Category: HelpnetSecurity
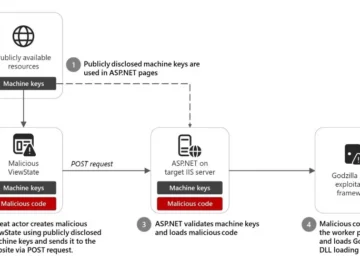
A ViewState code injection attack spotted by Microsoft threat researchers in December 2024 could be easily replicated by other attackers,…
The way we manage digital identity is fundamentally broken. The root of the problem lies in traditional, centralized identity models,…
NSA’s Research Directorate released version 11.3 of Ghidra, an open-source software reverse engineering (SRE) framework. It offers advanced analysis tools,…
The implementation of new regulatory measures that impact the UK, EU, and beyond are driving organizations to enhance vigilance in…
Cyber fraud (which includes activity such as hacking, deepfakes, voice cloning and highly sophisticated phishing schemes) rose by 14% year…
Here’s a look at the most interesting products from the past week, featuring releases from Dynatrace, Nymi, Qualys, SafeBreach, and…
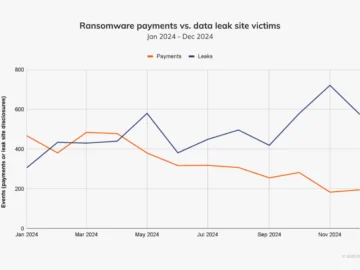
Chainalysis’ latest report on how the ransomware landscape changed from 2023 to 2024 shows a promising trend: An increasing number…
Apple’s Safari browser includes several features aimed at enhancing privacy while browsing the web. Two of the most notable privacy…
In this Help Net Security interview, Oliver Friedrichs, CEO at Pangea, discusses why strong data hygiene is more important than…
AI is driving significant changes in attack sources, with 88% of enterprises observing an increase in AI-powered bot attacks in…
XE Group, a cybercriminal outfit that has been active for over a decade, has been quietly exploiting zero-day vulnerabilities (CVE-2025-25181,…
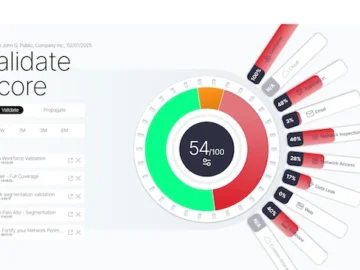
SafeBreach launched SafeBreach exposure validation platform, which combines the power of its time-tested breach and attack simulation (BAS) product—now called…