Category: HelpnetSecurity
In this Help Net Security interview, Sunil Seshadri, EVP and CSO at HealthEquity, talks about the growing risks to healthcare…
Despite growing national security concerns and government restrictions, Chinese military-linked companies remain deeply embedded in the US digital supply chain,…
93% of organizations made policy changes over the preceding 12 months to address concerns about increased personal liability for CISOs,…
State-sponsored threat actors and cybercrime groups from North Korea, Iran, Russia, and China have been exploiting a zero-day Windows vulnerability…
GitGuardian’s State of Secrets Sprawl 2025 report shows no progress in combating secrets sprawl, with 23.8 million secrets leaked on…
1Kosmos announced 1Kosmos 1Key for shared account login environments. With FIDO-compliant biometric authentication, 1Kosmos 1Key addresses the pressing need for…
Keysight Technologies announces the expansion of its Keysight Vision Network Packet Brokers (NPBs), with the introduction of AI Insight Brokers….
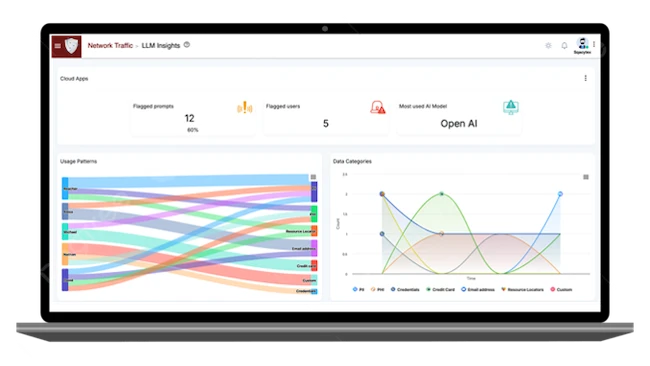
Cytex launched AICenturion, a LLM Firewall with Data Loss Prevention (DLP) capabilities. GenAI’s risks intensify as LLMs prevent enterprises from…
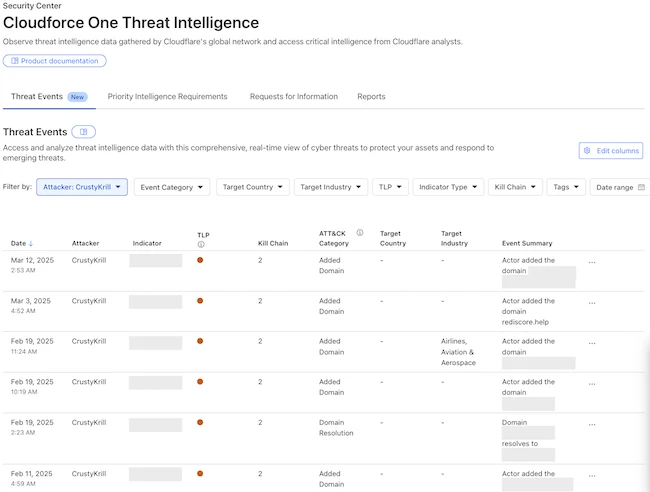
Cloudflare launched the Cloudforce One threat events platform to provide real-time intelligence on cyberattacks occurring across the Internet. Based on…
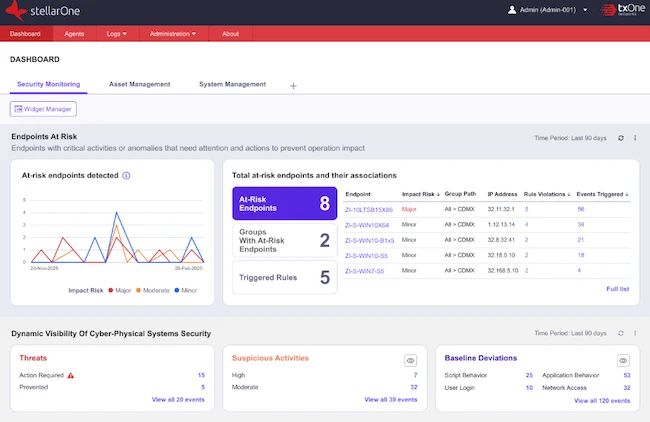
TXOne Networks announced Version 3.2 of its Stellar solution, further enhancing its capabilities from endpoint protection to more comprehensive detection…
Advanced Data Protection (ADP) secures iCloud data with end-to-end encryption. This ensures that no one, not even Apple, can access…
In this Help Net Security interview, William Booth, director, ATT&CK Evaluations at MITRE, discusses how CISOs can integrate regulatory compliance…