Category: HelpnetSecurity
A critical zero-day vulnerability (CVE-2025-23006) affecting SonicWall Secure Mobile Access (SMA) 1000 Series appliances is being exploited by attackers. “We…
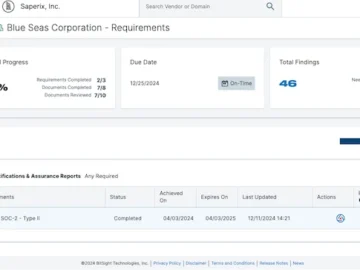
Bitsight unveiled Instant Insights, a new offering from the Bitsight IQ suite of AI-based capabilities. The new feature leverages generative…
In this Help Net Security interview, Tomer Shloman, Sr. Security Researcher at Trellix, talks about attack attribution, outlines solutions for…
The Web Cache Vulnerability Scanner (WCVS) is an open-source command-line tool for detecting web cache poisoning and deception. The scanner,…
This article gathers excerpts from multiple reports, presenting statistics and insights that may be valuable for CISOs, helping them with…
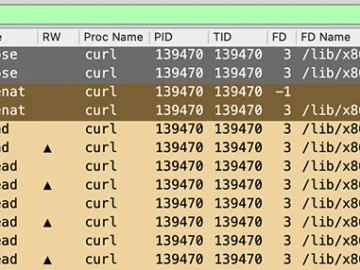
Stratoshark is an innovative open-source tool that brings Wireshark’s detailed network visibility to the cloud, providing users with a standardized…
Researchers have uncovered two Mirai-based botnets harnessing Internet of Things (IoT) devices to DDoS target organizations around the world. The…
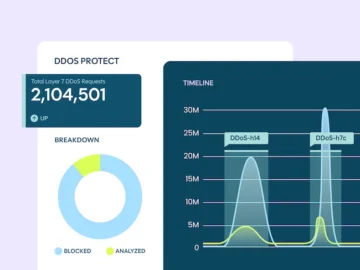
DataDome unveiled DDoS Protect, a cloud-based service designed to block distributed denial-of-service (DDoS) attack traffic at the edge before it…
Lookout announced their new Lookout Mobile Intelligence Application Programming Interfaces (APIs), exponentially expanding the scope of visibility into enterprise mobile…
Despite last week’s confirmation of and warnings about long-standing exploitation of CVE-2024-55591, a critical vulnerability affecting Fortinet Fortigate firewalls, too…
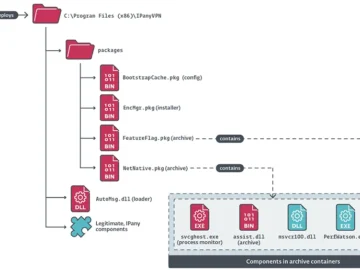
ESET researchers have uncovered a supply chain attack targeting a South Korean VPN provider, carried out by PlushDaemon, a newly…
In this Help Net Security interview, Gerald Beuchelt, CISO at Acronis, discusses common backup strategy pitfalls, reasons for backup failures,…