Category: HelpnetSecurity
The growth of AI-based technology has introduced new challenges, making remote identity verification systems more vulnerable to attacks, according to…
QR codes have become an integral part of our everyday life due to their simplicity. While they’ve been around for…
Commix is an open-source penetration testing tool designed to automate the detection and exploitation of command injection vulnerabilities, streamlining security…
The Chief AI Officer’s Handbook is a comprehensive resource for professionals navigating AI implementation and strategy. It is particularly valuable…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Massive botnet hits Microsoft 365…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Massive botnet hits Microsoft 365…
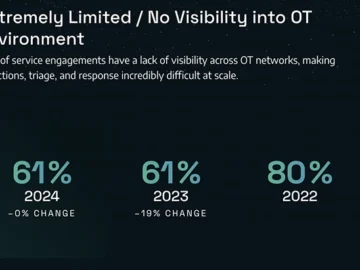
Ransomware attacks against industrial organizations surged by 87% over the past year, while new malware families designed specifically for OT…
Users of the MITRE Caldera cyber security platform have been urged to plug a critical hole (CVE-2025–27364) that may allow…
In this Help Net Security interview, David Dumont, Partner at Hunton Andrews Kurth, discusses the implications of the EU AI…
Here’s a look at the most interesting products from the past month, featuring releases from: 1Password, Armor, BigID, Dynatrace, Fortinet,…
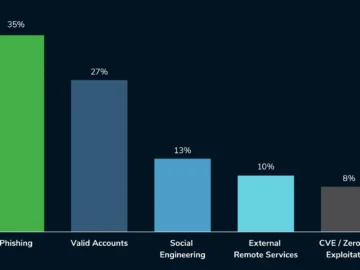
Phishing has been the method most often employed by cybercriminals to achieve initial access to targeted organizations in 2024, according…
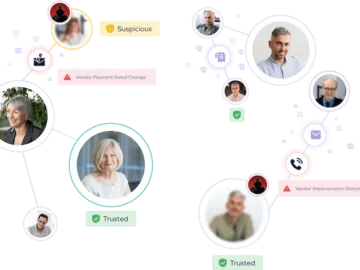
Trustmi announced new Behavioral AI, anomaly detection, and risk-scoring capabilities to help enterprise customers combat social engineering attacks on their…