Category: HelpnetSecurity
Dependency-Check is an open-source Software Composition Analysis (SCA) tool to identify publicly disclosed vulnerabilities within a project’s dependencies. The tool…
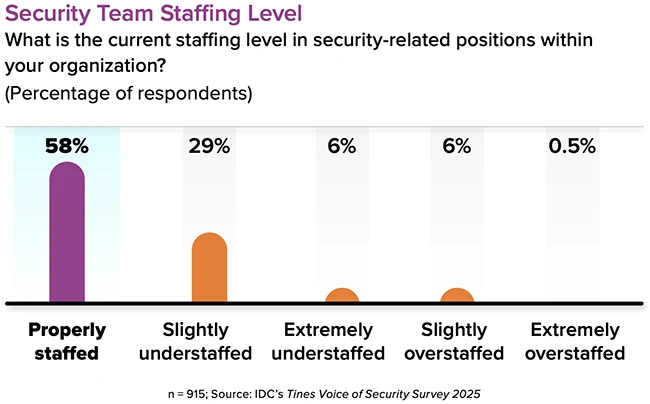
The contemporary SOC is transforming as it starts to realize the benefits of GenAI and utilize the manifestations of autonomous…
Google announced it has signed a definitive agreement to acquire Wiz for $32 billion, subject to closing adjustments, in an…
In this Help Net Security interview, Sunil Mallik, CISO of Discover Financial Services, discusses cybersecurity threats for financial institutions. He…
The growing sophistication of software supply chain attacks is driven by widespread flaws in open-source and third-party commercial software, along…
Application Security Expert monday.com | United Kingdom | Hybrid – View job details As an Application Security Expert, you will…
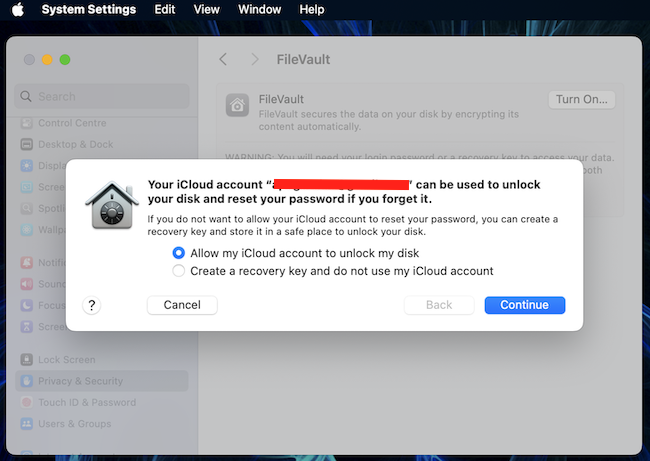
Encrypting files keeps sensitive data like personal details, finances, and passwords safe from attackers by making them unreadable to unauthorized…
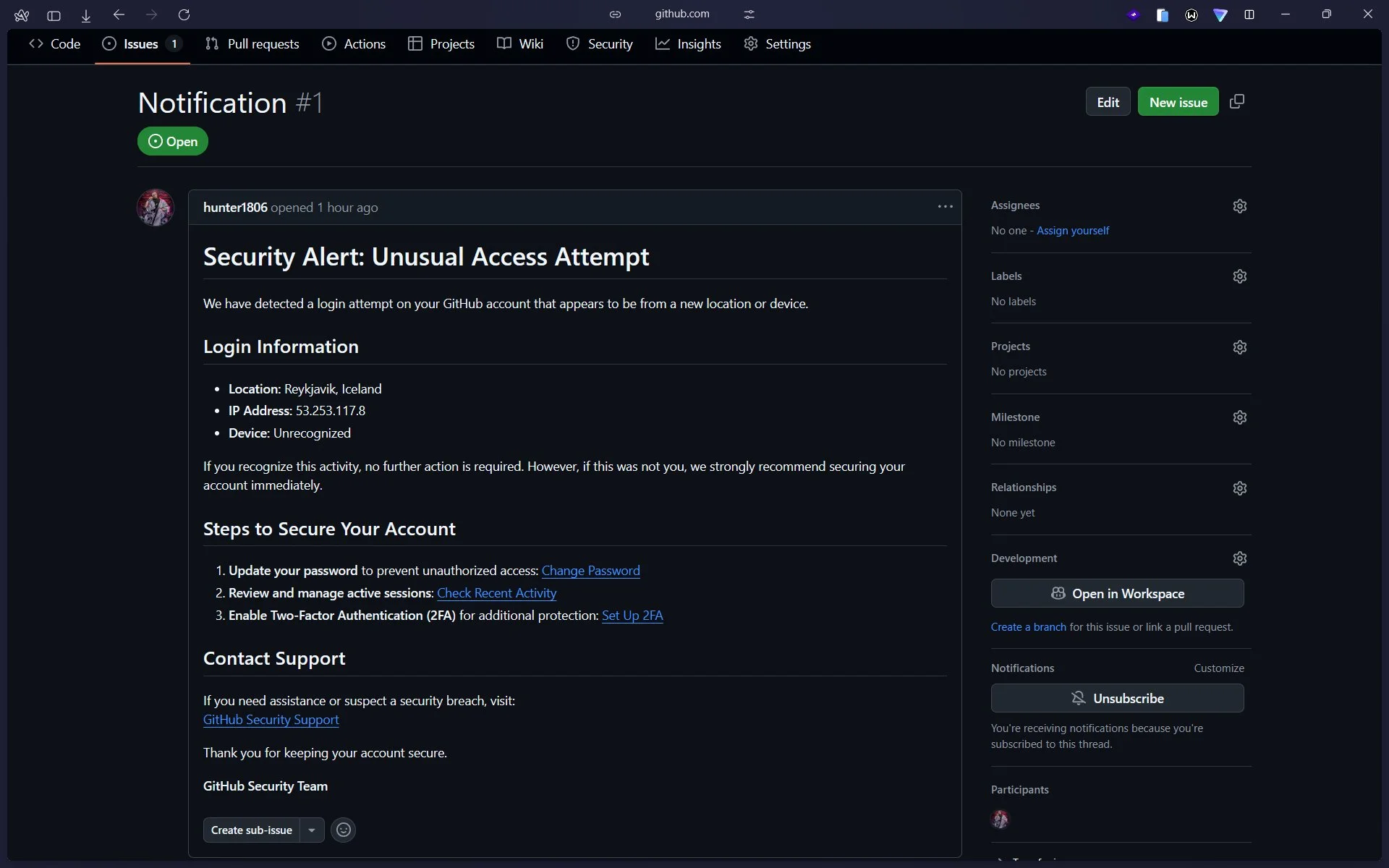
A phishing campaign targeting GitHub account owners has been trying to scare them with a fake security alert into allowing…
Packed with real-world case studies and practical examples, Cybersecurity Tabletop Exercises offers insights into how organizations have successfully leveraged tabletop…
IntelMQ is an open-source solution designed to help IT security teams (including CERTs, CSIRTs, SOCs, and abuse departments) streamline the…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: NIST selects HQC as backup…
In this Help Net Security interview, Mir Kashifuddin, Data Risk & Privacy Leader at PwC, discusses how CISOs can translate…