can balance…
Microsoft is continuing to build on their AI cybersecurity strategy and this month announced the introduction of new agents in…
Technology has entered all areas of life, and our cars are no exception. They have become computers on wheels, equipped…
Here’s a look at the most interesting products from the past week, featuring releases from 1touch.io, Bitsight, Bluefin, CyberQP, and…
A suspected Chinese APT group has exploited CVE-2025-22457 – a buffer overflow bug that was previously thought not to be…
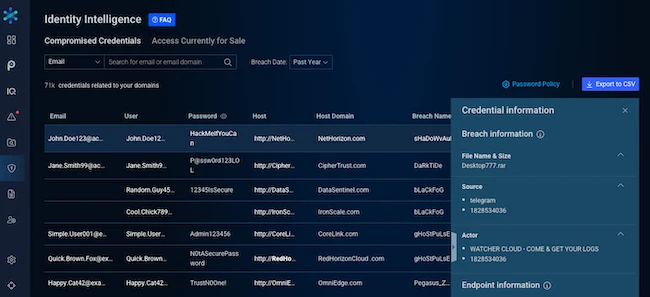
Bitsight launched Bitsight Identity Intelligence, a new, standalone threat intelligence module designed to help security teams detect compromised credentials, prevent…
CVE-2024-20439, a static credential vulnerability in the Cisco Smart Licensing Utility, is being exploited by attackers in the wild, CISA…
Steam was the most imitated brands by phishers in the first quarter of 2025, followed by Microsoft and Facebook/Meta, Guardio…