Category: HelpnetSecurity
Security concerns around cloud environments has prompted 44% of CISOs to change cloud service provider, according to Arctic Wolf. This…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Critical Veeam Backup & Replication…
Enterprises lack visibility into their own data, creating security risks that are compounding as organizations and their employees increase AI…
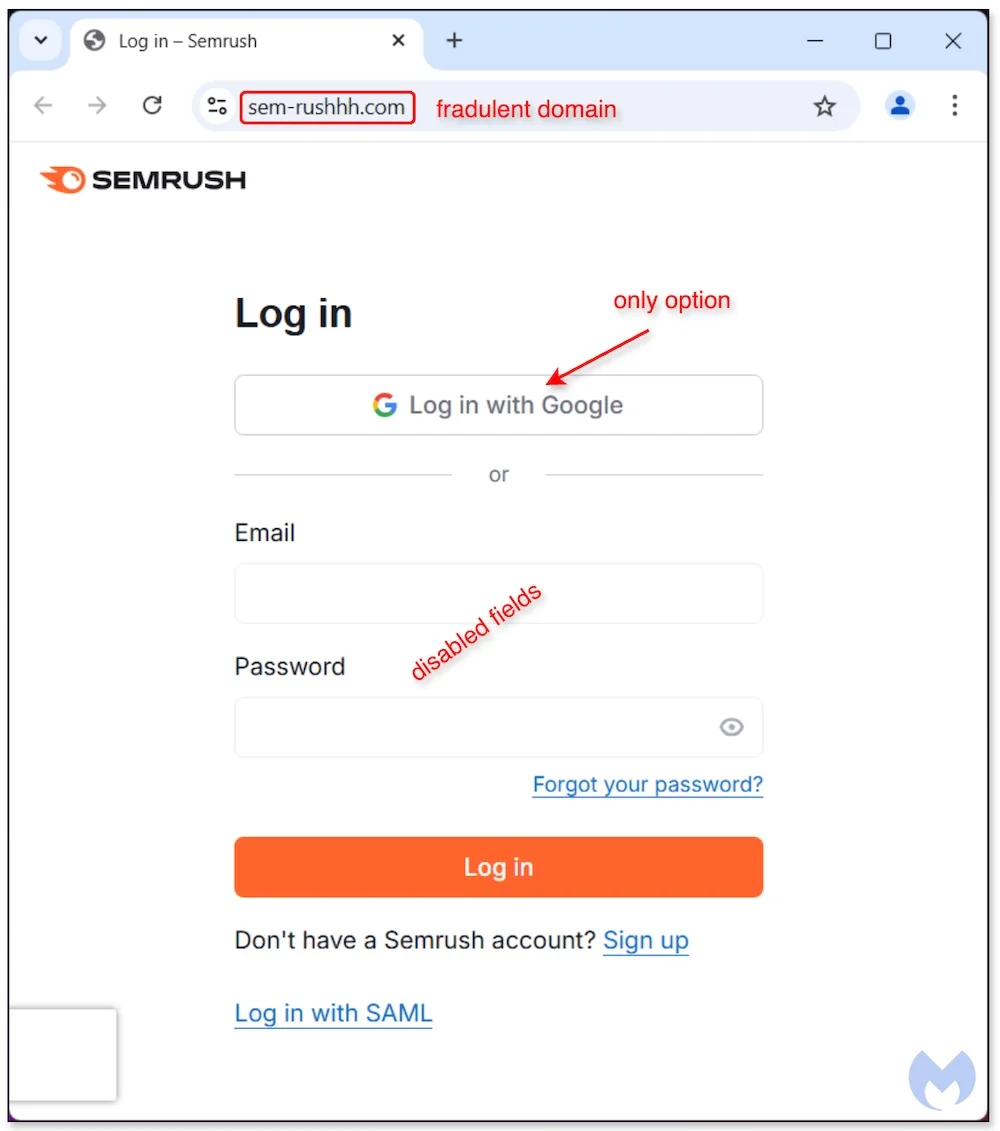
Cyber crooks are exploiting users’ interest in Semrush, a popular SEO, advertising, and market research SaaS platform, to steal their…
Ransomware is the top predicted threat for 2025, which is especially concerning given 38% of security professionals say ransomware will…
AI-powered phishing emails, deepfake phone calls, and fake tax prep websites are making tax scams more convincing and costly than…
Here’s a look at the most interesting products from the past week, featuring releases from 1Kosmos, Cloudflare, Cytex, Keysight Technologies,…
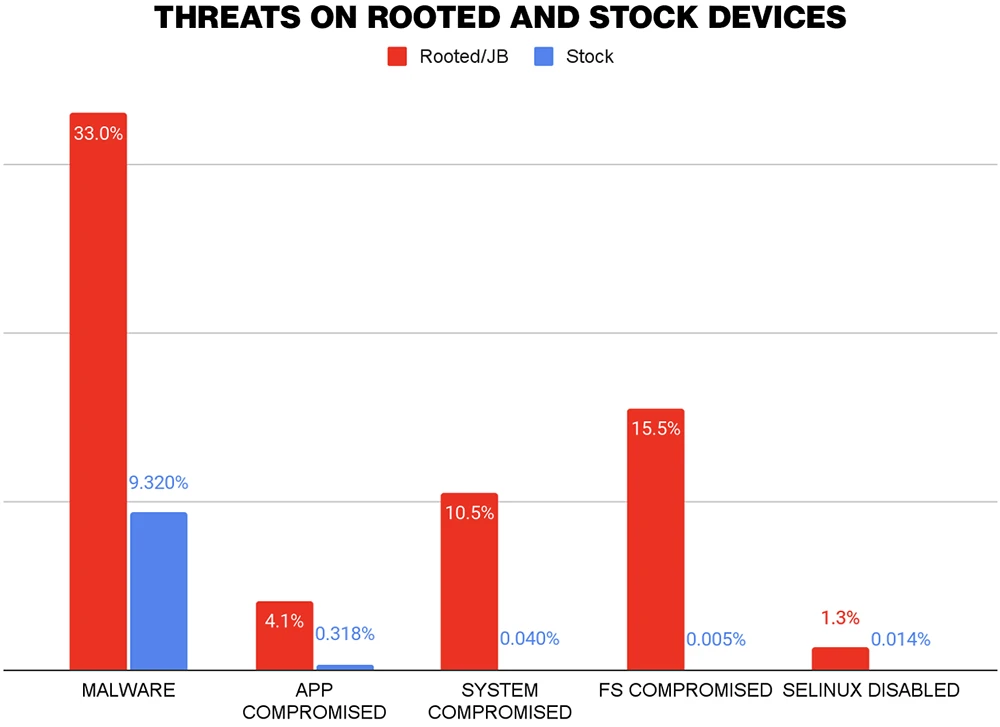
As cybercriminals have moved to a mobile-first attack strategy, rooting and jailbreaking mobile devices remain a powerful attack vector. Such…
AI Security Architect Verizon | USA | Hybrid – View job details As an AI Security Architect, you will ensure…
Veeam has released fixes for a critical remote code execution vulnerability (CVE-2025-23120) affecting its enterprise Veeam Backup & Replication solution,…
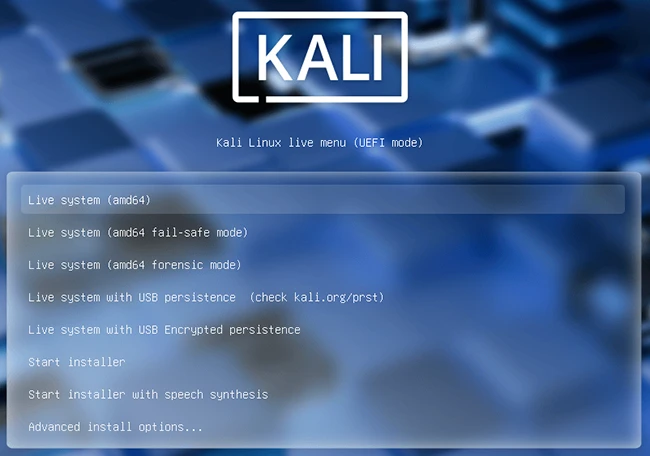
Kali Linux 2025.1a is now available. This release enhances existing features with improvements designed to streamline your experience. 2025 theme…
Long-lived plaintext credentials have been involved in most breaches over the last several years, according to GitGuardian. When valid credentials,…