Category: HelpnetSecurity
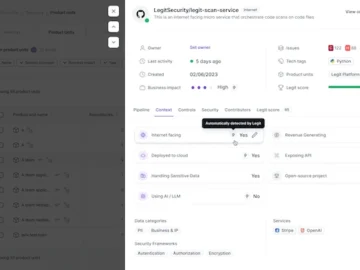
By providing full context around both the application and the development environment, Legit’s ASPM platform empowers CISOs and their team…
In this Help Net Security interview, Marina Segal, CEO at Tamnoon, discusses the most significant obstacles when implementing managed cloud…
CISOs are constantly navigating the challenge of protecting their organizations while ensuring business agility and innovation. For example, as companies…
Application Security Engineer Binance | UAE | Remote – View job details As a Application Security Engineer, you will enhance…
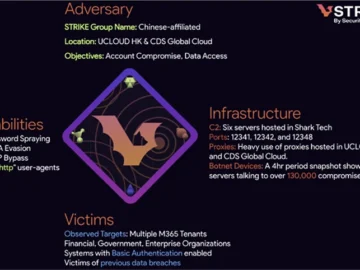
A recently discovered botnet of over 130,000 compromised devices is launching coordinated password-spraying attacks against Microsoft 365 (M365) accounts. Security…
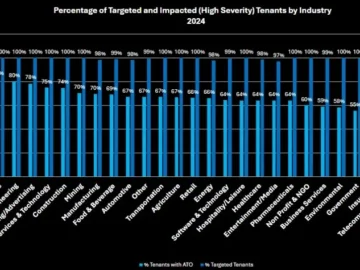
Account takeover (ATO) is one of the most prevalent attack types; Proofpoint says that in 2024, 99% of the customer…
In this Help Net Security interview, Aaron Roberts, Director at Perspective Intelligence, discusses how automation is reshaping threat intelligence. He…
Misconfig Mapper is an open-source CLI tool built in Golang that discovers and enumerates instances of services used within your…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: A PostgreSQL zero-day was also…
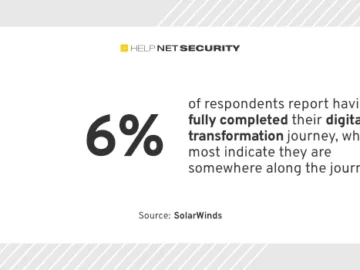
For most public sector organizations, digital transformation is a work in progress, with the complexity of integrating new systems and…
In this Help Net Security interview, Chester Wisniewski, Director and Global Field CISO at Sophos, discusses the shifting ransomware landscape,…
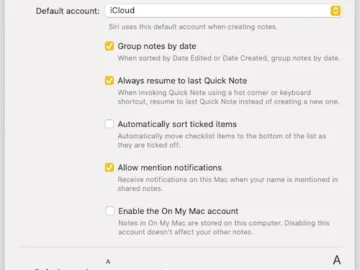
Apple allows you to lock your notes using your iPhone passcode or a separate password, ensuring your private information stays…