Category: HelpnetSecurity
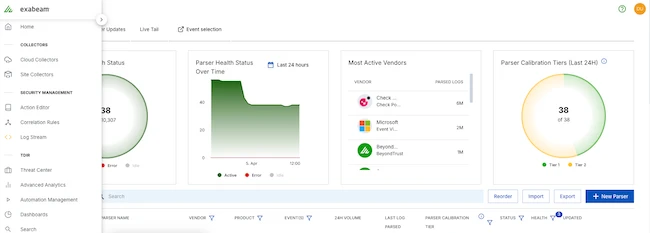
Exabeam unveiled Exabeam Nova, an autonomous AI agent delivering actionable intelligence that enables security teams to respond faster to incidents,…
99% of email threats reaching corporate user inboxes in 2024 were response-based social engineering attacks or contained phishing links, according…
In this Help Net Security interview, Aaron Weismann, CISO at Main Line Health, discusses the growing ransomware threat in healthcare…
BlueToolkit is an open-source tool that helps find security flaws in Bluetooth Classic devices. It runs known and custom exploits…
The Internet of Things (IoT) has become a major part of daily life. Smartphones, smart thermostats, security cameras, and other…
Exploitation attempts targeting the CVE-2025-2825 vulnerability on internet-facing CrushFTP instances are happening, the Shadowserver Foundation has shared on Monday, and…
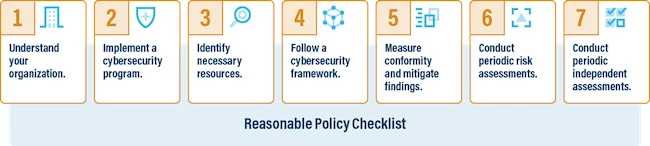
If you do business in the United States, especially across state lines, you probably know how difficult it is to…
With global tensions climbing, cyber attacks linked to nation-states and their allies are becoming more common, sophisticated, and destructive. For…
While cybercriminals are often in the spotlight, one of the most dangerous threats to your company might be hiding in…
In this Help Net Security interview, Yinglian Xie, CEO at DataVisor, explains how evolving fraud tactics require adaptive, AI-driven prevention…
Cloud Security Engineer Fexco | Ireland | Hybrid – View job details As a Cloud Security Engineer, you will design…
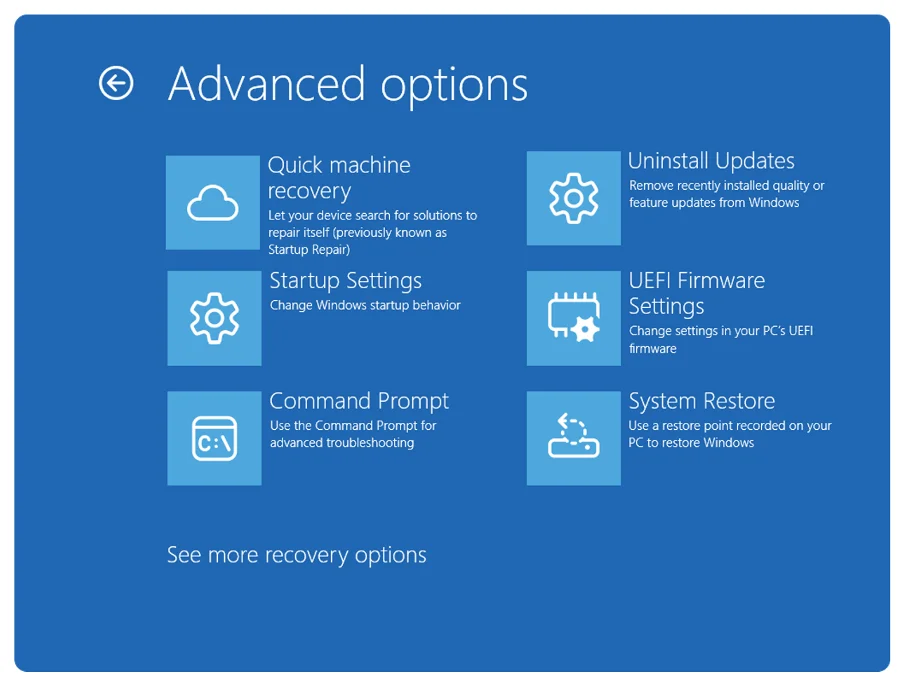
Microsoft has rolled out quick machine recovery, a new Windows feature aimed at preventing prolonged widespread outages like the one…