Category: HelpnetSecurity
Cyber threats in 2025 require a proactive, adaptive approach. To stay ahead, CISOs must balance technical defenses, regulatory expectations, and…
A recent report from Nozomi Networks Labs, based on an analysis of over 500,000 wireless networks worldwide, reveals that only…
Here’s a look at the most interesting products from the past week, featuring releases from Alloy, Detectify, Pondurance, and SimSpace….
When it comes to safeguarding your privacy online, most people focus on securing passwords, encrypting communications, and clearing browsing history….
The adoption of connected medical devices, collectively called the Internet of Medical Things (IoMT), has transformed patient care. However, this…
Cybersecurity constantly evolves, but some books have stood the test of time, shaping how professionals think about security, risk, and…
Cloud Security Engineer TUI Group | Portugal | Hybrid – View job details As a Cloud Security Engineer, you will…
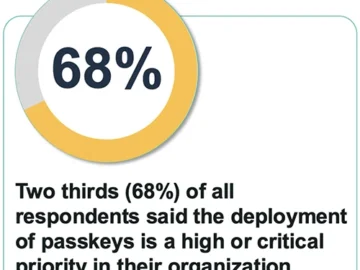
87% of companies have, or are in the midst of, rolling out passkeys with goals tied to improved user experience,…
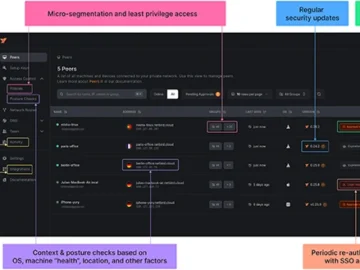
NetBird is an open-source solution that integrates a configuration-free peer-to-peer private network with centralized access control, providing a single platform…
Cybersecurity is a high-stakes, high-pressure field in which CISOs and their teams constantly battle threats, compliance requirements, and business expectations….
As AI technology advances, cybercriminals create more personalized and convincing scams. This includes mimicking voices, deepfake videos, and highly convincing…
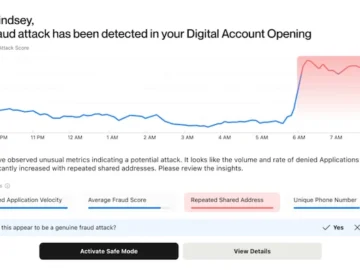
Alloy launched Fraud Attack Radar, a machine learning-powered solution that provides financial institutions (FIs) and fintechs with actionable intelligence on…