Category: HelpnetSecurity
Edge Delta announced its Security Data Pipelines. This solution empowers security teams to process, analyze, and act on security data…
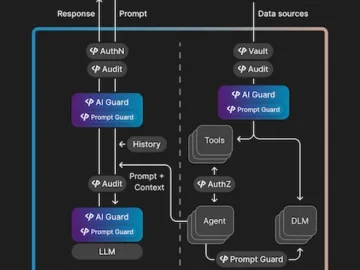
Pangea announced AI Guard and Prompt Guard to secure AI, defending against threats like prompt injection and sensitive information disclosure….
Kunai is an open-source tool that provides deep and precise event monitoring for Linux environments. “What sets Kunai apart is…
Cybersecurity advice is everywhere. We’re constantly reminded to update our passwords, enable two-factor authentication, and avoid clicking suspicious links. Yet,…
BlackLock is on track to become the most active ransomware-as-a-service (RaaS) outfit in 2025, according to ReliaQuest. Its success is…
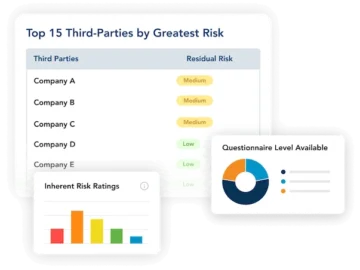
ProcessUnity announced the next generation of the Global Risk Exchange. This platform transforms the third-party assessment process, reducing friction for…
In this Help Net Security, Oded Hareven, CEO of Akeyless Security, discusses how enterprises should adapt their cybersecurity strategies to…
Airport Cybersecurity Engineer II Salt Lake City Corporation | USA | On-site – View job details As an Airport Cybersecurity…
Discover the top Open-Source Intelligence (OSINT) books in this curated list. From investigative techniques to digital footprint analysis, these titles…
The suspected Chinese state-sponsored hackers who breached workstations of several US Treasury employees in December 2024 did so by leveraging…
In this Help Net Security interview, Natalia Belaya, CISO at Cloudera, discusses common misconceptions about cloud security, the balance between…
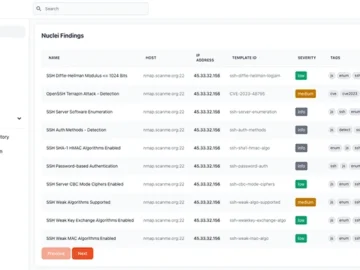
Orbit is an open-source platform built to streamline large-scale Nuclei scans, enabling teams to manage, analyze, and collaborate on security…